What is SegurazoService.exe?
SegurazoService.exe is part of Segurazo Antivirus and developed by Digital Communications Inc according to the SegurazoService.exe version information.
SegurazoService.exe's description is "Segurazo Service"
SegurazoService.exe is digitally signed by Digital Communications Inc..
SegurazoService.exe is usually located in the 'C:\Program Files (x86)\Segurazo\' folder.
Some of the anti-virus scanners at VirusTotal detected SegurazoService.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on SegurazoService.exe:
| Property | Value |
|---|---|
| Product name | Segurazo Antivirus |
| Company name | Digital Communications Inc |
| File description | Segurazo Service |
| Internal name | SegurazoService.exe |
| Original filename | SegurazoService.exe |
| Comments | Segurazo Service |
| Legal copyright | Copyright © Digital Communications Inc 2018 |
| Legal trademark | Digital Communications Inc |
| Product version | 1.0.14.2 |
| File version | 1.0.14.2 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | Segurazo Antivirus |
| Company name | Digital Communications Inc |
| File description | Segurazo Service |
| Internal name | SegurazoService.exe |
| Original filename | SegurazoService.exe |
| Comments | Segurazo Service |
| Legal copyright | Copyright © Digital Communications .. |
| Legal trademark | Digital Communications Inc |
| Product version | 1.0.14.2 |
| File version | 1.0.14.2 |
Digital signatures [?]
SegurazoService.exe has a valid digital signature.
| Property | Value |
|---|---|
| Signer name | Digital Communications Inc. |
| Certificate issuer name | COMODO RSA Extended Validation Code Signing CA |
| Certificate serial number | 12dfc245bb37b84c6da2fba4e421b62e |
VirusTotal report
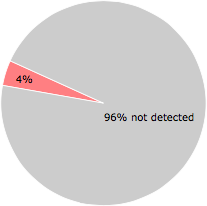
3 of the 70 anti-virus programs at VirusTotal detected the SegurazoService.exe file. That's a 4% detection rate.
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"file_recreated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"\\Device\\KsecDD",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE\\Blob",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\LanguageList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46\\Blob"
],
"dll_loaded": [
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\culture.dll",
"imagehlp.dll",
"kernel32",
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"credssp.dll",
"ntdll",
"API-MS-WIN-Service-Management-L2-1-0.dll",
"gdi32.dll",
"CFGMGR32.dll",
"DNSAPI.dll",
"kernel32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"CRYPTBASE.dll",
"C:\\Windows\\system32\\rsaenh.dll",
"SensApi.dll",
"ntdll.dll",
"cryptsp.dll",
"imm32.dll",
"ncrypt.dll",
"bcrypt.dll",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\System\\adff7dd9fe8e541775c46b6363401b22\\System.ni.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"cryptnet.dll",
"setupapi.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"psapi.dll",
"AdvApi32.dll",
"SspiCli.dll",
"advapi32.dll",
"ole32.dll",
"SHLWAPI.dll",
"CRYPTSP.dll",
"USER32.dll",
"DEVRTL.dll",
"C:\\Windows\\system32\\IMM32.DLL",
"mscorjit.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"IPHLPAPI.DLL",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\System.ServiceProce#\\df4cc33bfe326b259eeef086451a2528\\System.ServiceProcess.ni.dll",
"C:\\Windows\\assembly\\GAC_MSIL\\System\\2.0.0.0__b77a5c561934e089\\psapi.dll",
"ADVAPI32.dll",
"C:\\Windows\\system32\\CRYPT32.dll",
"winhttp.dll",
"profapi.dll",
"RPCRT4.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorwks.dll",
"C:\\Windows\\System32\\wship6.dll",
"USERENV.dll",
"NSI.dll",
"mscorsec.dll",
"RichEd20.dll",
"mscoree.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorsec.dll",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\mscorlib\\9469491f37d9c35b596968b206615309\\mscorlib.ni.dll",
"C:\\Windows\\system32\\cryptnet.dll",
"WINTRUST.DLL",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\ole32.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorjit.dll",
"C:\\Windows\\system32\\bcryptprimitives.dll",
"C:\\Windows\\system32\\mswsock.dll",
"shell32.dll",
"C:\\Windows\\System32\\wshtcpip.dll",
"WS2_32.dll",
"Cabinet.dll",
"WINHTTP.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\SystemCertificates\\My\\CRLs\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"C:\\Users\\cuck\\",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\SystemCertificates\\My\\CTLs\\",
"C:\\Windows\\System32\\en-US\\WINHTTP.dll.mui",
"C:\\Windows\\",
"C:\\Windows\\System32\\netmsg.dll",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sorttbls.nlp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\",
"C:\\Windows\\System32\\l_intl.nls",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\index143.dat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Windows\\assembly\\GAC_MSIL\\System\\2.0.0.0__b77a5c561934e089\\",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\94308059B57B3142E455B38A6EB92015",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\SystemCertificates\\My\\Certificates\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Windows\\System32\\en-US\\KERNELBASE.dll.mui",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorrc.dll",
"C:\\Windows\\assembly\\pubpol4.dat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Windows\\assembly\\GAC_MSIL\\System.ServiceProcess\\2.0.0.0__b03f5f7f11d50a3a\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\",
"C:\\Windows\\System32\\rsaenh.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\Content\\94308059B57B3142E455B38A6EB92015",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sortkey.nlp",
"C:\\Users\\cuck\\AppData\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Configuration.Install__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Drawing__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.ServiceProcess__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Configuration__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\LocalIntranet",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\GACChangeNotification\\Default",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\49c35b12\\5d7615c1",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework\\Policy\\Standards",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Windows.Forms__b77a5c561934e089",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\Upgrades",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards\\v2.0.50727",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\v2.0.50727\\Security\\Policy",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System__b77a5c561934e089",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\StrongName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\PublisherPolicy\\Default",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Xml__b77a5c561934e089",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\v2.0",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\Class\\{4d36e972-e325-11ce-bfc1-08002be10318}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\Internet",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\internal\\jit\\Perf",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\APTCA",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\AppPatch",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\Standards",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e"
],
"resolves_host": [
"www.download.windowsupdate.com",
"crt.usertrust.com",
"crt.comodoca.com"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"regkey_deleted": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"file_exists": [
"C:\\Windows\\inf\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.config",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\msvcr80.dll",
"C:\\Windows\\System32\\fveui.dll",
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"C:\\Windows\\Globalization\\en-us.nlp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\fusion.localgac",
"C:\\Windows\\System32\\QAGENTRT.DLL",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Windows\\assembly\\GAC\\PublisherPolicy.tme",
"C:\\Windows\\System32\\dnsapi.dll",
"C:\\Windows\\System32\\MSCOREE.DLL.local",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Windows\\System32\\p2pcollab.dll"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config.cch",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\BF4F70F5959F0AEBFB03EDDC210D5768",
"C:\\Windows\\Microsoft.NET\\Framework64\\Upgrades.2.0.50727\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config.cch",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\74FBF93595CFC8459196065CE54AD928",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\46D7547AA7F9B9DA290D5C19668E04C1",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\6F0E55DF8A480361A1A27F82DAA1ABB7",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config.cch"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\94308059B57B3142E455B38A6EB92015",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\Content\\94308059B57B3142E455B38A6EB92015"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeInline",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.44.3.4!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\D4DE20D05E66FC53FE1A50882C78DB2852CAE474\\Blob",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\WinSock2\\Parameters\\Protocol_Catalog9\\Serial_Access_Num",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\Modules",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\SecurityProviders\\SecurityProviders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Drawing,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\A43489159A520F0D93D032CCAF37E7FE20A8B419\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DiagMatchAnyMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\97817950D81C9670CC34D809CF794431367EF474\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\ShareCredsWithWinHttp",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Version",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Enhanced RSA and AES Cryptographic Provider\\Image Path",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\CryptnetPreFetchTriggerPeriodSeconds",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.47.1.1!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\ILDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\ILUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\DevOverrideEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlRetrievalCountPerChain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\EvalationData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Configuration,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\ProxySettingsPerUser",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NoClientChecks",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DownloadCacheQuotaInKB",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Parameters\\Transports",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\SIG",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\system32\\qagentrt.dll,-10",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\OnlyUseLatestCLR",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LoggingLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\ForceLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\75E0ABB6138512271C04F85FDDDE38E4B7242EFE\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\ChainCacheResyncFiletime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\EvalationData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TailCallOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogFailures",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadOverride",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CseOn",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlRetrievalCertCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\ConfigString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\Latest",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\Local AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\MachineGuid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlRetrievalByteCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\245C97DF7514E7CF2DF8BE72AE957B9E04741E85\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\UseLegacyIdentityFormat",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\mscorlib,2.0.0.0,,b77a5c561934e089,AMD64",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugFlags",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Comment",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\DisableUnsupportedCriticalExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\A8985D3A65E5E5C4B2D7D66D40C6DD2FB19C5436\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Cryptography\\PrivateKeyLifetimeSeconds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Enhanced RSA and AES Cryptographic Provider\\Type",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\SESSION MANAGER\\SafeProcessSearchMode",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\DisplayName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\LogLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.67.1.1!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\Certificates\\FEE449EE0E3965A5246F000E87FDE2A065FD89D4\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip6\\WinSock 2.0 Provider ID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\Certificates\\109F1CAED645BB78B3EA2B94C0697C740733031C\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\NIUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Xml,2.0.0.0,,b77a5c561934e089,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\LegacyPolicyTimeStamp",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Cryptography\\PrivKeyCacheMaxItems",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Configuration.Install,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\Status",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\0563B8630D62D75ABBC8AB1E4BDFB5A899B24D43\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\Disallowed\\Certificates\\637162CC59A3A1E25956FA5FA8F60D2E1C52EAC6\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStart",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\742C3192E607E424EB4549542BE1BBC53E6174E2\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\ConfigString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStartAtJit",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\WinHttpSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\Disallowed\\Certificates\\7D7F4414CCEF168ADF6BF40753B5BECD78375931\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\CacheLocation",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\LsaExtensionConfig\\SspiCli\\CheckSignatureRoutine",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\DisableCANameConstraints",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ILDependencies",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\system32\\p2pcollab.dll,-8042",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\BE36A4562FB2EE05DBB3D32323ADF445084ED656\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CLRLoadLogDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MVID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Cleanup\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\LsaExtensionConfig\\SspiCli\\CheckSignatureDll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\ILDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\WinHttp\\DisableBranchCache",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\InstallRoot",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.67.1.2!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\Status",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\CRLs\\A377D1B1C0538833035211F4083D00FECC414DAB\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DisableMSIPeek",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Capabilities",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\DisplayName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\WinTrust\\Trust Providers\\Software Publishing\\State",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\18F7C1FCC3090203FD5BAA2F861A754976C8DD25\\Blob",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\system32\\dnsapi.dll,-103",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\System32\\fveui.dll,-844",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TURNOFFDEBUGINFO",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableConfigCache",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\EvalationData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\TokenSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxUrlRetrievalByteCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\5FB7EE0633E259DBAD0C4C9AE6D38F1A61C7DC25\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\LatestIndex",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlCountInCert",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigString",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\System32\\fveui.dll,-843",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogResourceBinds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System,2.0.0.0,,b77a5c561934e089,MSIL",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip\\WinSock 2.0 Provider ID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\EnableLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Cleanup\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DiagLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\Certificates\\D559A586669B08F46A30A133F8A9ED3D038E2EA8\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\LogMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\NewGCCalc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeCalliOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\7F88CD7223F3C813818C994614A89C99FA3B5247\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\WinHttp\\Tracing\\Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\LogMaxFileSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\SystemCertificates\\Root\\ProtectedRoots\\Certificates",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Cryptography\\PrivKeyCachePurgeIntervalSeconds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Windows.Forms,2.0.0.0,,b77a5c561934e089,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.64.1.1!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\DisableMandatoryBasicConstraints",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\CDD4EEAE6000AC7F40C3802C171E30148030C072\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Type",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\EnableInetUnknownAuth",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy\\Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableHotCold",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\VersioningLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\MVID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\EnableWeakSignatureFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\MaximumAllowedAllocationSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\LoadAppInit_DLLs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.ServiceProcess,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\SIG",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\Security\\Safety Warning Level",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\MVID",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\StringCacheSettings\\StringCacheGeneration",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\RpcId",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\index4"
]
}Dropped
[
{
"yara": [],
"sha1": "c64ad224b877cd5bbdcdb1799b71f3682602d231",
"name": "b0a39e28d93f7822_Tar745A.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"type": "data",
"sha256": "b0a39e28d93f7822fe6cac1e082c7adc581dcd2b61eb9f536e74bd14a75b27bc",
"urls": [
"http:\/\/www.microsoft.com\/pkiops\/certs\/Microsoft%20Certificate%20Trust%20List%20PCA(3).crt0",
"http:\/\/www.microsoft.com\/pki\/certs\/MicRooCerAut_2010-06-23.crt07",
"http:\/\/www.microsoft.com\/pki\/certs\/MicCerLisCA2011_2011-03-29.crt0",
"http:\/\/www.microsoft.com\/pki\/certs\/MicrosoftRootCert.crt0",
"http:\/\/www.microsoft.com\/pkiops\/crl\/Microsoft%20Certificate%20Trust%20List%20PCA(3).crl0u"
],
"crc32": "B495BE07",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/1981\/files\/b0a39e28d93f7822_Tar745A.tmp",
"ssdeep": null,
"size": 138525,
"sha512": "0663fb22bcefd0ac5f090104322a8c0dc1ceb77a168b589d7dbb9a74d109daf38beac97dab715220abab08c355496f5719159e17995248caa19eff45bc2a5d46",
"pids": [
2816
],
"md5": "0e34ebf89b843b303f0fb5f194be9d28"
},
{
"yara": [],
"sha1": "cf925fc512b936fe7d44ceb6e999e4a020ed6ff0",
"name": "4c9c4d831d61c8c3_Cab7459.tmp",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"type": "Microsoft Cabinet archive data, 56952 bytes, 1 file",
"sha256": "4c9c4d831d61c8c38b2513f9b431ef4f4cf6af9fb18a2317cd2178d6e0997822",
"urls": [],
"crc32": "5168F337",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/1981\/files\/4c9c4d831d61c8c3_Cab7459.tmp",
"ssdeep": null,
"size": 56952,
"sha512": "65dc435f6d3e1afd347ba1617a3eee59c6660f221faa36456a09e307d434d7276e8095e8aa34d59933e685a9f84564ec783e59ae9658791f7ebdbbc2eda32f7a",
"pids": [
2816
],
"md5": "04d79a0dc77a8f449cbff6252862d398"
}
]Generic
[
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"process_name": "3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"pid": 2816,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"file_recreated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"\\Device\\KsecDD",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE\\Blob",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\LanguageList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46\\Blob"
],
"dll_loaded": [
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\culture.dll",
"imagehlp.dll",
"kernel32",
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"credssp.dll",
"ntdll",
"API-MS-WIN-Service-Management-L2-1-0.dll",
"gdi32.dll",
"CFGMGR32.dll",
"DNSAPI.dll",
"kernel32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"CRYPTBASE.dll",
"C:\\Windows\\system32\\rsaenh.dll",
"SensApi.dll",
"ntdll.dll",
"cryptsp.dll",
"imm32.dll",
"ncrypt.dll",
"bcrypt.dll",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\System\\adff7dd9fe8e541775c46b6363401b22\\System.ni.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"cryptnet.dll",
"setupapi.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"psapi.dll",
"AdvApi32.dll",
"SspiCli.dll",
"advapi32.dll",
"ole32.dll",
"SHLWAPI.dll",
"CRYPTSP.dll",
"USER32.dll",
"DEVRTL.dll",
"C:\\Windows\\system32\\IMM32.DLL",
"mscorjit.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"IPHLPAPI.DLL",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\System.ServiceProce#\\df4cc33bfe326b259eeef086451a2528\\System.ServiceProcess.ni.dll",
"C:\\Windows\\assembly\\GAC_MSIL\\System\\2.0.0.0__b77a5c561934e089\\psapi.dll",
"ADVAPI32.dll",
"C:\\Windows\\system32\\CRYPT32.dll",
"winhttp.dll",
"profapi.dll",
"RPCRT4.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorwks.dll",
"C:\\Windows\\System32\\wship6.dll",
"USERENV.dll",
"NSI.dll",
"mscorsec.dll",
"RichEd20.dll",
"mscoree.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorsec.dll",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\mscorlib\\9469491f37d9c35b596968b206615309\\mscorlib.ni.dll",
"C:\\Windows\\system32\\cryptnet.dll",
"WINTRUST.DLL",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\ole32.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorjit.dll",
"C:\\Windows\\system32\\bcryptprimitives.dll",
"C:\\Windows\\system32\\mswsock.dll",
"shell32.dll",
"C:\\Windows\\System32\\wshtcpip.dll",
"WS2_32.dll",
"Cabinet.dll",
"WINHTTP.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\SystemCertificates\\My\\CRLs\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"C:\\Users\\cuck\\",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\SystemCertificates\\My\\CTLs\\",
"C:\\Windows\\System32\\en-US\\WINHTTP.dll.mui",
"C:\\Windows\\",
"C:\\Windows\\System32\\netmsg.dll",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sorttbls.nlp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\",
"C:\\Windows\\System32\\l_intl.nls",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\index143.dat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Windows\\assembly\\GAC_MSIL\\System\\2.0.0.0__b77a5c561934e089\\",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\94308059B57B3142E455B38A6EB92015",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\SystemCertificates\\My\\Certificates\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Windows\\System32\\en-US\\KERNELBASE.dll.mui",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorrc.dll",
"C:\\Windows\\assembly\\pubpol4.dat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Windows\\assembly\\GAC_MSIL\\System.ServiceProcess\\2.0.0.0__b03f5f7f11d50a3a\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\",
"C:\\Windows\\System32\\rsaenh.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\Content\\94308059B57B3142E455B38A6EB92015",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sortkey.nlp",
"C:\\Users\\cuck\\AppData\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Configuration.Install__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Drawing__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.ServiceProcess__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Configuration__b03f5f7f11d50a3a",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\LocalIntranet",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\GACChangeNotification\\Default",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\49c35b12\\5d7615c1",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework\\Policy\\Standards",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Windows.Forms__b77a5c561934e089",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\Upgrades",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards\\v2.0.50727",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\v2.0.50727\\Security\\Policy",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System__b77a5c561934e089",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\StrongName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\PublisherPolicy\\Default",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\policy.2.0.System.Xml__b77a5c561934e089",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\v2.0",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\Class\\{4d36e972-e325-11ce-bfc1-08002be10318}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\Internet",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\internal\\jit\\Perf",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\APTCA",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\AppPatch",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\Standards",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e"
],
"resolves_host": [
"www.download.windowsupdate.com",
"crt.usertrust.com",
"crt.comodoca.com"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"regkey_deleted": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp"
],
"file_exists": [
"C:\\Windows\\inf\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.config",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\msvcr80.dll",
"C:\\Windows\\System32\\fveui.dll",
"C:\\Users\\cuck\\AppData\\LocalLow",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin",
"C:\\Windows\\Globalization\\en-us.nlp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\fusion.localgac",
"C:\\Windows\\System32\\QAGENTRT.DLL",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Windows\\assembly\\GAC\\PublisherPolicy.tme",
"C:\\Windows\\System32\\dnsapi.dll",
"C:\\Windows\\System32\\MSCOREE.DLL.local",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Windows\\System32\\p2pcollab.dll"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb.bin.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config.cch",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\BF4F70F5959F0AEBFB03EDDC210D5768",
"C:\\Windows\\Microsoft.NET\\Framework64\\Upgrades.2.0.50727\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config.cch",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\74FBF93595CFC8459196065CE54AD928",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\46D7547AA7F9B9DA290D5C19668E04C1",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\6F0E55DF8A480361A1A27F82DAA1ABB7",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config.cch"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab100F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarF14.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab75B3.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar745A.tmp",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\MetaData\\94308059B57B3142E455B38A6EB92015",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab25FA.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar26D8.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar101F.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB8A1.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB775.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA08E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab7459.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB96D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Cab26C7.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA08D.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB785.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar75B4.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabF03.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabB8A0.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarA17B.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarB96E.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabA16A.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\TarE468.tmp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\Tar260B.tmp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\CabE457.tmp",
"C:\\Users\\cuck\\AppData\\LocalLow\\Microsoft\\CryptnetUrlCache\\Content\\94308059B57B3142E455B38A6EB92015"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeInline",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.44.3.4!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\D4DE20D05E66FC53FE1A50882C78DB2852CAE474\\Blob",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\WinSock2\\Parameters\\Protocol_Catalog9\\Serial_Access_Num",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\UseDelayedAcceptance",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\Modules",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\SecurityProviders\\SecurityProviders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Drawing,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\A43489159A520F0D93D032CCAF37E7FE20A8B419\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DiagMatchAnyMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\97817950D81C9670CC34D809CF794431367EF474\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\ShareCredsWithWinHttp",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Version",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Enhanced RSA and AES Cryptographic Provider\\Image Path",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\CryptnetPreFetchTriggerPeriodSeconds",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.47.1.1!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\ILDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\ILUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\DevOverrideEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlRetrievalCountPerChain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\EvalationData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Configuration,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\ProxySettingsPerUser",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NoClientChecks",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DownloadCacheQuotaInKB",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Parameters\\Transports",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\SIG",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\system32\\qagentrt.dll,-10",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\OnlyUseLatestCLR",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LoggingLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\ForceLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\75E0ABB6138512271C04F85FDDDE38E4B7242EFE\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\ChainCacheResyncFiletime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\EvalationData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TailCallOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogFailures",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadOverride",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CseOn",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlRetrievalCertCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\ConfigString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\Latest",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\Local AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\MachineGuid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlRetrievalByteCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\245C97DF7514E7CF2DF8BE72AE957B9E04741E85\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\UseLegacyIdentityFormat",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\mscorlib,2.0.0.0,,b77a5c561934e089,AMD64",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugFlags",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Comment",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\DisableUnsupportedCriticalExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\A8985D3A65E5E5C4B2D7D66D40C6DD2FB19C5436\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Cryptography\\PrivateKeyLifetimeSeconds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Enhanced RSA and AES Cryptographic Provider\\Type",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\SESSION MANAGER\\SafeProcessSearchMode",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\DisplayName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\LogLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.67.1.1!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\Certificates\\FEE449EE0E3965A5246F000E87FDE2A065FD89D4\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip6\\WinSock 2.0 Provider ID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\Certificates\\109F1CAED645BB78B3EA2B94C0697C740733031C\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\NIUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Xml,2.0.0.0,,b77a5c561934e089,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\LegacyPolicyTimeStamp",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Cryptography\\PrivKeyCacheMaxItems",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Configuration.Install,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\Status",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\0563B8630D62D75ABBC8AB1E4BDFB5A899B24D43\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\CertCheck\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\Disallowed\\Certificates\\637162CC59A3A1E25956FA5FA8F60D2E1C52EAC6\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStart",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\742C3192E607E424EB4549542BE1BBC53E6174E2\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\ConfigString",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStartAtJit",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\WinHttpSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\Disallowed\\Certificates\\7D7F4414CCEF168ADF6BF40753B5BECD78375931\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\CacheLocation",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\LsaExtensionConfig\\SspiCli\\CheckSignatureRoutine",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\DisableCANameConstraints",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ILDependencies",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\system32\\p2pcollab.dll,-8042",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\BE36A4562FB2EE05DBB3D32323ADF445084ED656\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CLRLoadLogDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\424bd4d8\\1c83327b\\8e\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MVID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Cleanup\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\MinSockaddrLength",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\LsaExtensionConfig\\SspiCli\\CheckSignatureDll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\ILDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\WinHttp\\DisableBranchCache",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\InstallRoot",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.67.1.2!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\73843e06\\43a920ef\\6e\\Status",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\MaxSockaddrLength",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\CRLs\\A377D1B1C0538833035211F4083D00FECC414DAB\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DisableMSIPeek",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Capabilities",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\DisplayName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\WinTrust\\Trust Providers\\Software Publishing\\State",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\HelperDllName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\18F7C1FCC3090203FD5BAA2F861A754976C8DD25\\Blob",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\system32\\dnsapi.dll,-103",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\System32\\fveui.dll,-844",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TURNOFFDEBUGINFO",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\c991064\\2bd33e1c\\81\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableConfigCache",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\EvalationData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\TokenSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxUrlRetrievalByteCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\5FB7EE0633E259DBAD0C4C9AE6D38F1A61C7DC25\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\LatestIndex",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\19ab8d57\\1bd7b0d8\\8f\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\MaxAIAUrlCountInCert",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigString",
"HKEY_CURRENT_USER\\Local Settings\\MuiCache\\2\\52C64B7E\\@%SystemRoot%\\System32\\fveui.dll,-843",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Signature\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogResourceBinds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System,2.0.0.0,,b77a5c561934e089,MSIL",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Winsock\\Setup Migration\\Providers\\Tcpip\\WinSock 2.0 Provider ID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\EnableLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Cleanup\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DiagLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\CA\\Certificates\\D559A586669B08F46A30A133F8A9ED3D038E2EA8\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\LogMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\NewGCCalc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeCalliOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\7F88CD7223F3C813818C994614A89C99FA3B5247\\Blob",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\WinHttp\\Tracing\\Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\LogMaxFileSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\SystemCertificates\\Root\\ProtectedRoots\\Certificates",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Cryptography\\PrivKeyCachePurgeIntervalSeconds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.Windows.Forms,2.0.0.0,,b77a5c561934e089,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CryptDllFindOIDInfo\\1.3.6.1.4.1.311.64.1.1!7\\Name",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\DisableMandatoryBasicConstraints",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\ROOT\\Certificates\\CDD4EEAE6000AC7F40C3802C171E30148030C072\\Blob",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\Type",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\EnableInetUnknownAuth",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy\\Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3f50fe4f\\6f1da7aa\\90\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableHotCold",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\VersioningLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\5fcea75a\\3c9c8d7b\\6f\\MVID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Message\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\OID\\EncodingType 0\\CertDllCreateCertificateChainEngine\\Config\\EnableWeakSignatureFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Initialization\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\OLE\\MaximumAllowedAllocationSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\LoadAppInit_DLLs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\System.ServiceProcess,2.0.0.0,,b03f5f7f11d50a3a,MSIL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\3c9c8d7b\\46b95040\\74\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\Certificate\\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE}\\$DLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Providers\\Trust\\FinalPolicy\\{31D1ADC1-D329-11D1-8ED8-0080C76516C6}\\$Function",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\6dc7d4c0\\a5cd4db\\87\\SIG",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\Security\\Safety Warning Level",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\30bc7c4f\\3f50fe4f\\90\\MVID",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\TCPIP6\\Parameters\\Winsock\\Mapping",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\StringCacheSettings\\StringCacheGeneration",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\SspiCache\\credssp.dll\\RpcId",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\PublisherPolicy\\Default\\index4"
]
},
"first_seen": 1566539604.5938,
"ppid": 2016
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1566539604.3281,
"ppid": 376
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "Checks if process is being debugged by a debugger",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741700,
"api": "IsDebuggerPresent",
"return_value": 0,
"arguments": {},
"time": 1566539605.0308,
"tid": 2420,
"flags": {}
},
"pid": 2816,
"type": "call",
"cid": 372
}
],
"references": [],
"name": "checks_debugger"
},
{
"markcount": 1,
"families": [],
"description": "Collects information to fingerprint the system (MachineGuid, DigitalProductId, SystemBiosDate)",
"severity": 1,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\MachineGuid",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "recon_fingerprint"
},
{
"markcount": 1,
"families": [],
"description": "This executable has a PDB path",
"severity": 1,
"marks": [
{
"category": "pdb_path",
"ioc": "SegurazoService.pdb",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "has_pdb"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1566539605.2497,
"tid": 2420,
"flags": {}
},
"pid": 2816,
"type": "call",
"cid": 475
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 1,
"families": [],
"description": "The executable contains unknown PE section names indicative of a packer (could be a false positive)",
"severity": 1,
"marks": [
{
"category": "section",
"ioc": ".sdata",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_features"
},
{
"markcount": 55,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feef821000"
},
"time": 1566539604.9367,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 254
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9e000"
},
"time": 1566539604.9997,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 329
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9e000"
},
"time": 1566539604.9997,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 331
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 385
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 387
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 389
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 391
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 393
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 395
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 397
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 399
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 401
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 403
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 405
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 407
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 409
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 411
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 413
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 415
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 417
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9e000"
},
"time": 1566539605.0468,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2816,
"type": "call",
"cid": 419
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00052000"
},
"time": 1566539605.2808,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 539
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 589824,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 1056768,
"base_address": "0x000007fffff10000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_RESERVE|MEM_TOP_DOWN"
}
},
"pid": 2816,
"type": "call",
"cid": 6660
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007fffff10000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 6661
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007fffff10000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 6662
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 65536,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 1056768,
"base_address": "0x000007fffff00000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_RESERVE|MEM_TOP_DOWN"
}
},
"pid": 2816,
"type": "call",
"cid": 6663
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007fffff00000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 6664
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0010a000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 6665
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00042000"
},
"time": 1566539635.4058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 6666
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00053000"
},
"time": 1566539663.4367,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9391
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0011a000"
},
"time": 1566539663.4527,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9402
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00142000"
},
"time": 1566539663.4527,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9403
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0011d000"
},
"time": 1566539663.4527,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9404
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0005c000"
},
"time": 1566539663.4838,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9445
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00054000"
},
"time": 1566539663.5308,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9488
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00190000"
},
"time": 1566539663.5308,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9490
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00102000"
},
"time": 1566539663.6088,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9509
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00055000"
},
"time": 1566539663.6558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9519
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00056000"
},
"time": 1566539663.8588,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 9627
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 61440,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00191000"
},
"time": 1566539664.3277,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 10190
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0010b000"
},
"time": 1566539664.9058,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 10969
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff001a0000"
},
"time": 1566539665.0617,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 11482
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00043000"
},
"time": 1566539665.0777,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 11505
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0005a000"
},
"time": 1566539665.0777,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 11507
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0006f000"
},
"time": 1566539667.1558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 17586
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff000a4000"
},
"time": 1566539667.1558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 17588
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00073000"
},
"time": 1566539667.1558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 17589
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff001a1000"
},
"time": 1566539667.1558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 17594
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 16384,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x0000000000682000"
},
"time": 1566539667.1558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 17595
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2816,
"region_size": 53248,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x0000000000686000"
},
"time": 1566539667.1558,
"tid": 2420,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2816,
"type": "call",
"cid": 17596
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 1,
"families": [],
"description": "Checks adapter addresses which can be used to detect virtual network interfaces",
"severity": 2,
"marks": [
{
"call": {
"category": "network",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "GetAdaptersAddresses",
"return_value": 111,
"arguments": {
"flags": 15,
"family": 0
},
"time": 1566539606.8907,
"tid": 2820,
"flags": {}
},
"pid": 2816,
"type": "call",
"cid": 3334
}
],
"references": [],
"name": "antivm_network_adapters"
},
{
"markcount": 2,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 6.9418170052919,
"section": {
"size_of_data": "0x00031800",
"virtual_address": "0x00002000",
"entropy": 6.9418170052919,
"name": ".text",
"virtual_size": "0x000317f4"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 0.87610619469027,
"type": "generic",
"description": "Overall entropy of this PE file is high"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 1,
"families": [],
"description": "Checks for the Locally Unique Identifier on the system for a suspicious privilege",
"severity": 2,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1566539665.0938,
"tid": 2420,
"flags": {}
},
"pid": 2816,
"type": "call",
"cid": 11516
}
],
"references": [],
"name": "privilege_luid_check"
},
{
"markcount": 2,
"families": [],
"description": "Attempts to create or modify system certificates",
"severity": 3,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\8F43288AD272F3103B6FB1428485EA3014C0BCFE\\Blob",
"type": "ioc",
"description": null
},
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SystemCertificates\\AuthRoot\\Certificates\\E12DFB4B41D7D9C32B30514BAC1D81D8385E2D46\\Blob",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "modifies_certificates"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 662,
"time": 6.2341368198395,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 18302,
"time": 12.268179893494,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 20146,
"time": 46.900410890579,
"dport": 5355,
"sport": 49556
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 20466,
"time": 9.939728975296,
"dport": 5355,
"sport": 49840
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 20786,
"time": 41.491017818451,
"dport": 5355,
"sport": 50202
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 21106,
"time": 6.1808578968048,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 21434,
"time": 15.822415828705,
"dport": 5355,
"sport": 52259
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 21754,
"time": 4.1573297977448,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 22082,
"time": 6.2219069004059,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 22410,
"time": 58.483096837997,
"dport": 5355,
"sport": 54025
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 22730,
"time": 30.48111987114,
"dport": 5355,
"sport": 54237
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 23050,
"time": 4.6612739562988,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 23378,
"time": 21.25785279274,
"dport": 5355,
"sport": 54335
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 23698,
"time": 3.0446209907532,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 24026,
"time": 7.2793519496918,
"dport": 5355,
"sport": 55880
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 24346,
"time": 52.808595895767,
"dport": 5355,
"sport": 56347
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 24666,
"time": 44.152948856354,
"dport": 5355,
"sport": 56353
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 24986,
"time": 61.139678001404,
"dport": 5355,
"sport": 58651
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 25306,
"time": 27.148312807083,
"dport": 5355,
"sport": 58989
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 25626,
"time": 55.452134847641,
"dport": 5355,
"sport": 59490
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 25946,
"time": 24.504992961884,
"dport": 5355,
"sport": 59548
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 26266,
"time": 35.965322971344,
"dport": 5355,
"sport": 60071
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 26586,
"time": 49.558820009232,
"dport": 5355,
"sport": 60575
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 26906,
"time": 38.622356891632,
"dport": 5355,
"sport": 62601
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 27226,
"time": 18.623935937881,
"dport": 5355,
"sport": 63506
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 27546,
"time": 33.119617938995,
"dport": 5355,
"sport": 63646
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 27866,
"time": 13.187029838562,
"dport": 5355,
"sport": 64017
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28186,
"time": 4.6752958297729,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 47596,
"time": 4.178062915802,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 55980,
"time": 6.3025360107422,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "761a9ea08a94ac5fce9f52949f1ba26b54819da0fd79eaabfed991f7d3ab5546",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "53265dba29a44973c5f8421a12c5adccbf8c60d69c8ecac2336637c614a48bb0",
"irc": [],
"https_ex": []
}Screenshots
SegurazoService.exe removal instructions
The instructions below shows how to remove SegurazoService.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the SegurazoService.exe file for removal, restart your computer and scan it again to verify that SegurazoService.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate SegurazoService.exe in the scan result and tick the checkbox next to the SegurazoService.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate SegurazoService.exe in the scan result.



 C:\Program Files (x86)\Segurazo\SegurazoService.exe
C:\Program Files (x86)\Segurazo\SegurazoService.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If SegurazoService.exe still remains in the scan result, proceed with the next step. If SegurazoService.exe is gone from the scan result you're done.
- If SegurazoService.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that SegurazoService.exe no longer appear in the scan result.
Other files also named SegurazoService.exe
SegurazoService.exe (13 votes)
Hashes [?]
| Property | Value |
|---|---|
| MD5 | fe0bfe536948dbbc216705dc0461db30 |
| SHA256 | 3585e1d0c20276d0390ce2248bddf71387dfa270910169fa40e7c5c5c44e67bb |
Error Messages
These are some of the error messages that can appear related to segurazoservice.exe:
segurazoservice.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
segurazoservice.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
Segurazo Service has stopped working.
End Program - segurazoservice.exe. This program is not responding.
segurazoservice.exe is not a valid Win32 application.
segurazoservice.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with the file?
To help other users, please let us know what you will do with the file:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.