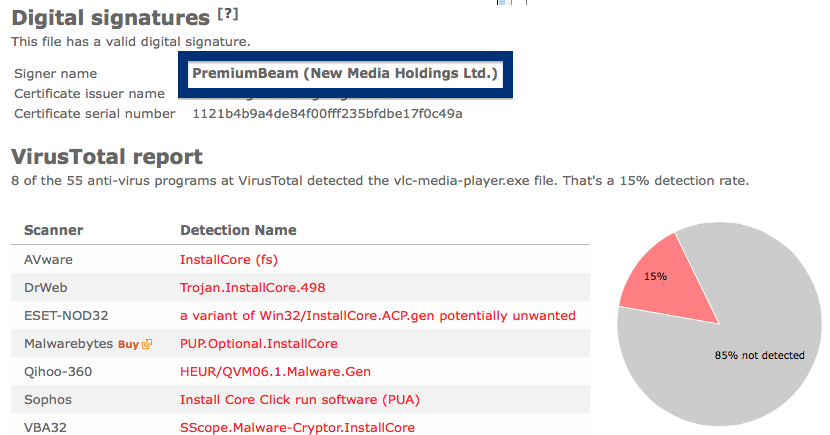
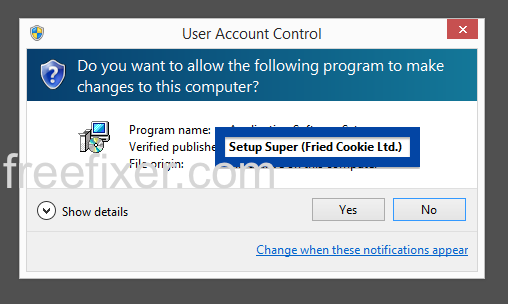
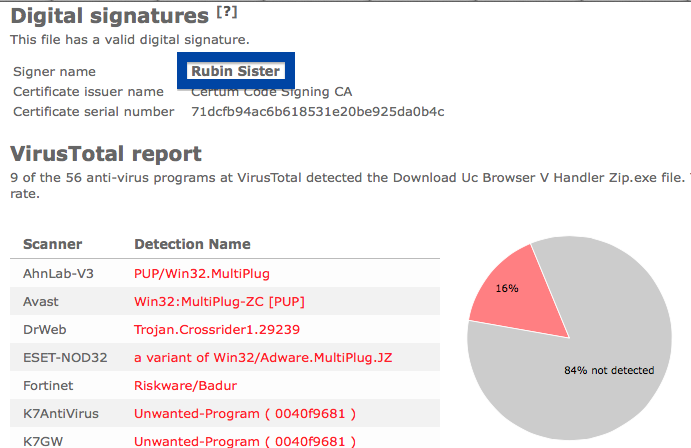
Hello readers! Just wanted to let you know about a publisher called SetupFlash (New Media Holdings Ltd.) before going back to writing some code for FreeFixer.
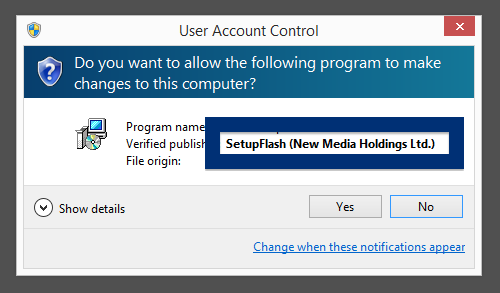
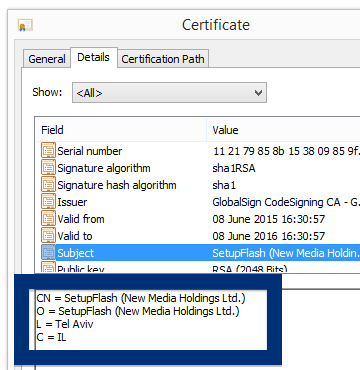
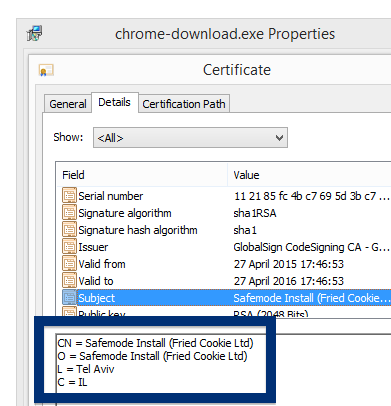
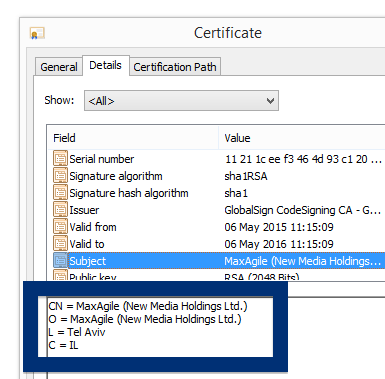
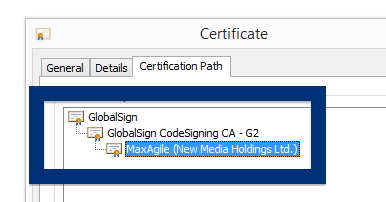
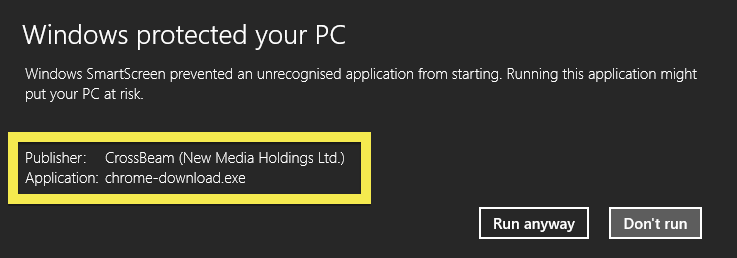
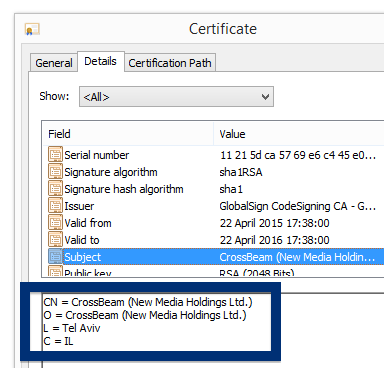
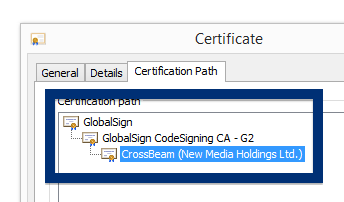
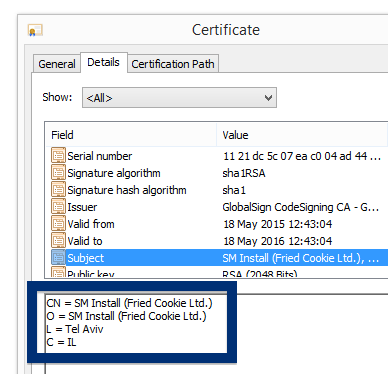
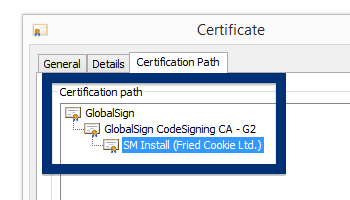
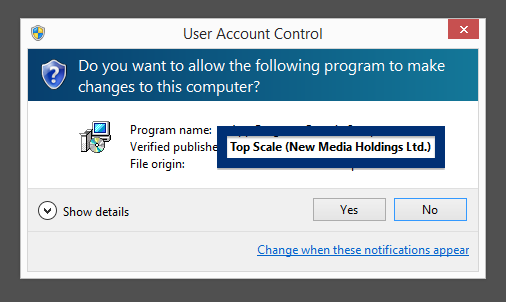
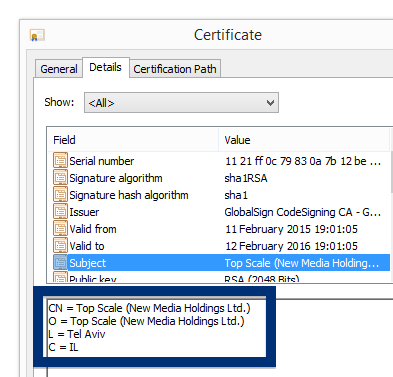
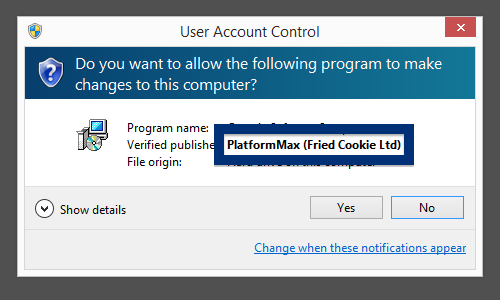
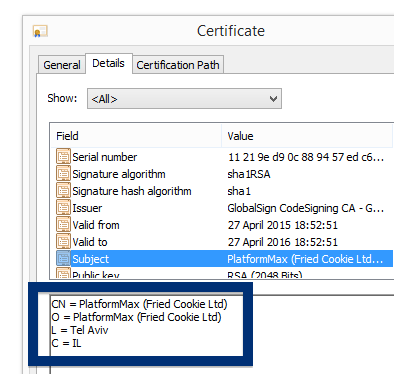
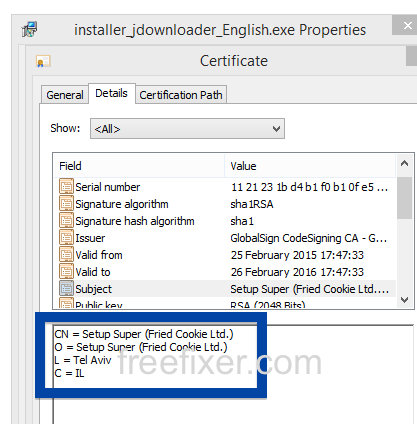
This is how it looks when double-clicking on the file and SetupFlash (New Media Holdings Ltd.) appears as the publisher. To get more details on the publisher, you can view the certificate by right-clicking on the file, and looking under the Digital Signatures tab. According to the certificate we can see that SetupFlash (New Media Holdings Ltd.) seems to be located in Israel and that the certificate is issued by GlobalSign CodeSigning CA – G2.
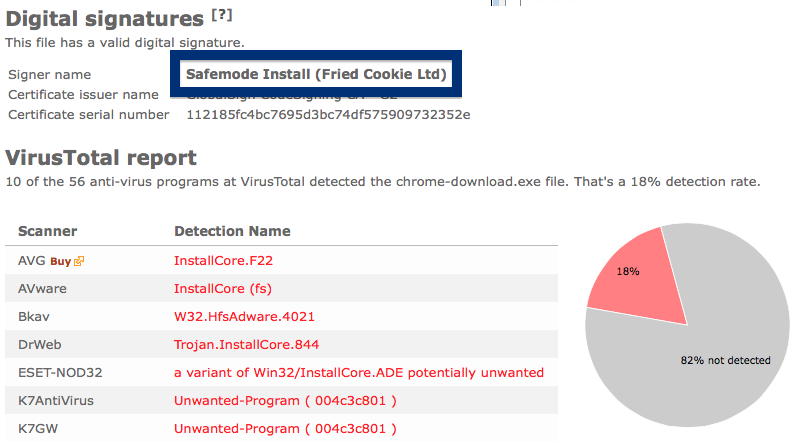
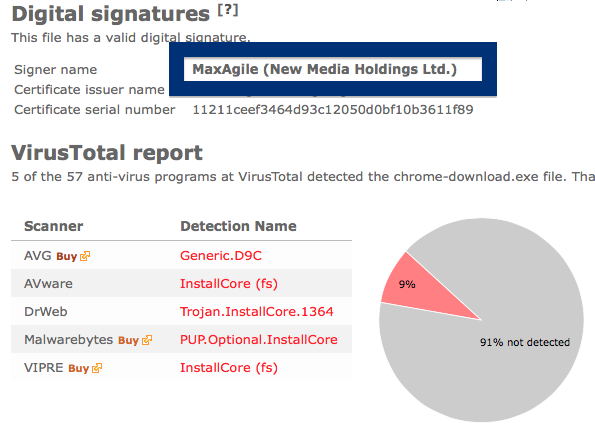
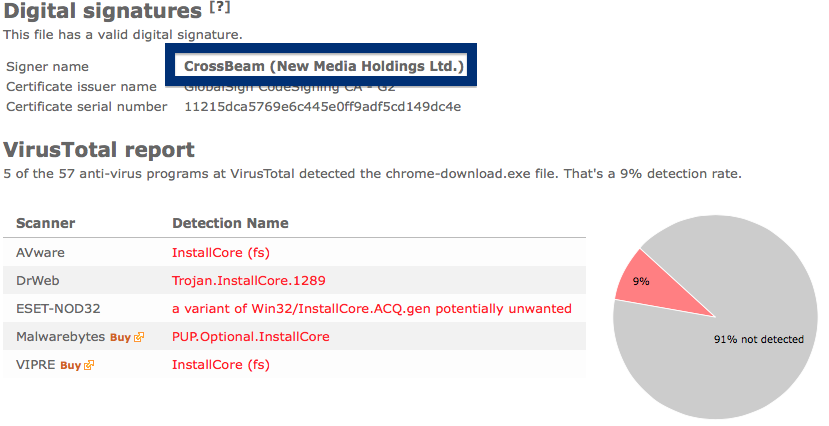
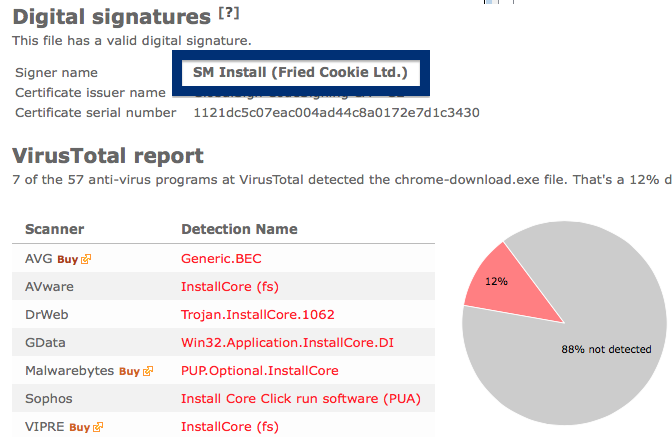
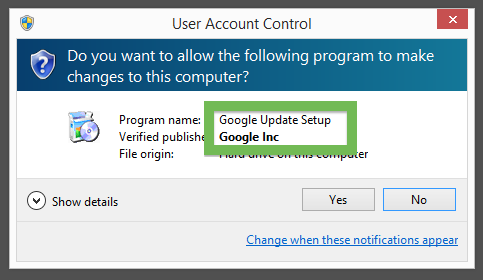
What caught my attention was that the download was called chrome-download.exe. This might look like an official Google Chrome download, but it is not. If it was an official download, it should be signed by Google Inc.. Here’s how the authentic Google Chrome looks like when you double click on it. Notice that the “Verified publisher” says “Google Inc”.
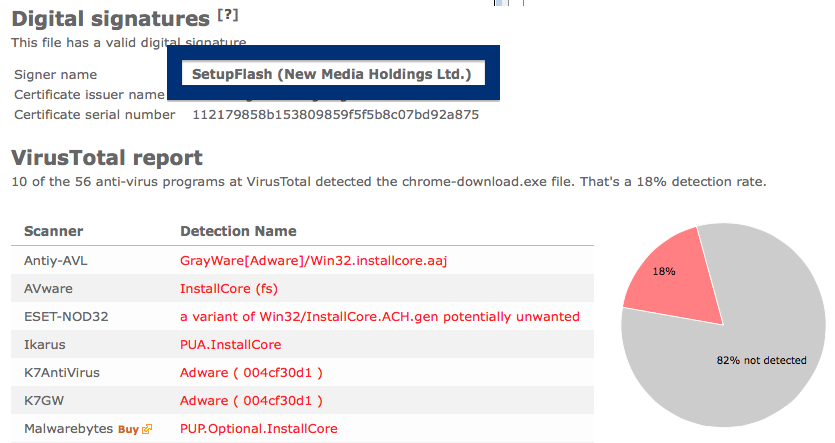
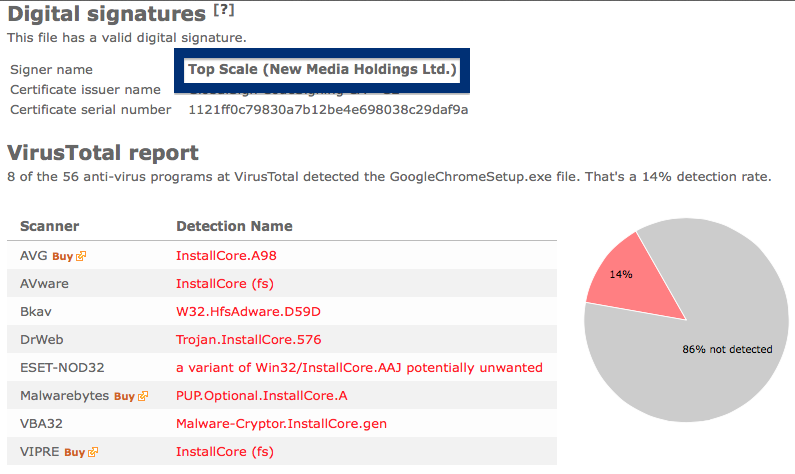
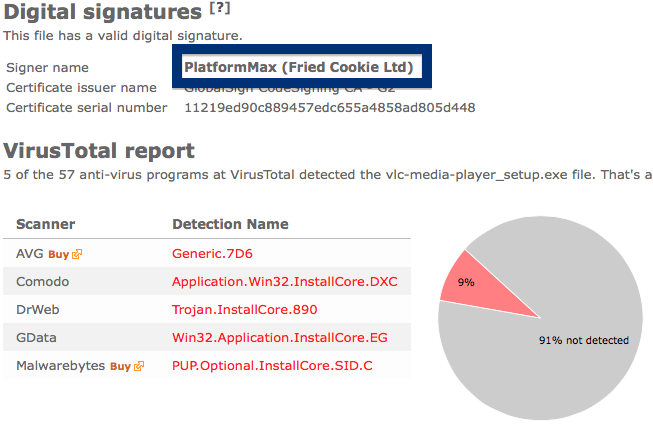
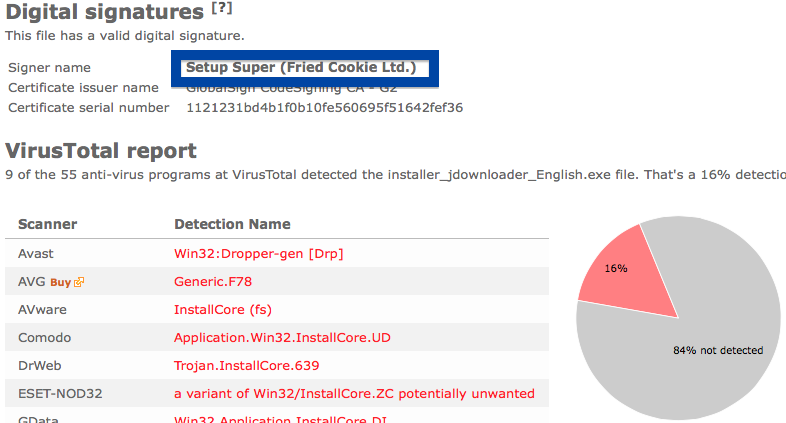
If you are considering to run the SetupFlash (New Media Holdings Ltd.) signed file, I’ll advice you not to. Delete it instead. Just check out detection list by some of the anti-virus program:
Ikarus classifies chrome-download.exe as PUA.InstallCore, VIPRE detects it as InstallCore (fs), Malwarebytes detects it as PUP.Optional.InstallCore and Sophos reports Install Core Click run software (PUA).
Did you also find a SetupFlash (New Media Holdings Ltd.) file?
Thank you for reading.