What is check-update.exe?
check-update.exe's description is "Update-Download-Tool" according to the check-update.exe version information.
check-update.exe is digitally signed by Aller Media e.K..
check-update.exe is usually located in the 'C:\ProgramData\Updater\' folder.
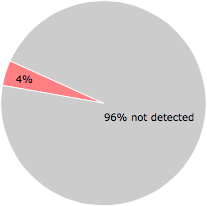
Some of the anti-virus scanners at VirusTotal detected check-update.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on check-update.exe:
| Property | Value |
|---|---|
| File description | Update-Download-Tool |
| Original filename | Setup.EXE |
| Legal copyright | Copyright (C) 2005-15 |
| Product version | 2.4.500 |
| File version | 2. 4. 500. 0 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| File description | Update-Download-Tool |
| Original filename | Setup.EXE |
| Legal copyright | Copyright (C) 2005-15 |
| Product version | 2.4.500 |
| File version | 2. 4. 500. 0 |
Digital signatures [?]
check-update.exe has a valid digital signature.
| Property | Value |
|---|---|
| Signer name | Aller Media e.K. |
| Certificate issuer name | GlobalSign Extended Validation CodeSigning CA - SHA256 - G3 |
| Certificate serial number | 722005b571e0aa4f57857efd |
VirusTotal report
3 of the 72 anti-virus programs at VirusTotal detected the check-update.exe file. That's a 4% detection rate.
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\extern.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\MaxFileSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileDirectory"
],
"dll_loaded": [
"C:\\Windows\\System32\\mswsock.dll",
"urlmon.dll",
"DNSAPI.dll",
"DHCPCSVC.DLL",
"kernel32.dll",
"UxTheme.dll",
"C:\\Windows\\system32\\ole32.dll",
"MFC42u.DLL",
"dwmapi.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Ext.dll",
"C:\\Windows\\system32\\napinsp.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"C:\\Windows\\syswow64\\MSCTF.dll",
"WININET.dll",
"KERNEL32.DLL",
"OLEAUT32.DLL",
"RASMAN.DLL",
"IPHLPAPI.DLL",
"MFC42.DLL",
"ole32.dll",
"SHLWAPI.dll",
"USER32.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"ICMP.DLL",
"rtutils.dll",
"shdocvw.dll",
"WININET.DLL",
"wininet.dll",
"shell32.dll",
"OLEAUT32.dll",
"C:\\Windows\\system32\\pnrpnsp.dll",
"SHELL32.dll",
"C:\\Windows\\System32\\winrnr.dll",
"CLBCatQ.DLL",
"comctl32.dll",
"COMCTL32.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"VERSION.dll",
"GDI32.dll",
"msi.dll",
"RICHED20.DLL",
"MSVCRT.dll",
"C:\\Windows\\SysWOW64\\oleaut32.dll",
"ADVAPI32.dll",
"rpcrt4.dll",
"SETUPAPI.dll",
"WS2_32.dll",
"COMCTL32.DLL"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"C:\\Windows\\SysWOW64\\en-US\\WININET.dll.mui",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"command_line": [
"\"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe\" ",
"\"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat\" ",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"connects_host": [
"update.am.de"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\TreatAs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InprocHandler32",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\DnsCache\\Parameters",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\DnsClient",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing\\udt_RASMANCS",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{8613E14C-D0C0-4161-AC0F-1DD2563286BC}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\udt.exe",
"HKEY_CURRENT_USER\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}",
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Microsoft.XMLDOM\\CLSID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\COM3",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Connections",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\",
"HKEY_CURRENT_USER\\Microsoft.XMLDOM",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F25E9F57-2FC8-4EB3-A41A-CCE5F08541E6}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{07EB03D6-B001-41DF-9192-BF9B841EE71F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32",
"HKEY_CURRENT_USER\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{AE6BE008-07FB-400D-8BEB-337A64F7051F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OleAut",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{C1EE01F2-B3B6-4A6A-9DDD-E988C088EC82}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellCompatibility\\Applications\\udt.exe",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\Progid",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\System\\DNSClient",
"HKEY_CURRENT_USER\\Software\\Microsoft\\CTF\\DirectSwitchHotkeys",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_CURRENT_USER\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}",
"HKEY_CURRENT_USER\\software",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InprocHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F89E9E58-BD2F-4008-9AC2-0F816C09F4EE}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\TreatAs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellCompatibility\\Applications\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{3697C5FA-60DD-4B56-92D4-74A569205C16}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{DCBD6FA8-032F-11D3-B5B1-00C04FC324A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{531FDEBF-9B4C-4A43-A2AA-960E8FCDC732}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Wpad",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{A028AE76-01B1-46C2-99C4-ACD9858AE02F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing",
"HKEY_CURRENT_USER\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{81D4E9C9-1D3B-41BC-9E6C-4B40BF79E35E}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{03B5835F-F03C-411B-9CE2-AA23E1171E36}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\FileSystem",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{E429B25A-E5D3-4D1F-9BE3-0C608477E3A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{78CB5B0E-26ED-4FCC-854C-77E8F3D1AA80}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler"
],
"resolves_host": [
"update.am.de",
"wpad",
"cuckpc"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT2.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\extern.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray2.ico",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray1.ico",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini"
],
"directory_removed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0"
],
"file_exists": [
"",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tools.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\extern.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Ext.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\http:\\update.am.de\\version.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2?",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\\"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat\"",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray.ico"
],
"mutex": [
"IESQMMUTEX_0_208",
"_UDT_Update_Download_Tool_",
"am.de-OPIF-SNUX-QCOD-TV9F-WW50-ISJ57"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\E01",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\MPIC.ini",
"C:\\Windows\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"guid": [
"{dcb00c01-570f-4a9b-8d69-199fdba5723b}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{00000000-0000-0000-c000-000000000046}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}",
"{2933bf90-7b36-11d2-b20e-00c04f983e60}",
"{dcb00000-570f-4a9b-8d69-199fdba5723b}"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Language Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\ConsoleTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}\\Enable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\EnableConsoleTracing",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\TimeOut",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\TestConnection",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\CTF\\EnableAnchorContext",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoProxyDetectType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\ProgramData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\SaferFlags",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\(Default)",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\ProxyType",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Layout Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\DefaultLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InProcServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\ConsoleTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\COM3\\Com+Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\ProgID\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\DefaultDLServer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\FileSystem\\Win31FileSystem",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\TurnOffSPIAnimations",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Srp\\GP\\RuleCount",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\ThreadingModel",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\Levels",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\NoBetaVersions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\LogFileName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InProcServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Microsoft.XMLDOM\\CLSID\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\ProxyHTTP",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadExpirationDays",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\PolicyScope",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2?",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe",
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.*",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Users",
"C:\\Windows\\System32\\ras\\*.pbk",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest"
],
"directory_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\"
]
}Dropped
[
{
"yara": [],
"sha1": "debfee4bd188671bc5102b47f3cf271d50d4564f",
"name": "784733cac3c047e2_udt.log",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"type": "ASCII text, with CRLF line terminators",
"sha256": "784733cac3c047e20d80a1d5f965d854c30ceea557977ee95d8c8ed39165d5ea",
"urls": [
"http:\/\/update.am.de\/\/"
],
"crc32": "3C15B880",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/784733cac3c047e2_udt.log",
"ssdeep": null,
"size": 328,
"sha512": "8bc0b801bab9f3f24a5a5b343368d928e2c13ec8c0d27b57b4ba0893d387d014edee8cfe95abad8e35cf6375094833129ac7baaec04333d55073524984cf2b68",
"pids": [
2500
],
"md5": "c0d8c905090a68b4360a1586dc6562c3"
},
{
"yara": [],
"sha1": "db3bd7e956b4af519a036dfa63719bfb971c75da",
"name": "e7112af15271a948_udt.log",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"type": "ASCII text, with CRLF line terminators",
"sha256": "e7112af15271a948a79e41c2e25635161b341c24515595580908bb75698f3e74",
"urls": [
"http:\/\/update.am.de\/\/"
],
"crc32": "6EBB0DC6",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/e7112af15271a948_udt.log",
"ssdeep": null,
"size": 444,
"sha512": "761c329905ae06f95c89aa26a57efcab467e88489f88d78569bf0bb2a7eef22a5216ce269dab93b224030f04e9e88b96e767811debd6d7bad769f5bd191c303a",
"pids": [
2500
],
"md5": "8622b6abf948a6e164c1ed3a3a6c9e12"
},
{
"yara": [],
"sha1": "897a8da7901d4d152005e3575169efbd996a2351",
"name": "74d2a756e04de291_udt.exe",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"type": "PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed",
"sha256": "74d2a756e04de29123800bdcba168e57a859e6fba4a6927dc85b30e676bf6ee7",
"urls": [],
"crc32": "D826DB5D",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/74d2a756e04de291_udt.exe",
"ssdeep": null,
"size": 238080,
"sha512": "3a1340466c0ec5c9dcd495a1733d45cf69b96dc634a7a184fc687d98be6a56dbd45c337582de7719234ba122bae06e36498a73b6a757075e0a083fb0b549c064",
"pids": [],
"md5": "0026755e9486c6e2424ec10956414b48"
},
{
"yara": [],
"sha1": "ecd8a820d022dfd12590551e68087048e5715c59",
"name": "2264acac265e8eef_udt.exe.manifest",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest",
"type": "XML 1.0 document, ASCII text, with CRLF line terminators",
"sha256": "2264acac265e8eef34a7d37e18292a1550ab346fdfcc9f5a262e6a2c59ac4cd6",
"urls": [],
"crc32": "DAB52ED5",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/2264acac265e8eef_udt.exe.manifest",
"ssdeep": null,
"size": 1342,
"sha512": "4ae91136fa3a53eb38b9fec4eaf1c6e2c540e462a61c4751793d4bb21e113d8a554d5e954d363cf773b4aa69ad1b160802842eb0fc706b79227ac916d740347d",
"pids": [],
"md5": "ae6a394fcd53586b0875f4b40cc511bc"
},
{
"yara": [],
"sha1": "85469548f4e8fc1eae49cf69563fbbe403a63d65",
"name": "b12b2dd9a2cb68e1_config.ini",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"type": "ASCII text, with CRLF line terminators",
"sha256": "b12b2dd9a2cb68e1df45f961bd824a7dbea85167c127a786f84e972ed65b7f37",
"urls": [],
"crc32": "5C645901",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/b12b2dd9a2cb68e1_config.ini",
"ssdeep": null,
"size": 429,
"sha512": "41f4aa461ca363c3a024c59981eb39c2896b926bb4ef3ddd024b12852cb1989663f1527654975d9333c7d8685b496b4bfcf300ccb36f79acf1ef3c7358484d8e",
"pids": [
2800,
2500
],
"md5": "ffc6c46cc9666e8aa020c6cfce7991c9"
},
{
"yara": [],
"sha1": "d92a5ac4bcd24a65ff09ae04821246ae033b4031",
"name": "e34707267db063ed_AKIDelST.bat",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"type": "ASCII text, with CRLF line terminators",
"sha256": "e34707267db063ed1d3485ad1561f41c845350597306f340106ae3640b082119",
"urls": [],
"crc32": "EC9F9D2F",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/e34707267db063ed_AKIDelST.bat",
"ssdeep": null,
"size": 852,
"sha512": "8beb69ae26b9988478aea6acc305a6c3d65d9d4ef9e78bd539202b1ed760d443464ab795c96a149fd40e8179ca83e7e3a766cc74e39279b11bf6f5e837669e3c",
"pids": [
2500,
2628
],
"md5": "1a6a51fabd912ece18a486fb04ea79b9"
},
{
"yara": [],
"sha1": "352db564e5d80bf6e70df68f1226b5a4b9fb1273",
"name": "b2199b7933227655_tray1.ico",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray1.ico",
"type": "MS Windows icon resource - 9 icons, 256x256",
"sha256": "b2199b7933227655475b64c50afe09e1db10d511a248283ddd8ee88ef794a680",
"urls": [],
"crc32": "6A4BE874",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/b2199b7933227655_tray1.ico",
"ssdeep": null,
"size": 196022,
"sha512": "fdb91e46dbdbb5b73dddc3e22241628af69cfc0eb0886651c9d4d97d3b49658032c21f8361cd04c5f155224372107d36ff92427b356d674be35b1e514c10707b",
"pids": [],
"md5": "a60b9afb2dbc13dbfcfe4172325d1712"
},
{
"yara": [],
"sha1": "633ae52483c66d1a2b8b21f2bbaef970a4068546",
"name": "c32e567d8bea4ef9_udt.ini",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"type": "XML 1.0 document, UTF-8 Unicode text, with very long lines, with CRLF line terminators",
"sha256": "c32e567d8bea4ef927a1d20483e35ebf5cae48fc950a027cb8cfd293f34572e7",
"urls": [
"http:\/\/update.am.de",
"http:\/\/update.am.de\/info"
],
"crc32": "8BDBDE78",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/c32e567d8bea4ef9_udt.ini",
"ssdeep": null,
"size": 14420,
"sha512": "9761fd30c713e1523ef85b187550fcf2f11fedba09b005cffe99e5c530a418ecda42f5fa1c23332920bdccf3e85dd99df043b5ffff377deb8a079f2ead2f0a6c",
"pids": [],
"md5": "16b2e232623fb23c988d30ddde716c31"
},
{
"yara": [],
"sha1": "bc2f4725132b2e5e67db813f53b277fb4b25fd4c",
"name": "2f5296c5fcc67f78_Tools.dll",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"type": "PE32 executable (DLL) (GUI) Intel 80386, for MS Windows",
"sha256": "2f5296c5fcc67f78cee6eadb1d87201772602f94216d19f857140e51e2f691ff",
"urls": [],
"crc32": "E92045C1",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/2f5296c5fcc67f78_Tools.dll",
"ssdeep": null,
"size": 18944,
"sha512": "987a7fd1d877cf6f0cf199fbca2a601978ac7c2d52e53c288a2544bf07b15742e694d4dd3517b0443b71a10069dc22c2d4f1506f6f21d9d0a15f4fc8231d6d9b",
"pids": [],
"md5": "c0b8010d872f15c1ff0ca8063600bc9d"
},
{
"yara": [],
"sha1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"name": "e3b0c44298fc1c14_extern.xml",
"type": "empty",
"sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"urls": [],
"crc32": "00000000",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/8824\/files\/e3b0c44298fc1c14_extern.xml",
"ssdeep": null,
"size": 0,
"sha512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e",
"md5": "d41d8cd98f00b204e9800998ecf8427e"
}
]Generic
[
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"process_name": "24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"pid": 2800,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"directory_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\"
],
"dll_loaded": [
"SETUPAPI.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"kernel32.dll",
"KERNEL32.DLL",
"MSVCRT.dll",
"rpcrt4.dll",
"SHELL32.dll",
"MFC42.DLL",
"SHLWAPI.dll",
"USER32.dll"
],
"file_opened": [
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellCompatibility\\Applications\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe"
],
"directory_removed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A5",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A6",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A7",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A1",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\E01"
],
"command_line": [
"\"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe\" ",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763.bin",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName"
]
},
"first_seen": 1597013585.65625,
"ppid": 2924
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"process_name": "udt.exe",
"pid": 2500,
"summary": {
"file_created": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\extern.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\MaxFileSize",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileDirectory"
],
"dll_loaded": [
"C:\\Windows\\System32\\mswsock.dll",
"urlmon.dll",
"DNSAPI.dll",
"DHCPCSVC.DLL",
"kernel32.dll",
"UxTheme.dll",
"C:\\Windows\\system32\\ole32.dll",
"MFC42u.DLL",
"dwmapi.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Ext.dll",
"C:\\Windows\\system32\\napinsp.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"C:\\Windows\\syswow64\\MSCTF.dll",
"WININET.dll",
"KERNEL32.DLL",
"OLEAUT32.DLL",
"RASMAN.DLL",
"IPHLPAPI.DLL",
"ole32.dll",
"SHLWAPI.dll",
"USER32.dll",
"API-MS-Win-Core-LocalRegistry-L1-1-0.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"ICMP.DLL",
"rtutils.dll",
"shdocvw.dll",
"WININET.DLL",
"wininet.dll",
"shell32.dll",
"OLEAUT32.dll",
"C:\\Windows\\system32\\pnrpnsp.dll",
"SHELL32.dll",
"C:\\Windows\\System32\\winrnr.dll",
"CLBCatQ.DLL",
"comctl32.dll",
"COMCTL32.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"VERSION.dll",
"GDI32.dll",
"msi.dll",
"RICHED20.DLL",
"MSVCRT.dll",
"C:\\Windows\\SysWOW64\\oleaut32.dll",
"ADVAPI32.dll",
"SETUPAPI.dll",
"WS2_32.dll",
"COMCTL32.DLL"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Windows\\SysWOW64\\en-US\\WININET.dll.mui",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"command_line": [
"\"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat\" ",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"connects_host": [
"update.am.de"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\TreatAs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InprocHandler32",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\DnsCache\\Parameters",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\DnsClient",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing\\udt_RASMANCS",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{8613E14C-D0C0-4161-AC0F-1DD2563286BC}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\udt.exe",
"HKEY_CURRENT_USER\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Microsoft.XMLDOM\\CLSID",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\COM3",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Connections",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\",
"HKEY_CURRENT_USER\\Microsoft.XMLDOM",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F25E9F57-2FC8-4EB3-A41A-CCE5F08541E6}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{07EB03D6-B001-41DF-9192-BF9B841EE71F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32",
"HKEY_CURRENT_USER\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{AE6BE008-07FB-400D-8BEB-337A64F7051F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\OleAut",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{C1EE01F2-B3B6-4A6A-9DDD-E988C088EC82}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\ShellCompatibility\\Applications\\udt.exe",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\Progid",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\System\\DNSClient",
"HKEY_CURRENT_USER\\Software\\Microsoft\\CTF\\DirectSwitchHotkeys",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion",
"HKEY_CURRENT_USER\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}",
"HKEY_CURRENT_USER\\software",
"HKEY_CURRENT_USER\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InprocHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{F89E9E58-BD2F-4008-9AC2-0F816C09F4EE}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\Progid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\TreatAs",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{3697C5FA-60DD-4B56-92D4-74A569205C16}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{DCBD6FA8-032F-11D3-B5B1-00C04FC324A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\Tcpip\\Parameters",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{531FDEBF-9B4C-4A43-A2AA-960E8FCDC732}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Wpad",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{A028AE76-01B1-46C2-99C4-ACD9858AE02F}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Tracing",
"HKEY_CURRENT_USER\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{81D4E9C9-1D3B-41BC-9E6C-4B40BF79E35E}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{03B5835F-F03C-411B-9CE2-AA23E1171E36}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Control\\FileSystem",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Setup",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{E429B25A-E5D3-4D1F-9BE3-0C608477E3A1}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{78CB5B0E-26ED-4FCC-854C-77E8F3D1AA80}\\Category\\Category\\{534C48C1-0607-4098-A521-4FC899C73E90}",
"HKEY_CURRENT_USER\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocHandler"
],
"resolves_host": [
"update.am.de",
"wpad",
"cuckpc"
],
"file_written": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT2.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\extern.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray2.ico",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray1.ico",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini"
],
"file_exists": [
"",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tools.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\http:\\update.am.de\\version.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\udt.log",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\extern.xml",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Ext.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\tray.ico"
],
"mutex": [
"IESQMMUTEX_0_208",
"_UDT_Update_Download_Tool_",
"am.de-OPIF-SNUX-QCOD-TV9F-WW50-ISJ57"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\MPIC.ini",
"C:\\Windows\\"
],
"guid": [
"{dcb00c01-570f-4a9b-8d69-199fdba5723b}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{00000000-0000-0000-c000-000000000046}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}",
"{2933bf90-7b36-11d2-b20e-00c04f983e60}",
"{dcb00000-570f-4a9b-8d69-199fdba5723b}"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\config.ini"
],
"regkey_read": [
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Language Hotkey",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\ProxyType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Hotkey",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\TIP\\{0000897b-83df-4b96-be07-0fb58b01c4a4}\\LanguageProfile\\0x00000000\\{0001bea3-ed56-483d-a2e2-aeae25577436}\\Enable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\DevicePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\EnableConsoleTracing",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\TimeOut",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\COM3\\Com+Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InProcServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InProcServer32\\ThreadingModel",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_CURRENT_USER\\Keyboard Layout\\Toggle\\Layout Hotkey",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\ProgID\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\DefaultDLServer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\ProgramData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Microsoft.XMLDOM\\CLSID\\(Default)",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\NoBetaVersions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Setup\\SourcePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\CTF\\EnableAnchorContext",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b5-70f9-11e8-b07b-806e6f6e6963}\\Generation",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoProxyDetectType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\FileSystem\\Win31FileSystem",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\ProxyHTTP",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{2933BF90-7B36-11D2-B20E-00C04F983E60}\\InProcServer32\\InprocServer32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadExpirationDays",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer\\TurnOffSPIAnimations",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\MountPoints2\\CPC\\Volume\\{3f5cc1b6-70f9-11e8-b07b-806e6f6e6963}\\Data",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\udt_RASAPI32\\ConsoleTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_CURRENT_USER\\Software\\UpdateDownloadTool\\FBDHAGGAGAKGNHGBNHCA\\Settings\\TestConnection",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\(Default)"
],
"directory_enumerated": [
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.*",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Windows\\System32\\ras\\*.pbk"
]
},
"first_seen": 1597013586.015625,
"ppid": 2800
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 2628,
"summary": {
"dll_loaded": [
"ADVAPI32.dll"
],
"file_opened": [
"C:\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"file_deleted": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"directory_removed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2?",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\\"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat\"",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"file_read": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\LogFileName",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\DefaultLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\SaferFlags",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\PolicyScope",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Srp\\GP\\RuleCount",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\safer\\codeidentifiers\\Levels",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2?",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.ini",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe",
"C:\\Users\\cuck",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest"
]
},
"first_seen": 1597013589.810743,
"ppid": 2500
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1597013585.328125,
"ppid": 376
}
]Signatures
[
{
"markcount": 45,
"families": [],
"description": "Command line console output was observed",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.919743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 193
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.919743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 195
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.919743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 197
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.919743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 231
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.919743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 233
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 235
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe.manifest\r\n",
"console_handle": "0x0000000b"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 253
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 269
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 271
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2?\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 273
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\A2?\r\n",
"console_handle": "0x0000000b"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 288
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 304
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 306
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.ini\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 308
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\*.ini\r\n",
"console_handle": "0x0000000b"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 324
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 338
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 340
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 342
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll\r\n",
"console_handle": "0x0000000b"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 356
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 370
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 372
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 374
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Could Not Find C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe\r\n",
"console_handle": "0x0000000b"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 388
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.935743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 402
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "if ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 404
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "exist \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 406
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "goto",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 408
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " Repeat ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 410
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 427
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "if ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 429
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "exist \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 431
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "goto",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 433
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " Repeat ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 435
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 452
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "if ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 454
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "exist \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\st.exe\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 456
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "goto",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 458
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " Repeat ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 460
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 477
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "rmdir",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 479
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 481
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "C:\\Users\\cuck\\AppData\\Local\\Temp>",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 497
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "del",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 499
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": " \"C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat\" ",
"console_handle": "0x00000007"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 501
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "The batch file cannot be found.\r\n",
"console_handle": "0x0000000b"
},
"time": 1597013589.951743,
"tid": 1576,
"flags": {}
},
"pid": 2628,
"type": "call",
"cid": 520
}
],
"references": [],
"name": "console_output"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1597013585.89025,
"tid": 856,
"flags": {}
},
"pid": 2800,
"type": "call",
"cid": 1184
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 2,
"families": [],
"description": "Drops a binary and executes it",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "dropper"
},
{
"markcount": 2,
"families": [],
"description": "Drops an executable to the user AppData folder",
"severity": 2,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"type": "ioc",
"description": null
},
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\Tools.dll",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "exe_appdata"
},
{
"markcount": 1,
"families": [],
"description": "A process created a hidden window",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "ShellExecuteExW",
"return_value": 1,
"arguments": {
"parameters": "",
"filepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"filepath_r": "C:\\Users\\cuck\\AppData\\Local\\Temp\\AKIDelST.bat",
"show_type": 0
},
"time": 1597013589.750625,
"tid": 1676,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 2091
}
],
"references": [],
"name": "stealth_window"
},
{
"markcount": 1,
"families": [],
"description": "Checks adapter addresses which can be used to detect virtual network interfaces",
"severity": 2,
"marks": [
{
"call": {
"category": "network",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "GetAdaptersAddresses",
"return_value": 111,
"arguments": {
"flags": 0,
"family": 0
},
"time": 1597013586.390625,
"tid": 1616,
"flags": {}
},
"pid": 2500,
"type": "call",
"cid": 1731
}
],
"references": [],
"name": "antivm_network_adapters"
},
{
"markcount": 1,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 7.8698123719984,
"section": {
"size_of_data": "0x00007800",
"virtual_address": "0x0003a000",
"entropy": 7.8698123719984,
"name": "UPX1",
"virtual_size": "0x00008000"
},
"type": "generic",
"description": "A section with a high entropy has been found"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 2,
"families": [],
"description": "The executable is compressed using UPX",
"severity": 2,
"marks": [
{
"section": "UPX0",
"type": "generic",
"description": "Section name indicates UPX"
},
{
"section": "UPX1",
"type": "generic",
"description": "Section name indicates UPX"
}
],
"references": [],
"name": "packer_upx"
},
{
"markcount": 1,
"families": [],
"description": "Deletes executed files from disk",
"severity": 3,
"marks": [
{
"category": "file",
"ioc": "C:\\Users\\cuck\\AppData\\Local\\Temp\\UDT-FBDHAGGAGAKGNHGBNHCA0\\udt.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "deletes_executed_files"
},
{
"markcount": 5,
"families": [],
"description": "Sets or modifies WPAD proxy autoconfiguration file for traffic interception",
"severity": 3,
"marks": [
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x00000384",
"value": 1,
"regkey_r": "WpadDecisionReason",
"reg_type": 4,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason"
},
"time": 1597013586.719625,
"tid": 1616,
"flags": {
"reg_type": "REG_DWORD"
}
},
"pid": 2500,
"type": "call",
"cid": 1754
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x00000384",
"value": "\u00e0\u0013(\u009c\u00b0n\u00d6\u0001",
"regkey_r": "WpadDecisionTime",
"reg_type": 3,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime"
},
"time": 1597013586.719625,
"tid": 1616,
"flags": {
"reg_type": "REG_BINARY"
}
},
"pid": 2500,
"type": "call",
"cid": 1755
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x00000384",
"value": 3,
"regkey_r": "WpadDecision",
"reg_type": 4,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision"
},
"time": 1597013586.719625,
"tid": 1616,
"flags": {
"reg_type": "REG_DWORD"
}
},
"pid": 2500,
"type": "call",
"cid": 1756
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExW",
"return_value": 0,
"arguments": {
"key_handle": "0x00000384",
"value": "Unidentified network",
"regkey_r": "WpadNetworkName",
"reg_type": 1,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName"
},
"time": 1597013586.719625,
"tid": 1616,
"flags": {
"reg_type": "REG_SZ"
}
},
"pid": 2500,
"type": "call",
"cid": 1757
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExW",
"return_value": 0,
"arguments": {
"key_handle": "0x00000380",
"value": "{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"regkey_r": "WpadLastNetwork",
"reg_type": 1,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork"
},
"time": 1597013586.719625,
"tid": 1616,
"flags": {
"reg_type": "REG_SZ"
}
},
"pid": 2500,
"type": "call",
"cid": 1825
}
],
"references": [],
"name": "modifies_proxy_wpad"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.076781988143921,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6082,
"time": 2.604609966278076,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6402,
"time": 1.0336859226226807,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6730,
"time": 3.016084909439087,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7058,
"time": 1.5354928970336914,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7386,
"time": -0.09317302703857422,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7714,
"time": 3.0271899700164795,
"dport": 5355,
"sport": 55880
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8042,
"time": 1.5631098747253418,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 23194,
"time": 1.0666978359222412,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 31578,
"time": 3.0933918952941895,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "ba10f0b8a7765b9b060a265f91e9177a0fe419ef770d20619bc6c8f28f4316e1",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "d80e3a36c470cf233dfc0e924349245f616da0315ce626994e820c6ae97d59a4",
"irc": [],
"https_ex": []
}Screenshots
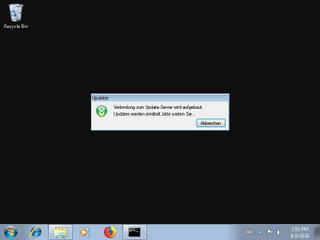
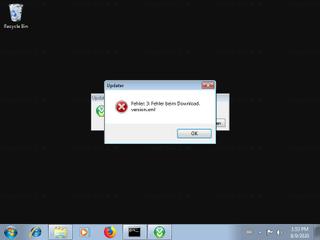
check-update.exe removal instructions
The instructions below shows how to remove check-update.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the check-update.exe file for removal, restart your computer and scan it again to verify that check-update.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate check-update.exe in the scan result and tick the checkbox next to the check-update.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate check-update.exe in the scan result.



 C:\ProgramData\Updater\check-update.exe
C:\ProgramData\Updater\check-update.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If check-update.exe still remains in the scan result, proceed with the next step. If check-update.exe is gone from the scan result you're done.
- If check-update.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that check-update.exe no longer appear in the scan result.
Other files also named check-update.exe
check-update.exe (4 votes)
Hashes [?]
| Property | Value |
|---|---|
| MD5 | adf1d0ce297563401b72dd4440546467 |
| SHA256 | 24fe8f56376d5bb6fd433c9ed0f3b1a43929351756be312d2690310882096763 |
Error Messages
These are some of the error messages that can appear related to check-update.exe:
check-update.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
check-update.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
Update-Download-Tool has stopped working.
End Program - check-update.exe. This program is not responding.
check-update.exe is not a valid Win32 application.
check-update.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with the file?
To help other users, please let us know what you will do with the file:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.