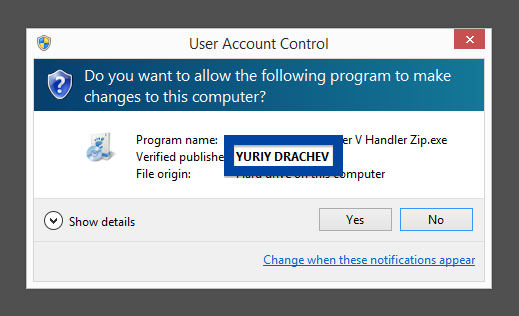
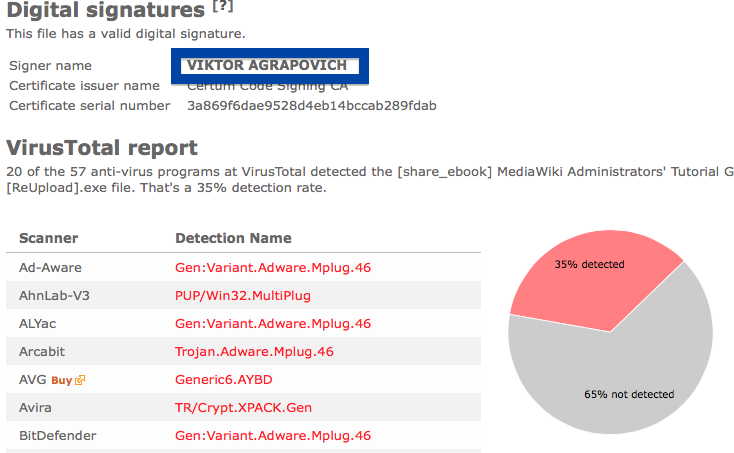
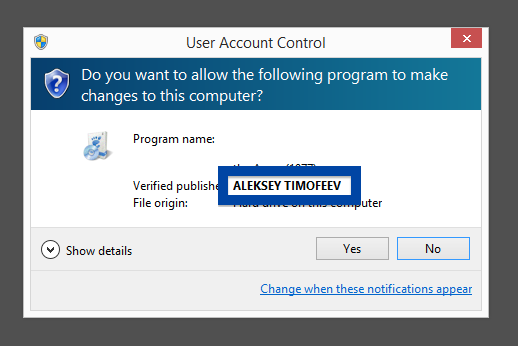
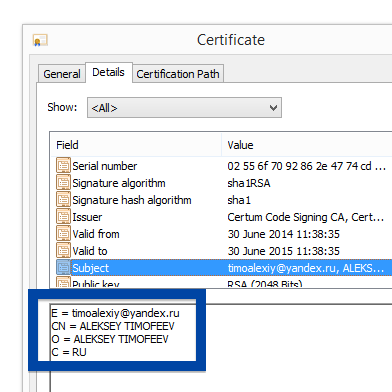
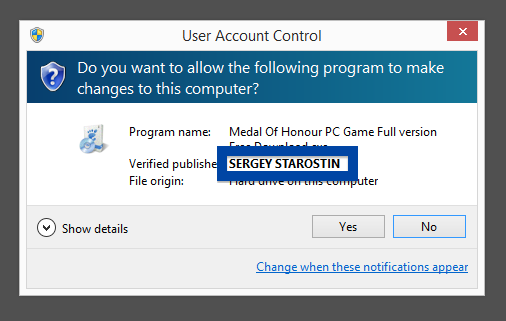
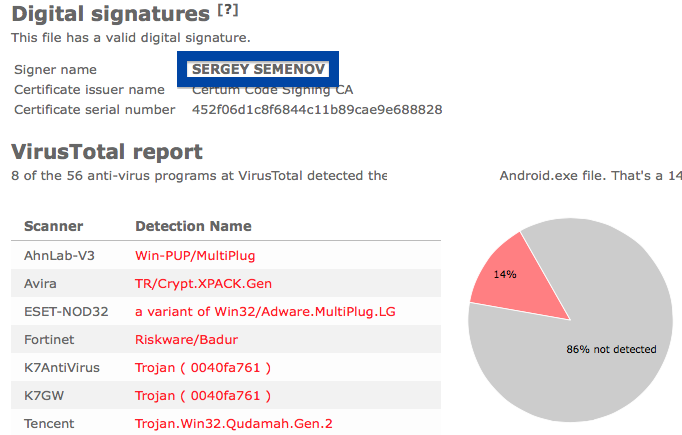
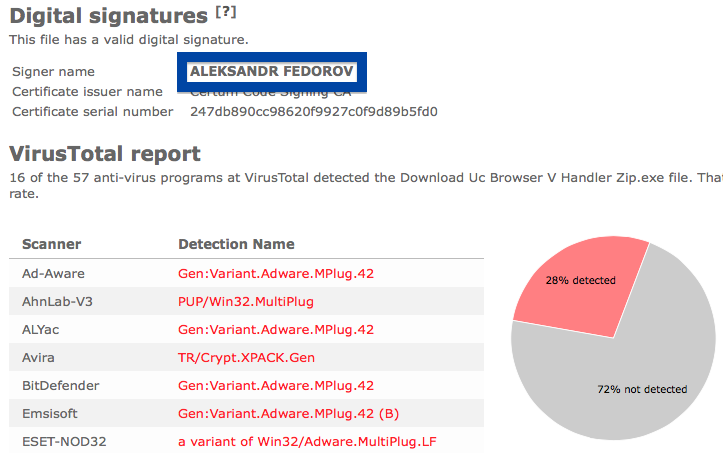
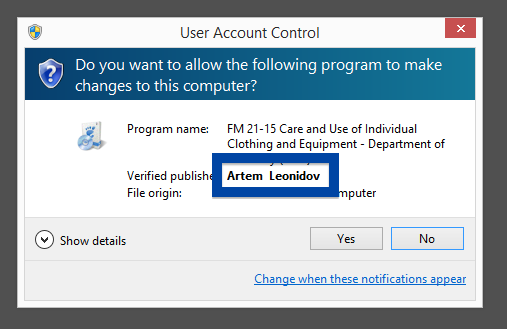
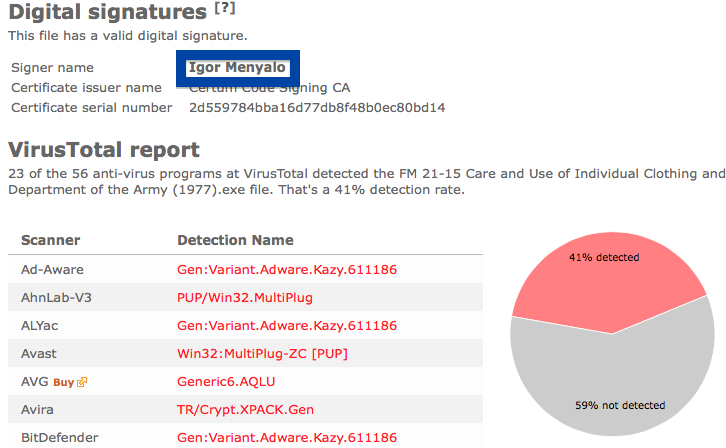
Hi there! Just wanted to give you heads-up on suspicious file I found right now. The file is named adobe_flash_setup.exe and digitally signed by OOO Mad Advert.
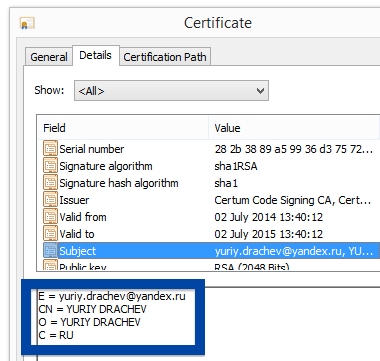
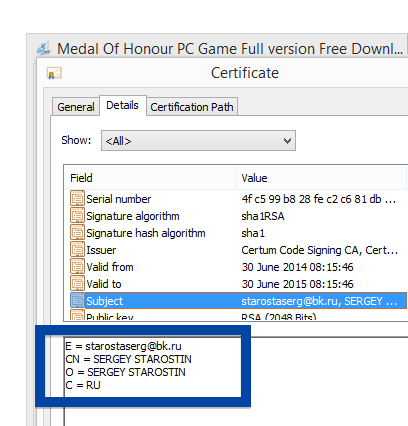
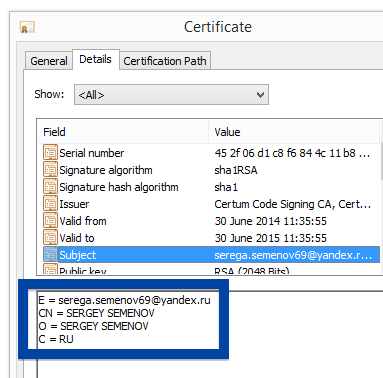
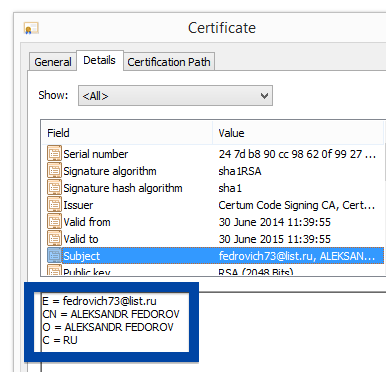
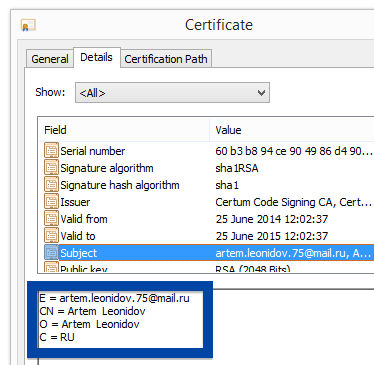
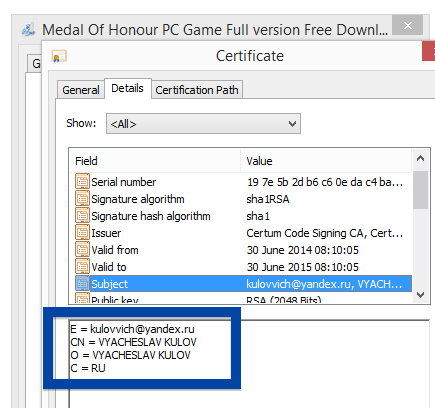
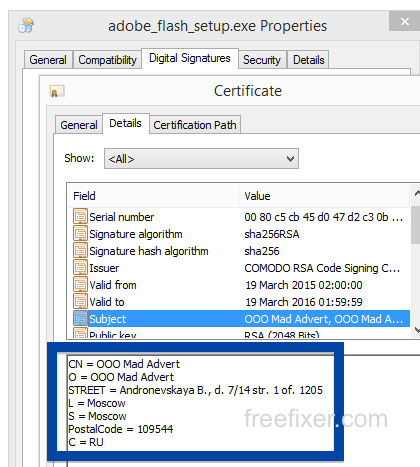
You can also check the digital signature under the file’s properties.. The screenshot below shows the OOO Mad Advert certificate. From the certificate info we can see that OOO Mad Advert appears to be located in Moscow, Russia.
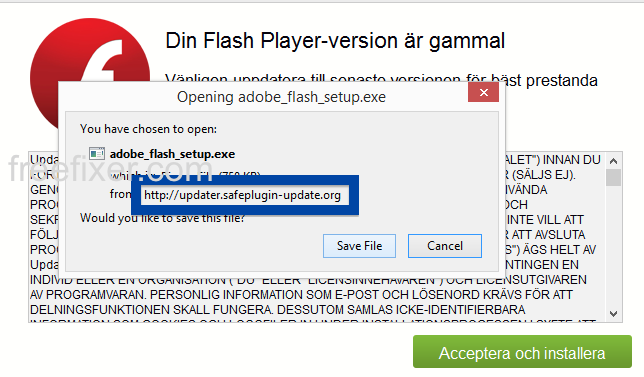
Here’s how the OOO MAD Advert download is promoted:
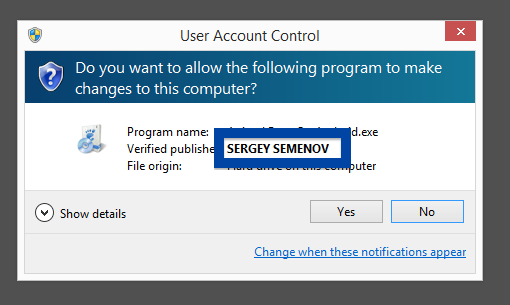
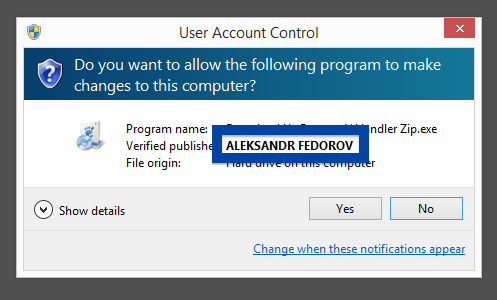
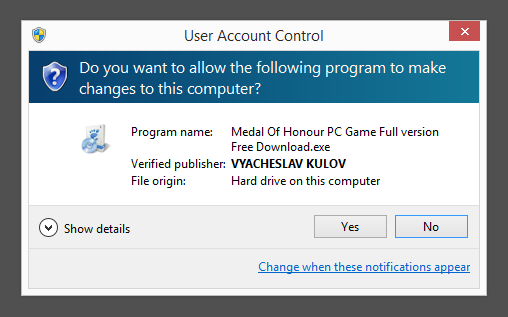
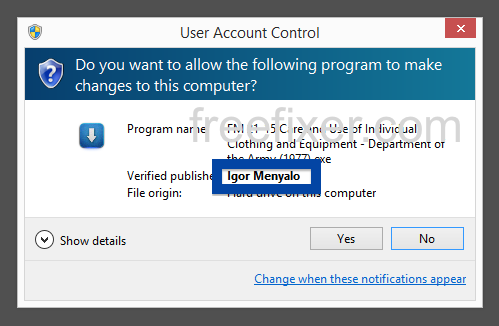
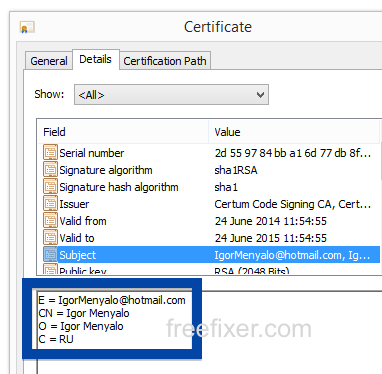
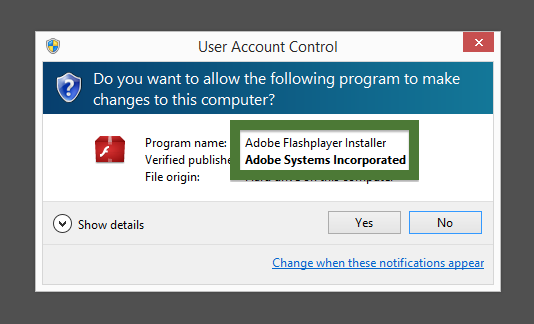
What caught my attention was that the download was called adobe_flash_setup.exe. This might look like an official Adobe Flash Player download, but it is not. If it was an official download, it should have been digitally signed by Adobe Systems Incorporated. Here’s how the authentic Adobe Flash Player looks like when you double click on it. Notice that the “Verified publisher” says “Adobe Systems Incorporated”.
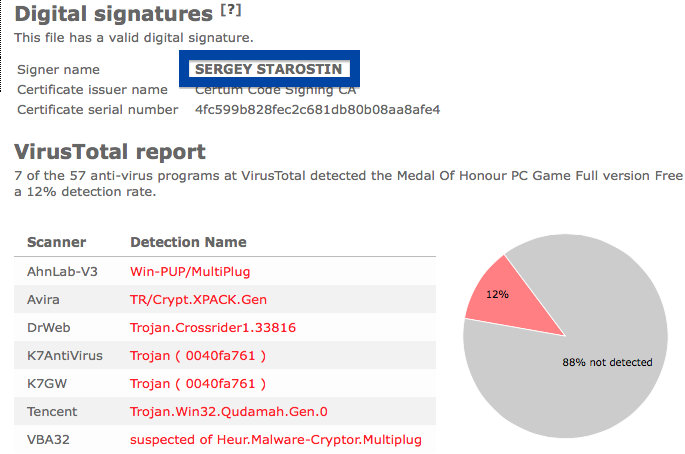
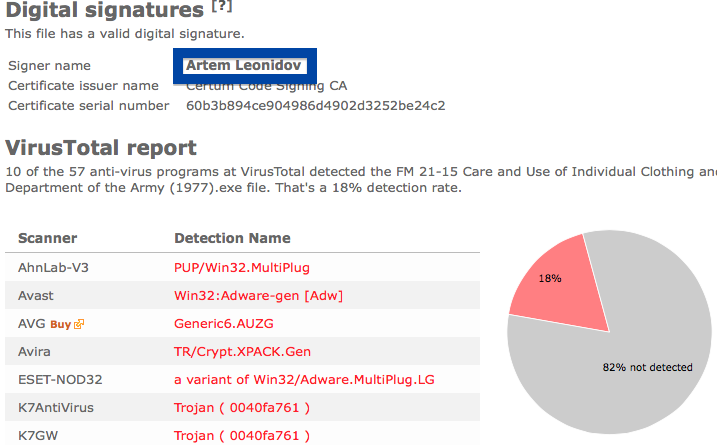
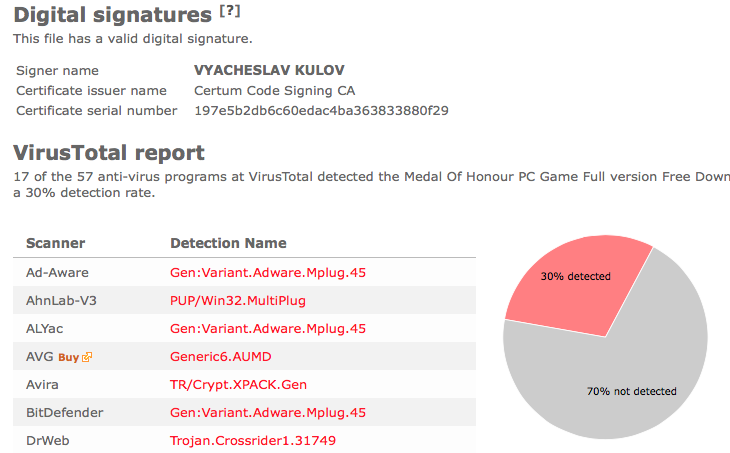
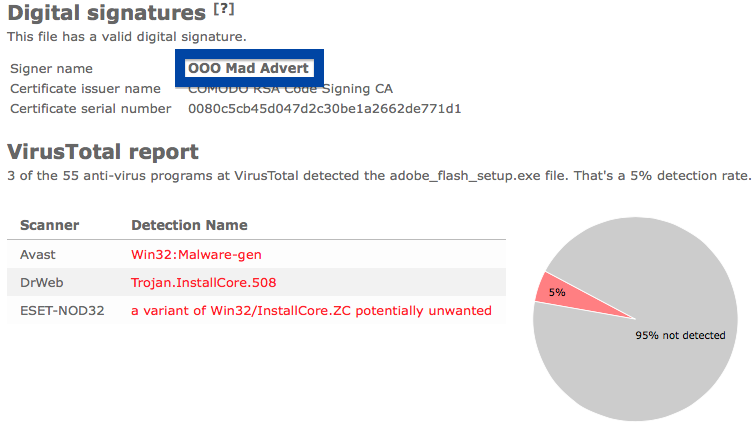
The detection rate is 3/55. Avast reports adobe_flash_setup.exe as Win32:Malware-gen, DrWeb calls it Trojan.InstallCore.508 and ESET-NOD32 calls it a variant of Win32/InstallCore.ZC potentially unwanted.
Did you also find a OOO Mad Advert file? Do you remember where you downloaded it?
Thank you for reading.