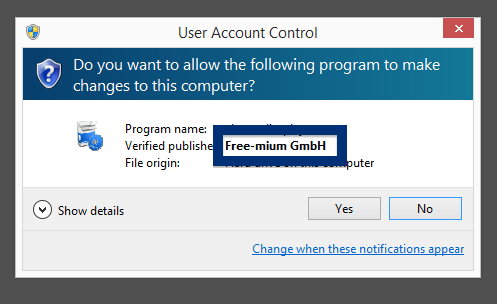
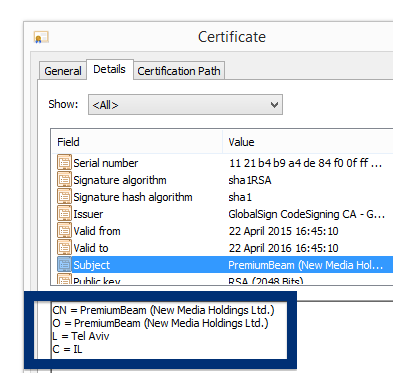
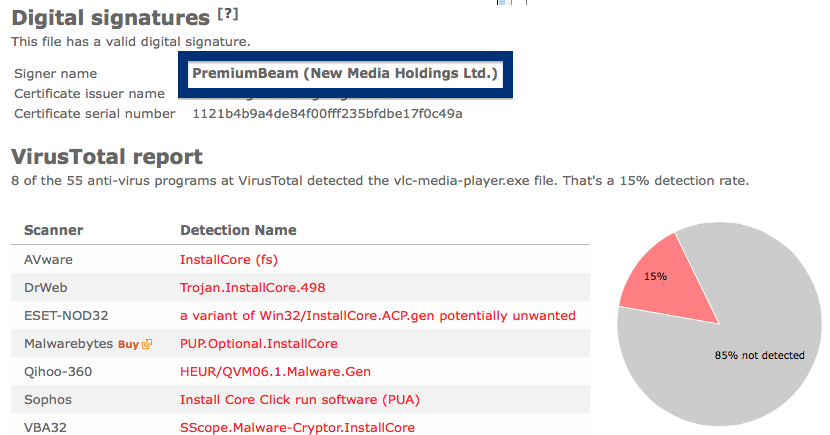
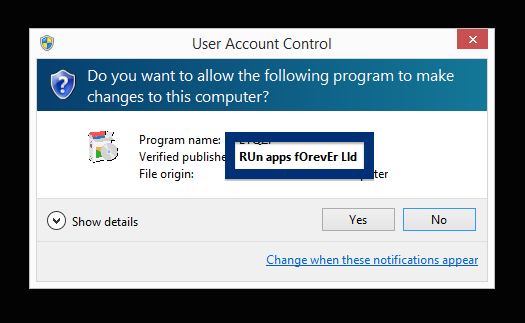
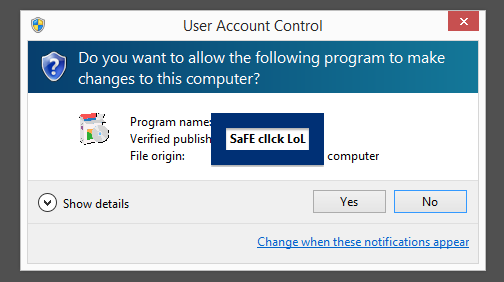
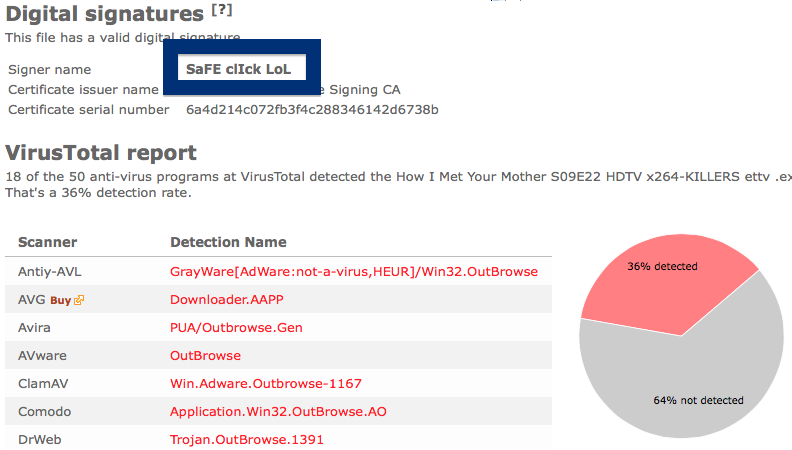
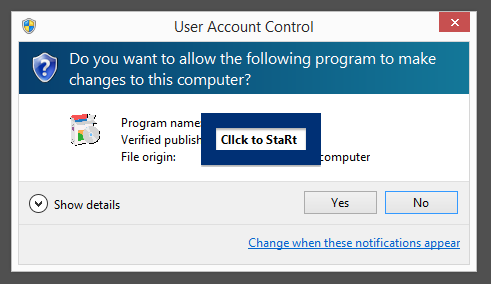
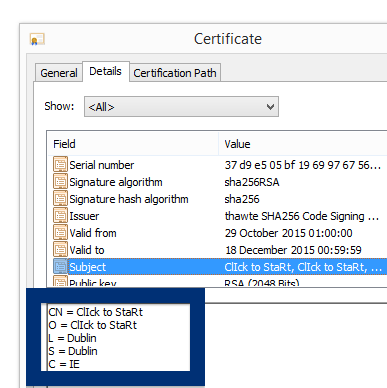
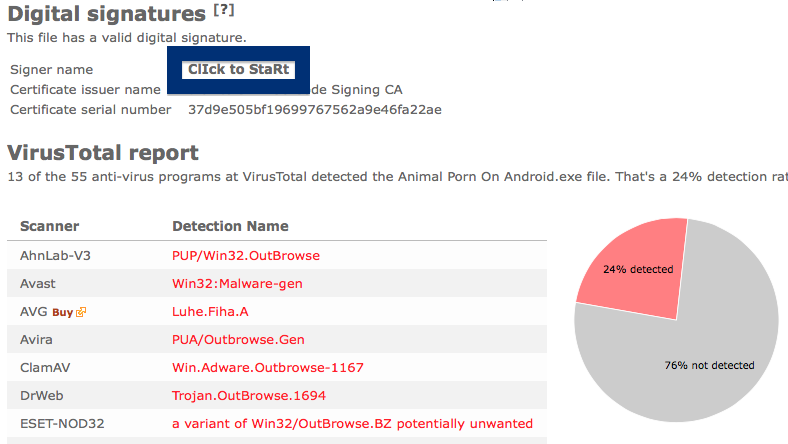
Hello! Just a note on a publisher called Free-mium GmbH. The Free-mium GmbH download – vlc-media-player.exe – was detected when I uploaded it to VirusTotal. Did you also find a download by Free-mium GmbH? Was it also detected when you uploaded it to VirusTotal?
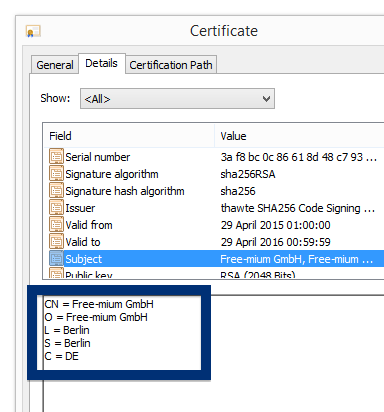
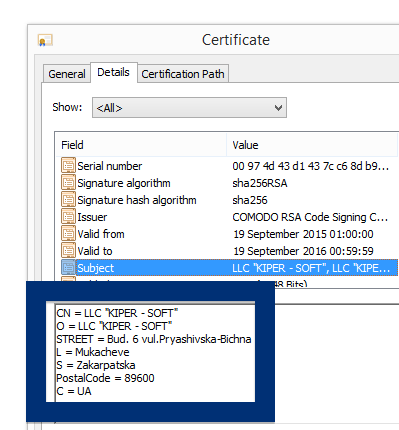
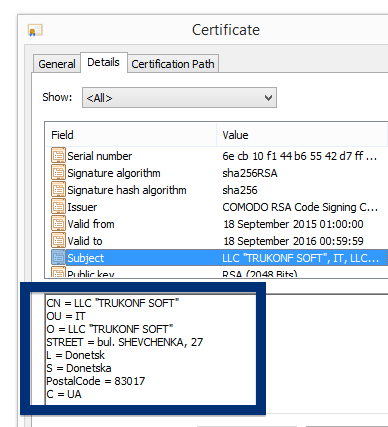
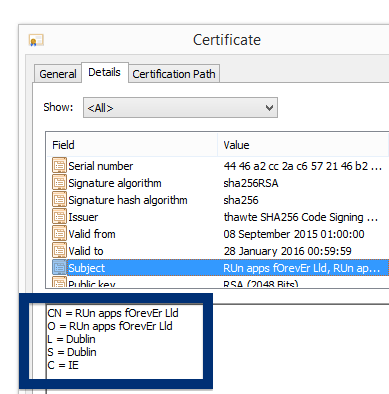
By looking at the certificate we can see that Free-mium GmbH appears to be located in Berlin, Germany.
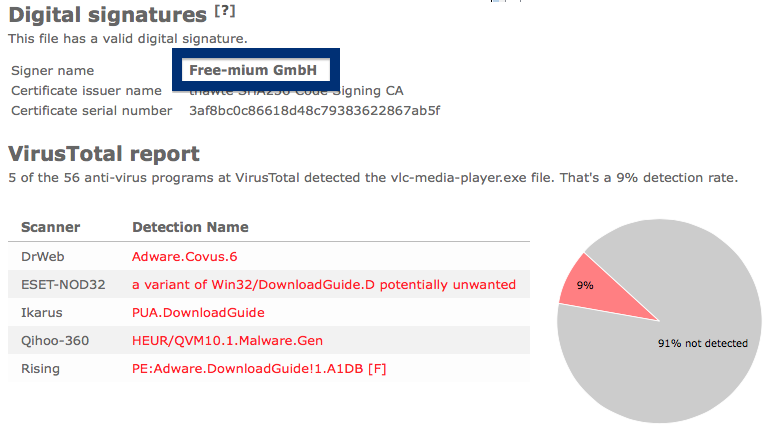
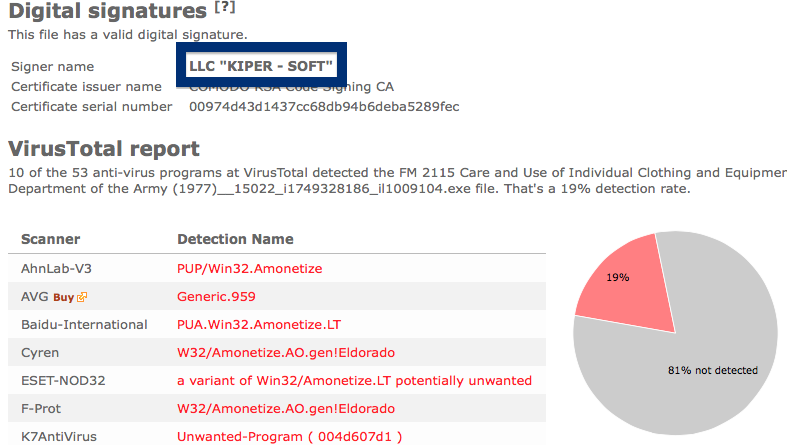
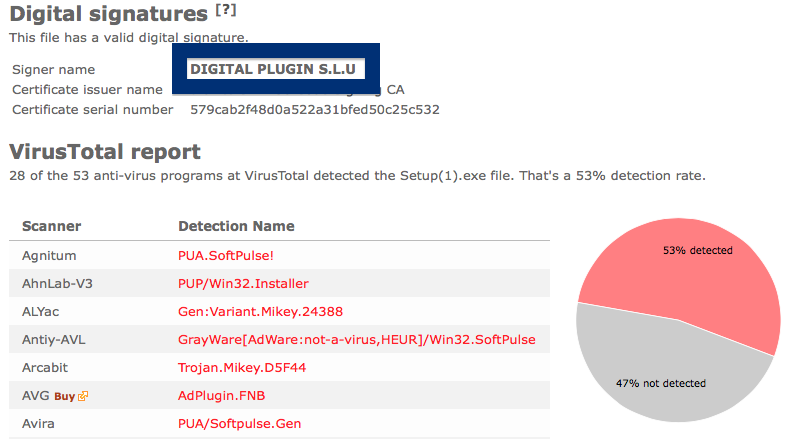
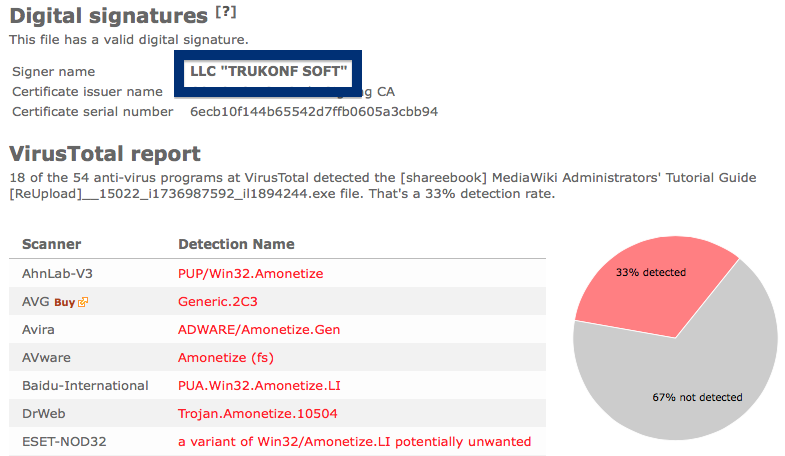
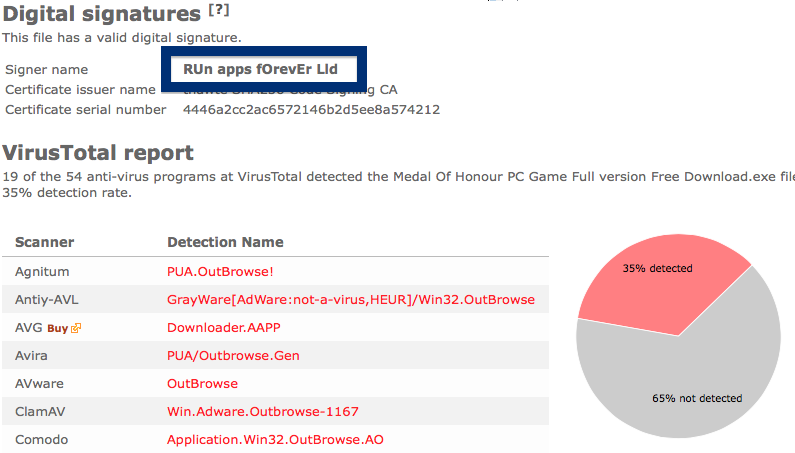
The scan result from VirusTotal below clearly shows why you probably should avoid the Free-mium GmbH file. The file is not the official VLC player, but detected under names such as Adware.Covus.6, a variant of Win32/DownloadGuide.D potentially unwanted, PUA.DownloadGuide and PE:Adware.DownloadGuide!1.A1DB [F].
If you want to download the official VLC player, you can do so from videolan.org.
Did you also find a file digitally signed by Free-mium GmbH? What kind of download was it and where did you find it?
Thank you for reading.