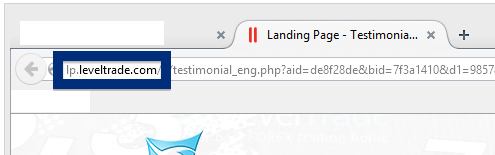
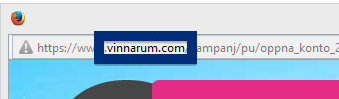
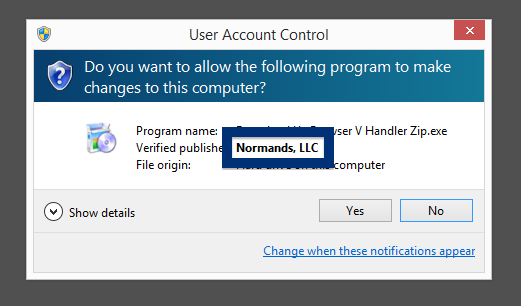
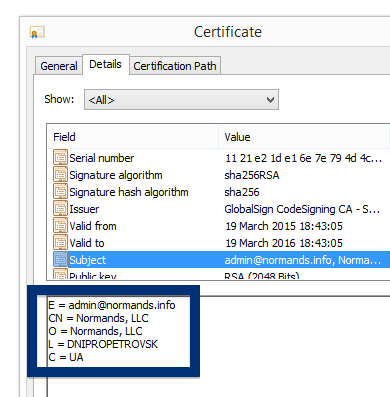
This page shows how to remove ib.adnxs.com from Mozilla Firefox, Google Chrome and Internet Explorer.
Does this sound familiar? You see ib.adnxs.com in your browser’s status bar while browsing web sites that generally don’t load any content from third party domains. Perhaps the ib.adnxs.com domain appear when performing a search at the Google search engine?
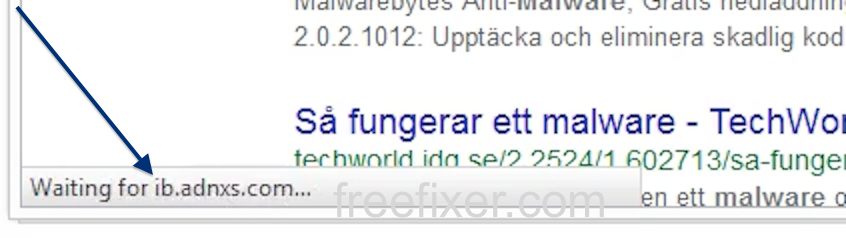
Here’s a screenshot of ib.adnxs.com when it showed up on my computer:
(I know, lots of watermarks. Have to do it to stop the copy-cats.)
The following are some of the status bar messages you may see in your browser’s status bar:
- Waiting for ib.adnxs.com…
- Transferring data from ib.adnxs.com…
- Looking up ib.adnxs.com…
- Read ib.adnxs.com
- Connected to ib.adnxs.com…
If this description sounds like what you are seeing, you presumably have some potentially unwanted program installed on your system that makes the ib.adnxs.com domain appear in your browser. Contacting the owner for the site you were at would be a waste of time. The ib.adnxs.com statusbar messages are not coming from them. I’ll do my best to help you with the ib.adnxs.com removal in this blog post.
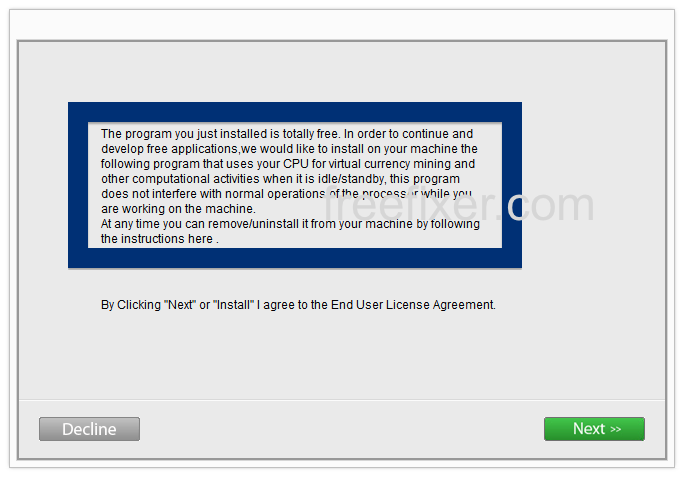
I found ib.adnxs.com on one of the lab systems where I have some potentially unwanted programs running. I’ve talked about this in some of the previous blog posts. The potentially unwanted programs was installed on purpose, and from time to time I check if something new has appeared, such as pop-up windows, new tabs in the browsers, injected ads on web site that usually don’t show ads, or if some new files have been saved to the hard-drive.
ib.adnxs.com was registered on 2008-05-27. ib.adnxs.com resolves to the 68.67.153.211 address. adnxs.net is located on the same IP.
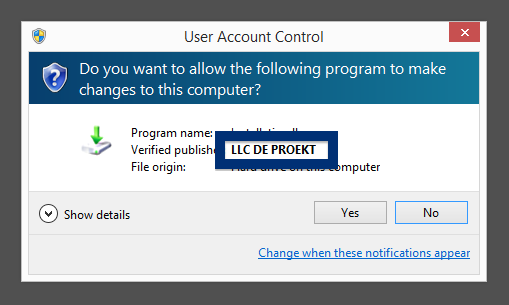
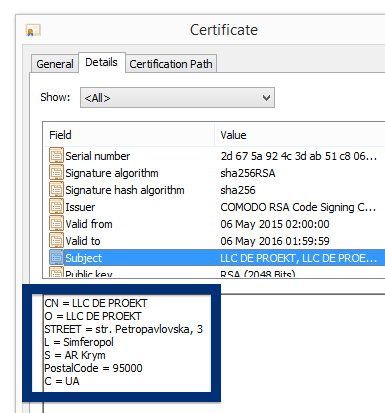
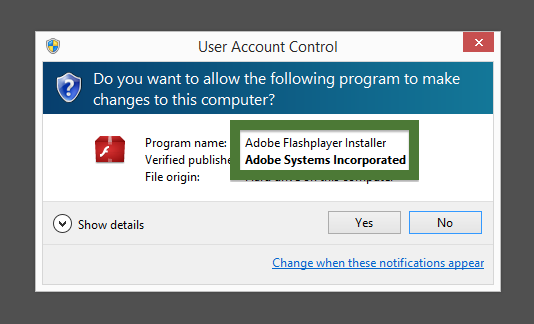
So, how do you remove ib.adnxs.com from your browser? On the machine where ib.adnxs.com showed up in the status bar I had YouTubeAdBlocke, SalePlus and IStart 5.3.7 installed. I removed them with FreeFixer and that stopped the browser from loading data from ib.adnxs.com.
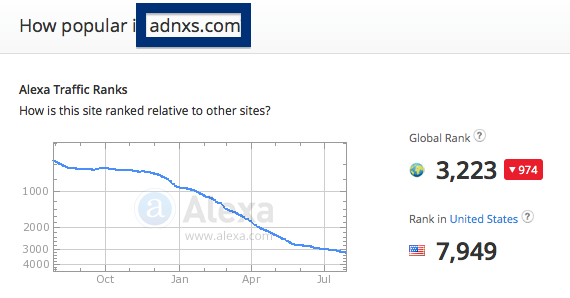
Judging from Alexa’s traffic rank, ib.adnxs.com is getting quite a lot of traffic:
The bad news with this type of status bar message is that it can be caused by many variants of potentially unwanted programs, not just the potentially unwanted program that’s installed on my system. This makes it impossible to say exactly what you need to remove to stop the status bar messages.
Anyway, here’s my suggestion for the ib.adnxs.com removal:
The first thing I would do to remove ib.adnxs.com is to examine the programs installed on the machine, by opening the “Uninstall programs” dialog. You can open this dialog from the Windows Control Panel. If you are using one of the more recent versions of Windows OS you can just type in “uninstall” in the Control Panel’s search field to find that dialog:
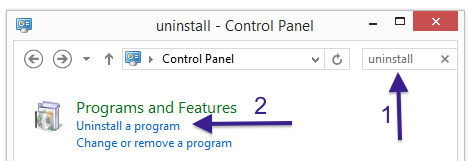
Click on the “Uninstall a program” link and the Uninstall programs dialog will open up:
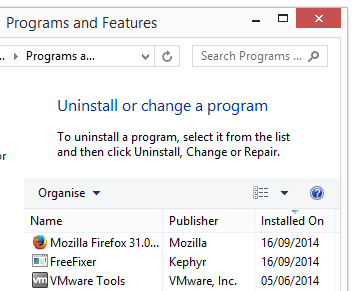
Do you see something suspicious in there or something that you don’t remember installing? Tip: Sort on the “Installed On” column to see if something was installed approximately about the same time as you started seeing the ib.adnxs.com statusbar messages.
Then I would check the web browser add-ons. Potentially unwanted programs often show up under the add-ons menu in Google Chrome, Mozilla Firefox, Internet Explorer, Safari or Opera. Is there something that looks suspicious? Something that you don’t remember installing?
I think you will be able to identify and uninstall the potentially unwanted program with the steps outlined above, but in case that did not work you can try the FreeFixer removal tool to identify and remove the potentially unwanted program. FreeFixer is a freeware tool that I started develop many years ago. Freefixer is a tool built to manually track down and uninstall unwanted software. When you’ve identified the unwanted files you can simply tick a checkbox and click on the Fix button to remove the unwanted file.
FreeFixer’s removal feature is not crippled like many other removal tools out there. It will not require you to purchase the program just when you are about to remove the unwanted files.
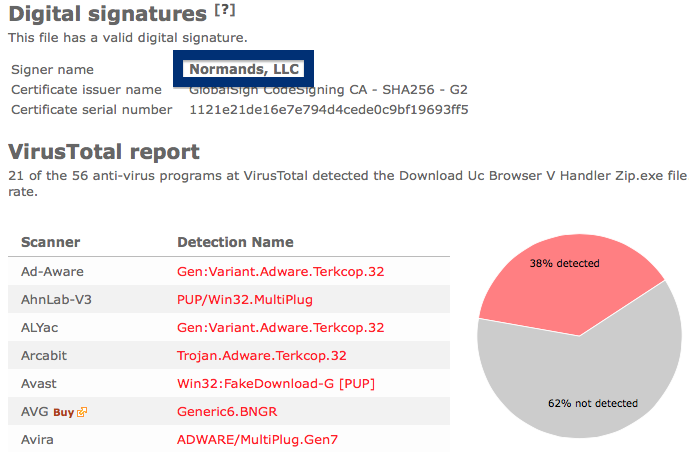
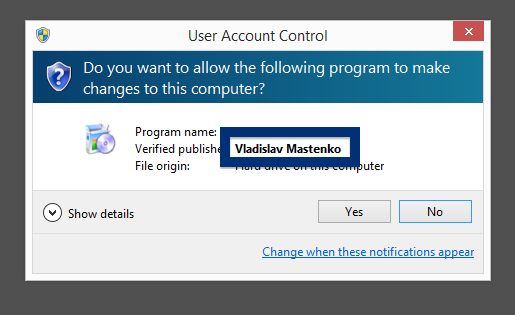
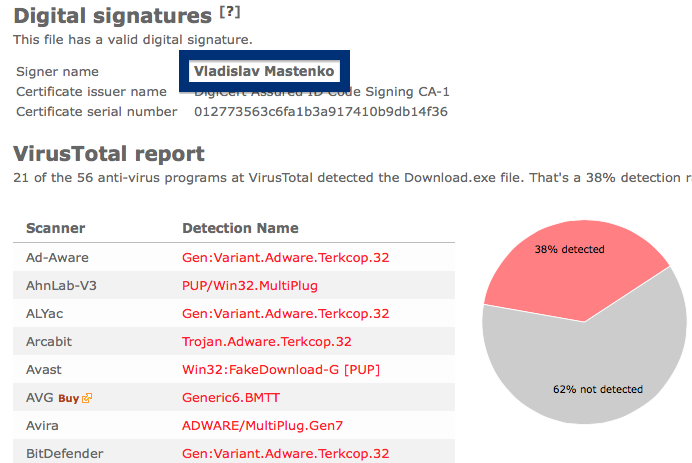
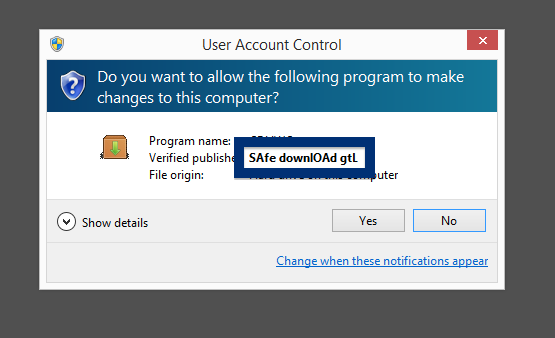
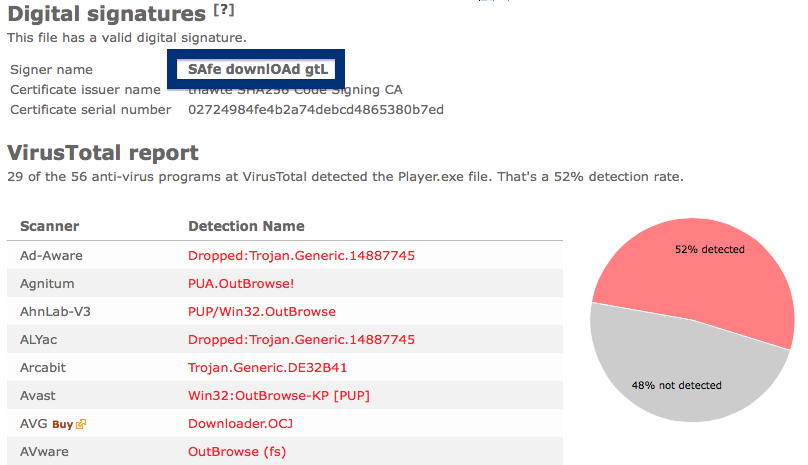
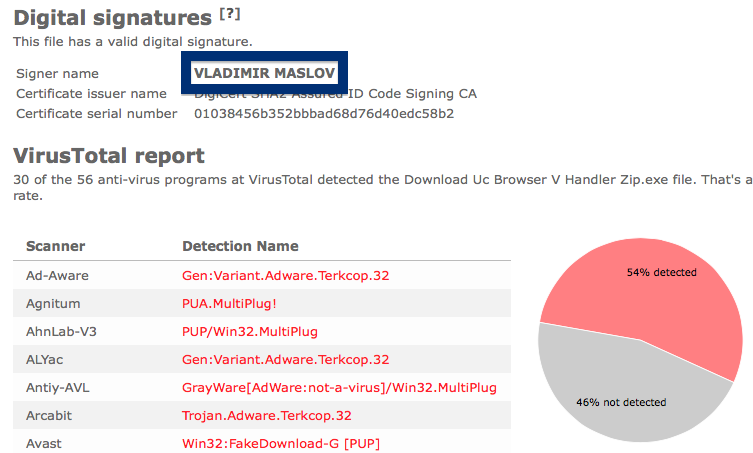
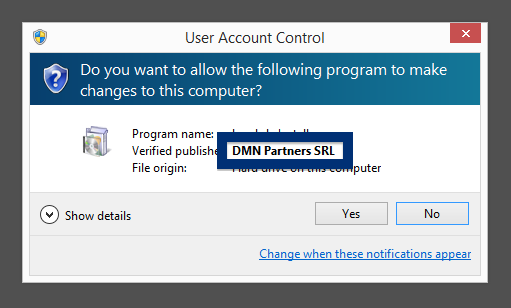
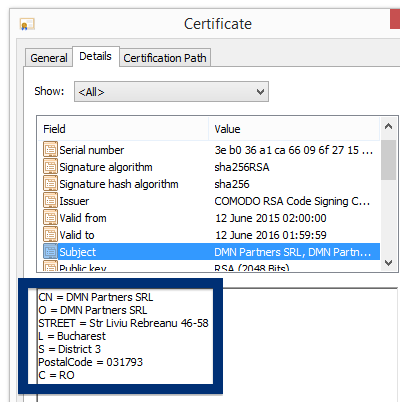
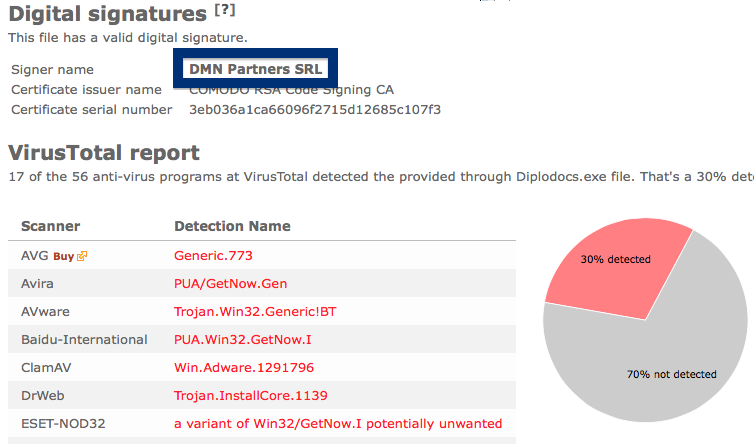
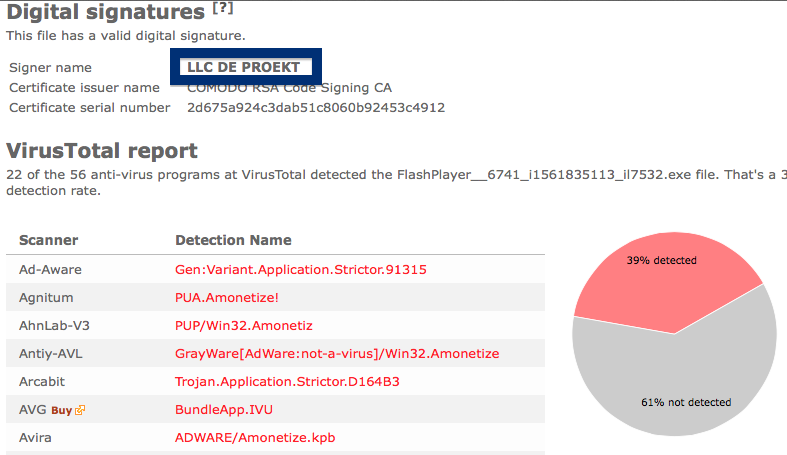
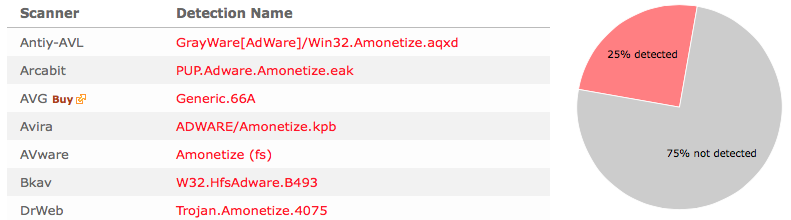
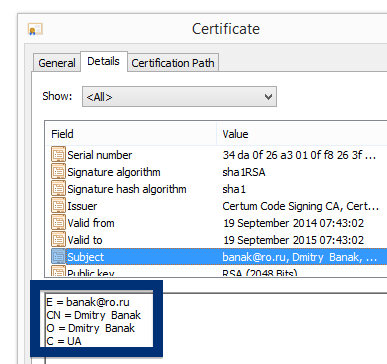
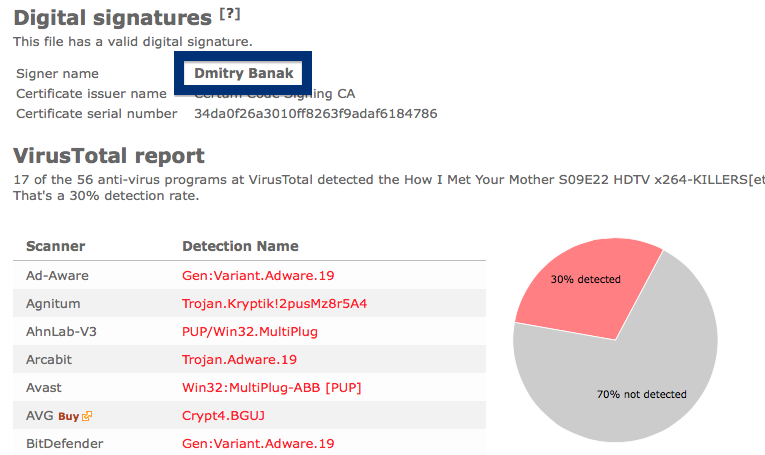
And if you’re having a hard time determining if a file is safe or potentially unwanted in the FreeFixer scan result, click on the More Info link for the file. That will open up your browser with a page which contains additional information about the file. On that web page, check out the VirusTotal report which can be very useful:

Did this blog post help you to remove ib.adnxs.com? Please let me know or how I can improve this blog post.
Thank you!