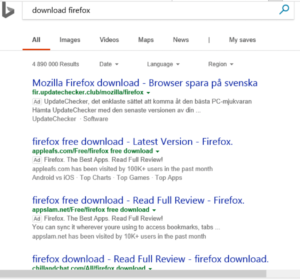
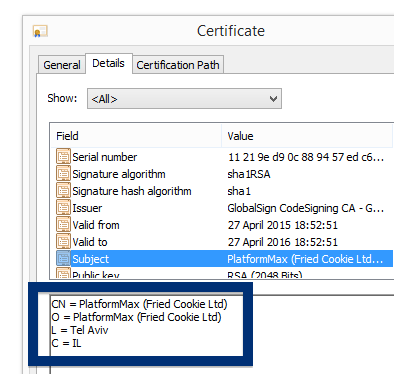
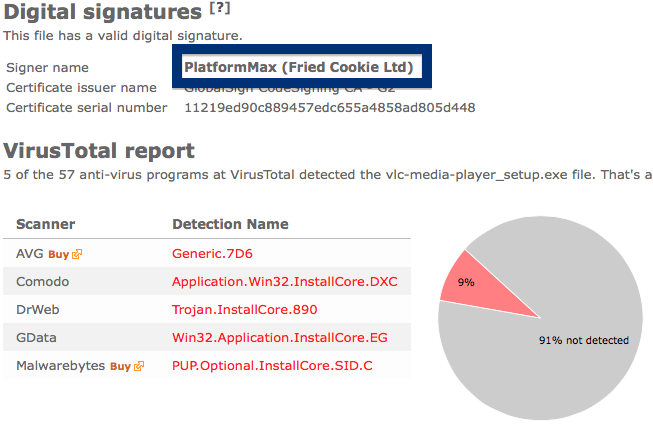
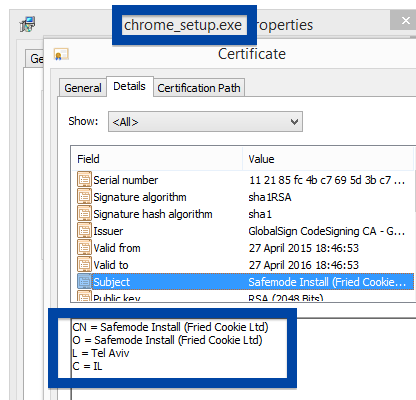
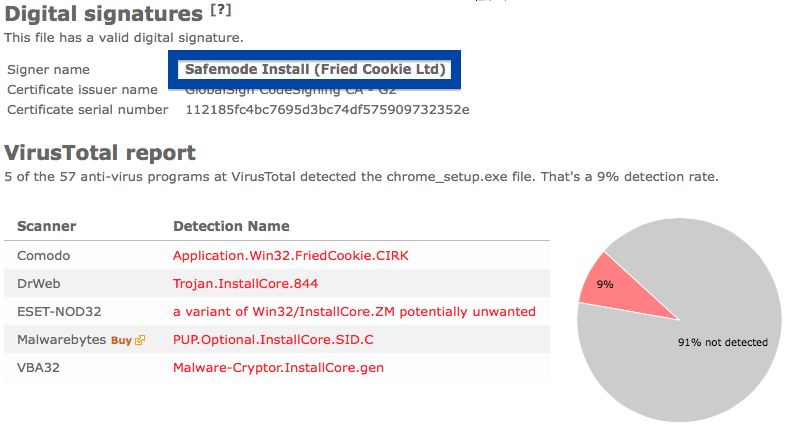
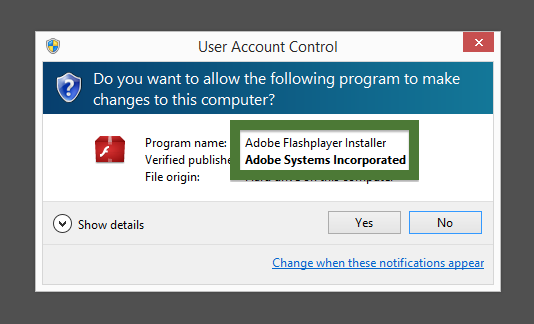
Something that always bugged me is some of the content promoted by search engine ads. I’m talking about the ads that appear at the top of the search results. Here’s an example where I search for “download firefox” on the Bing search engine:
The first four items above the fold are ads. Let’s click on the first ad (fir.updatechecker.club).
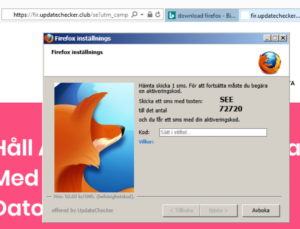
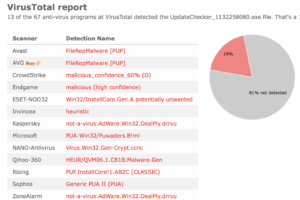
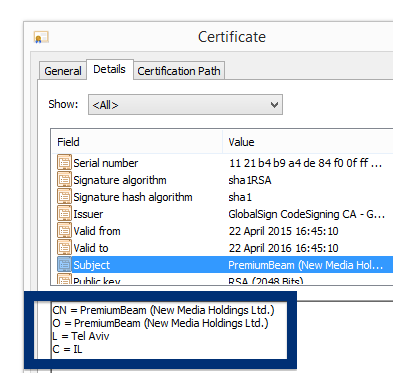
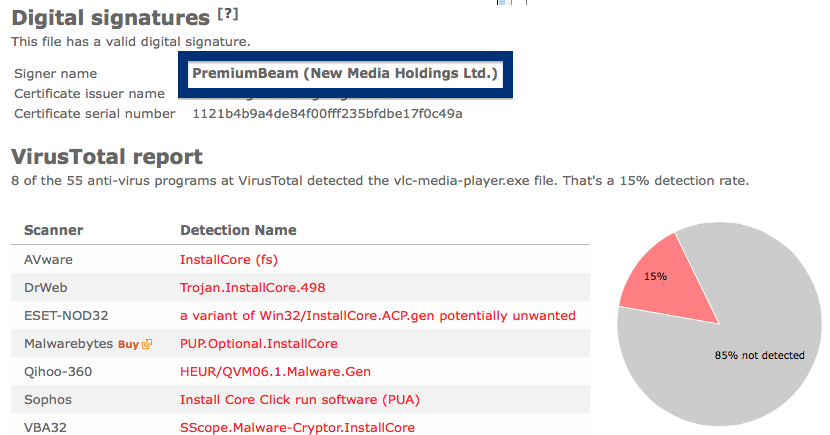
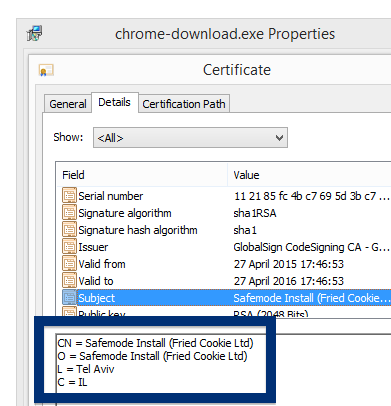
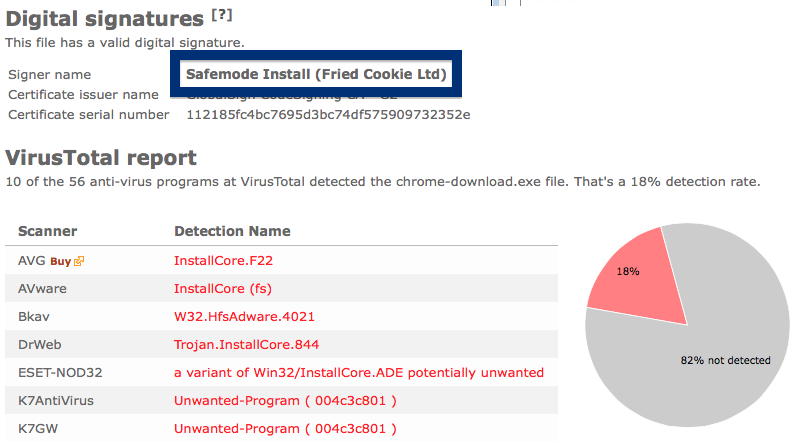
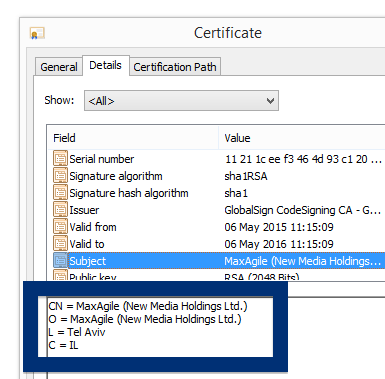
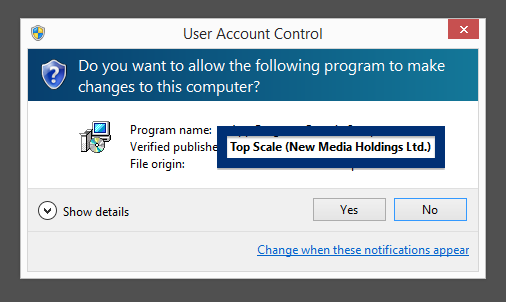
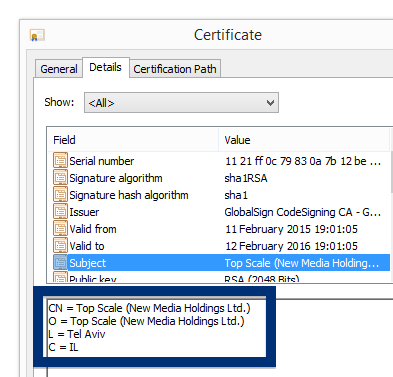
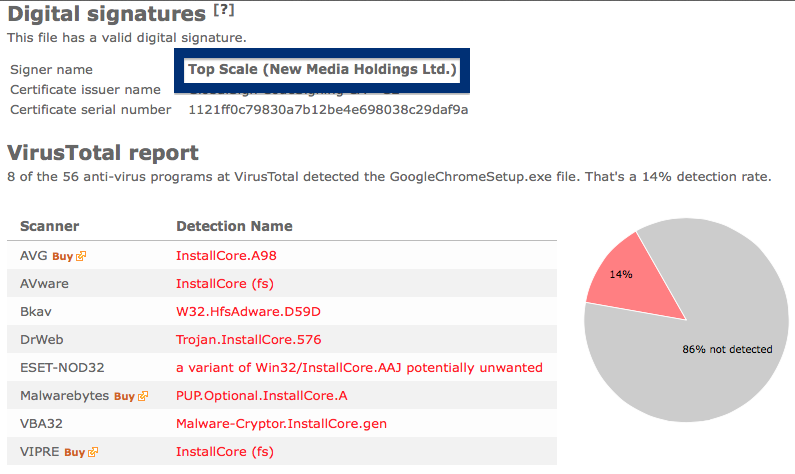
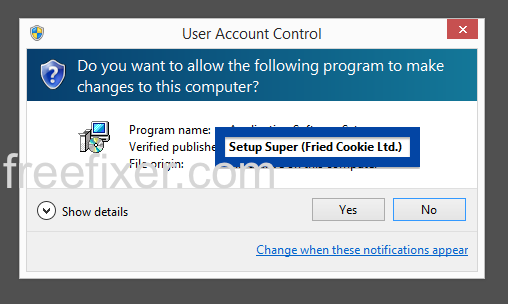
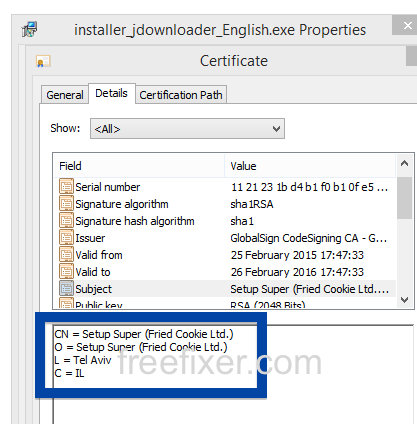
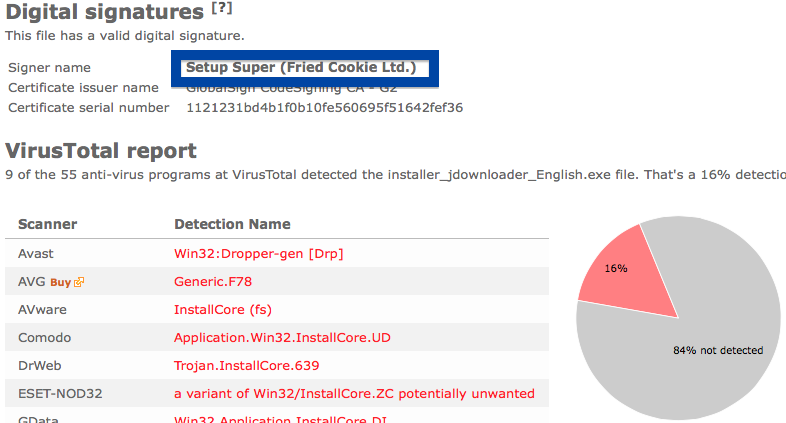
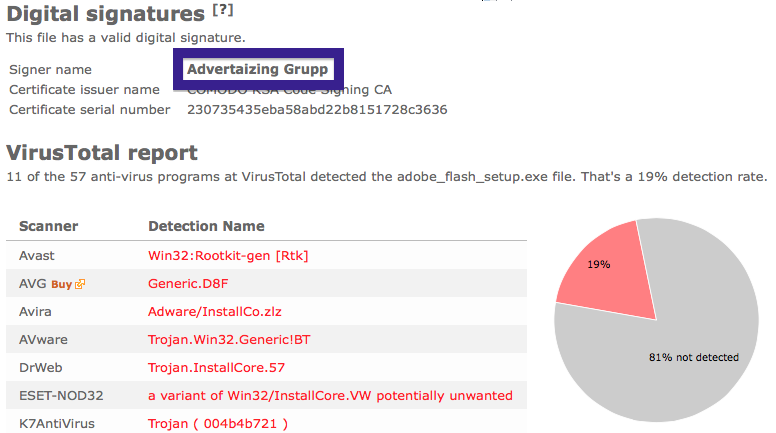
The fir.updatechecker.club web site shows a faked Windows GUI pretending to be the Firefox Installer (built inside the browser’s viewport) and they want me to pay 50 SEK to install the free Mozilla Firefox browser by sending an SMS! The fact that 50 SEK is charged when sending the SMS appears with a small font in grey in the lower left corner. When refusing to pay 50 SEK I get an setup file, which is detected by many of the security scanners:
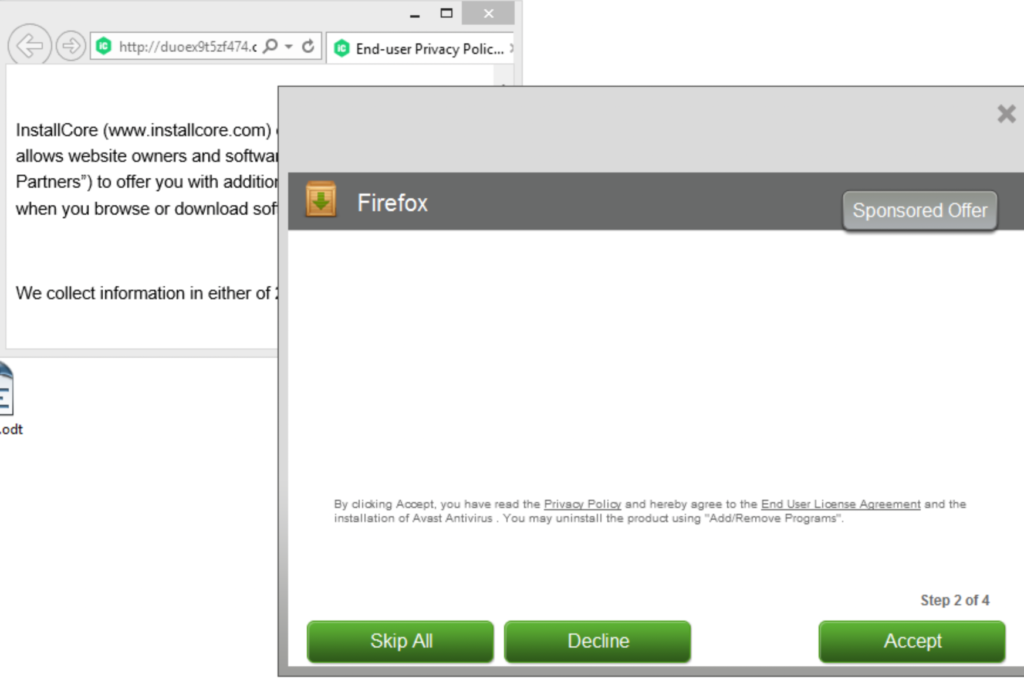
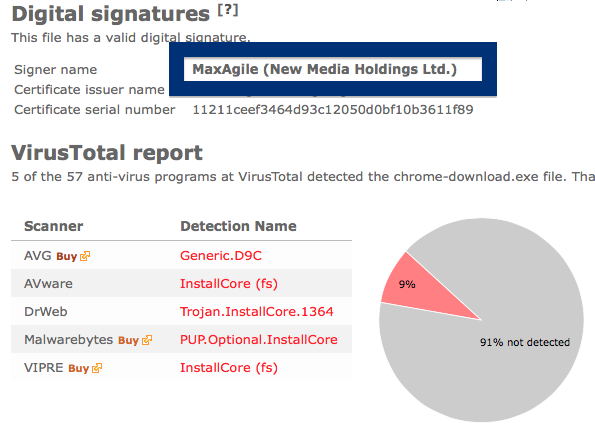
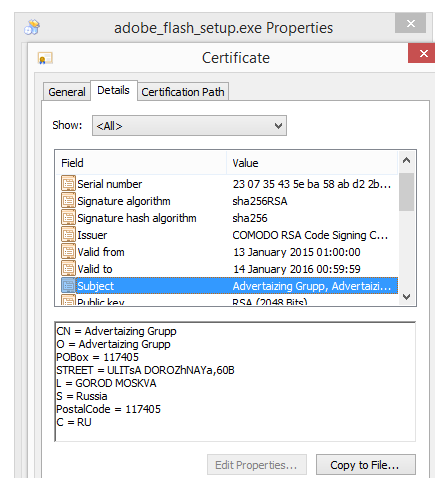
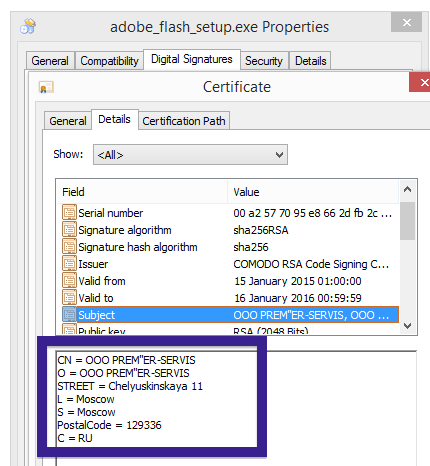
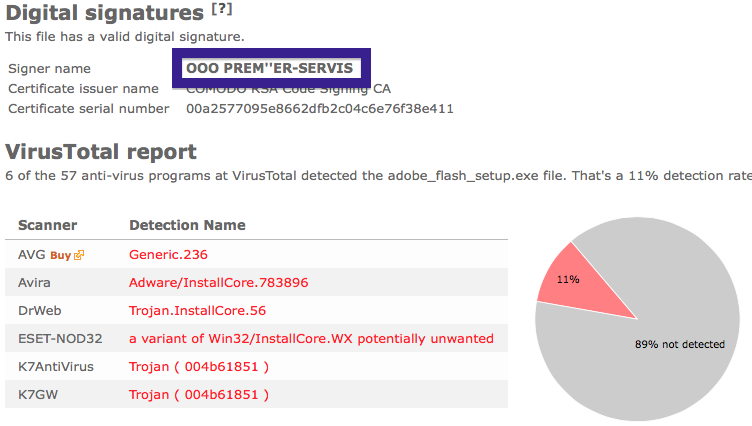
The installer appears to be build using InstallCore and shows a sponsored offer to install Avast AntiVirus, which I declined. (Though it would be interesting to see if Avast would go ahead and remove the bundler. As you can see in the scan result above, Avast is detecting the installer file, giving it the detection name “FileRepMalware [PUP]”).
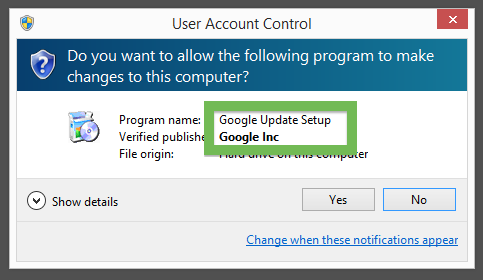
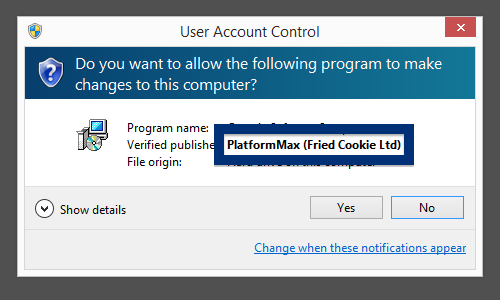
The installer file also installs a piece of software called UpdateChecker:
Should Bing block these ads? What do you think?