What is cpmmm.exe?
cpmmm.exe is part of YDAIS and developed by YD according to the cpmmm.exe version information.
cpmmm.exe's description is "YDAISV3"
cpmmm.exe is usually located in the 'c:\downloads\' folder.
Some of the anti-virus scanners at VirusTotal detected cpmmm.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Vendor and version information [?]
The following is the available information on cpmmm.exe:
| Property | Value |
|---|---|
| Product name | YDAIS |
| Company name | YD |
| File description | YDAISV3 |
| Internal name | AloulouJikou.exe |
| Original filename | AloulouJikou.exe |
| Comments | Y |
| Legal copyright | Copyright © 6488 |
| Product version | 6.4.4.6 |
| File version | 6.4.4.6 |
Here's a screenshot of the file properties when displayed by Windows Explorer:
| Product name | YDAIS |
| Company name | YD |
| File description | YDAISV3 |
| Internal name | AloulouJikou.exe |
| Original filename | AloulouJikou.exe |
| Comments | Y |
| Legal copyright | Copyright © 6488 |
| Product version | 6.4.4.6 |
| File version | 6.4.4.6 |
Digital signatures [?]
cpmmm.exe is not signed.
VirusTotal report
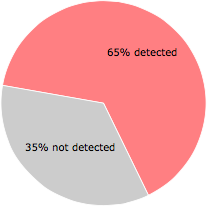
42 of the 65 anti-virus programs at VirusTotal detected the cpmmm.exe file. That's a 65% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| Ad-Aware | Adware.Temonde.2.Gen |
| AhnLab-V3 | PUP/Win32.Temonde.R238478 |
| Arcabit | Adware.Temonde.2.Gen |
| Avast | Win32:MalwareX-gen [Trj] |
| AVG | Win32:MalwareX-gen [Trj] |
| Avira | TR/Dropper.Gen |
| BitDefender | Adware.Temonde.2.Gen |
| Comodo | TrojWare.MSIL.Crypt.ML@81lvv2 |
| CrowdStrike | malicious_confidence_90% (W) |
| Cybereason | malicious.a72ce9 |
| Cylance | Unsafe |
| Cyren | W32/S-bd01f5bc!Eldorado |
| Emsisoft | Adware.Temonde.2.Gen (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | a variant of MSIL/Kryptik.LML |
| Fortinet | MSIL/Kryptik.KZF!tr |
| GData | Win32.Application.Kryptik.LQ |
| Ikarus | Trojan.MSIL.Crypt |
| Invincea | heuristic |
| K7AntiVirus | Trojan ( 005450931 ) |
| K7GW | Trojan ( 005450931 ) |
| Kaspersky | HEUR:Trojan.Win32.Generic |
| Malwarebytes | Adware.Csdimonetize |
| MAX | malware (ai score=67) |
| McAfee | Csdimonetize |
| McAfee-GW-Edition | BehavesLike.Win32.Generic.jh |
| Microsoft | SoftwareBundler:MSIL/Wizrem!bit |
| MicroWorld-eScan | Adware.Temonde.2.Gen |
| NANO-Antivirus | Trojan.Win32.Kryptik.fnfeux |
| Paloalto | generic.ml |
| Panda | Trj/GdSda.A |
| Qihoo-360 | HEUR/QVM03.0.5886.Malware.Gen |
| Rising | Dropper.Generic!8.35E (CLOUD) |
| SentinelOne | static engine - malicious |
| Sophos | Troj/Kryptik-JC |
| Symantec | ML.Attribute.HighConfidence |
| Tencent | Win32.Trojan.Generic.Aljc |
| Trapmine | malicious.moderate.ml.score |
| VIPRE | Trojan.Win32.Generic!BT |
| Webroot | W32.Adware.Gen |
| ZoneAlarm | HEUR:Trojan.Win32.Generic |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"file_recreated": [
"\\Device\\KsecDD"
],
"dll_loaded": [
"AdvApi32.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorwks.dll",
"ntdll",
"bcrypt.dll",
"shell32.dll",
"RpcRtRemote.dll",
"mscoree.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorjit.dll",
"kernel32.dll",
"gdi32.dll",
"advapi32.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\ole32.dll",
"C:\\Windows\\system32\\IMM32.DLL",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\bcrypt.dll",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\mscorlib\\9469491f37d9c35b596968b206615309\\mscorlib.ni.dll",
"ADVAPI32.dll",
"ole32.dll",
"SHLWAPI.dll",
"CRYPTSP.dll"
],
"file_opened": [
"C:\\Windows\\",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sorttbls.nlp",
"C:\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\",
"C:\\Windows\\System32\\l_intl.nls",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\index143.dat",
"C:\\Users\\cuck\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\",
"C:\\Users\\",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\",
"C:\\Users\\cuck\\AppData\\Local\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sortkey.nlp",
"C:\\Users\\cuck\\AppData\\",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\53f2c052\\5fff19b8",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\LocalIntranet",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\GACChangeNotification\\Default",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework\\Policy\\Standards",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\Upgrades",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards\\v2.0.50727",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\v2.0.50727\\Security\\Policy",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\StrongName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\v2.0",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\Internet",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\internal\\jit\\Perf",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\AppPatch",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\Standards"
],
"file_deleted": [
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config.cch.2740.15696984",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config.cch.2740.15696984",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config.cch.2740.15697156"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.config",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\msvcr80.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Windows\\Globalization\\en-us.nlp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\fusion.localgac",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"C:\\Windows\\System32\\MSCOREE.DLL.local"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config.cch",
"C:\\Windows\\Microsoft.NET\\Framework64\\Upgrades.2.0.50727\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config.cch",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config.cch"
],
"file_read": [
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeInline",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\EvalationData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\OnlyUseLatestCLR",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LoggingLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStart",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStartAtJit",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigString",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\CacheLocation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TailCallOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogResourceBinds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\DisabledSessions\\GlobalSession",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ILDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogFailures",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\mscorlib,2.0.0.0,,b77a5c561934e089,AMD64",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy\\Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\EnableLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CLRLoadLogDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Strong Cryptographic Provider\\Image Path",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MVID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\DisabledProcesses\\D48EBF9C",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\MachineGuid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\NewGCCalc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\DisabledSessions\\MachineThrottling",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\UseLegacyIdentityFormat",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\ForceLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeCalliOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\Extensions\\RemoteRpcDll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CseOn",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\LatestIndex",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\InstallRoot",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{00000134-0000-0000-C000-000000000046}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableHotCold",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\Extensions\\NdrOleExtDLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\ILUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TURNOFFDEBUGINFO",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\DevOverrideEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\VersioningLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DisableMSIPeek",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\LoadAppInit_DLLs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NoClientChecks",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DownloadCacheQuotaInKB",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Strong Cryptographic Provider\\Type",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\NIUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableConfigCache"
]
}Generic
[
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"process_name": "54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"pid": 2740,
"summary": {
"file_recreated": [
"\\Device\\KsecDD"
],
"dll_loaded": [
"AdvApi32.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorwks.dll",
"ntdll",
"bcrypt.dll",
"shell32.dll",
"RpcRtRemote.dll",
"mscoree.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\mscorjit.dll",
"kernel32.dll",
"gdi32.dll",
"advapi32.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\ole32.dll",
"C:\\Windows\\system32\\IMM32.DLL",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\bcrypt.dll",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\mscorlib\\9469491f37d9c35b596968b206615309\\mscorlib.ni.dll",
"ADVAPI32.dll",
"ole32.dll",
"SHLWAPI.dll",
"CRYPTSP.dll"
],
"file_opened": [
"C:\\Windows\\",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sorttbls.nlp",
"C:\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\",
"C:\\Windows\\System32\\l_intl.nls",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"C:\\Windows\\assembly\\NativeImages_v2.0.50727_64\\index143.dat",
"C:\\Users\\cuck\\",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\",
"C:\\Users\\",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\",
"C:\\Users\\cuck\\AppData\\Local\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Windows\\assembly\\GAC_64\\mscorlib\\2.0.0.0__b77a5c561934e089\\sortkey.nlp",
"C:\\Users\\cuck\\AppData\\",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\53f2c052\\5fff19b8",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\LocalIntranet",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\GACChangeNotification\\Default",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework\\Policy\\Standards",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\Upgrades",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\standards\\v2.0.50727",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\v2.0.50727\\Security\\Policy",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\StrongName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\v2.0",
"HKEY_CURRENT_USER\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Security\\Policy\\Extensions\\NamedPermissionSets\\Internet",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\internal\\jit\\Perf",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\Policy\\AppPatch",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\.NETFramework\\Policy\\Standards"
],
"file_deleted": [
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config.cch.2740.15696984",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config.cch.2740.15696984",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config.cch.2740.15697156"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.config",
"C:\\Windows\\winsxs\\amd64_microsoft.vc80.crt_1fc8b3b9a1e18e3b_8.0.50727.4940_none_88df89932faf0bf6\\msvcr80.dll",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config",
"C:\\Windows\\Globalization\\en-us.nlp",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\fusion.localgac",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin",
"C:\\Windows\\System32\\MSCOREE.DLL.local"
],
"file_failed": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e.bin.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config.cch",
"C:\\Windows\\Microsoft.NET\\Framework64\\Upgrades.2.0.50727\\",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\CLR Security Config\\v2.0.50727.312\\64bit\\security.config.cch",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\enterprisesec.config",
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\security.config.cch"
],
"file_read": [
"C:\\Windows\\Microsoft.NET\\Framework64\\v2.0.50727\\CONFIG\\machine.config"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeInline",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\EvalationData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\OnlyUseLatestCLR",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LoggingLevel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStart",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MissingDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\NIDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\GCStressStartAtJit",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigString",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\CacheLocation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TailCallOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\SIG",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogResourceBinds",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\DisabledSessions\\GlobalSession",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ILDependencies",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\LogFailures",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\GACChangeNotification\\Default\\mscorlib,2.0.0.0,,b77a5c561934e089,AMD64",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\FipsAlgorithmPolicy\\Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\EnableLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CLRLoadLogDir",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\ConfigMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Strong Cryptographic Provider\\Image Path",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\MVID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\DisabledProcesses\\D48EBF9C",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\MachineGuid",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\NewGCCalc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\DisabledSessions\\MachineThrottling",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\UseLegacyIdentityFormat",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\ForceLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\PInvokeCalliOpt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\Extensions\\RemoteRpcDll",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\CseOn",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\LatestIndex",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\InstallRoot",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\LastModTime",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Interface\\{00000134-0000-0000-C000-000000000046}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableHotCold",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\Extensions\\NdrOleExtDLL",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\ILUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\TURNOFFDEBUGINFO",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\DevOverrideEnable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\DisplayName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\VersioningLog",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DisableMSIPeek",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\LoadAppInit_DLLs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NoClientChecks",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\DownloadCacheQuotaInKB",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\IL\\7950e2c5\\19b8f67f\\82\\Modules",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\NI\\181938c6\\7950e2c5\\82\\Status",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\Defaults\\Provider\\Microsoft Strong Cryptographic Provider\\Type",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Fusion\\NativeImagesIndex\\v2.0.50727_64\\index143\\NIUsageMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\.NETFramework\\DisableConfigCache"
]
},
"first_seen": 1605808388.578125,
"ppid": 1664
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1605808388.328125,
"ppid": 376
}
]Signatures
[
{
"markcount": 1,
"families": [],
"description": "Checks if process is being debugged by a debugger",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741700,
"api": "IsDebuggerPresent",
"return_value": 0,
"arguments": {},
"time": 1605808388.953125,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 373
}
],
"references": [],
"name": "checks_debugger"
},
{
"markcount": 1,
"families": [],
"description": "Collects information to fingerprint the system (MachineGuid, DigitalProductId, SystemBiosDate)",
"severity": 1,
"marks": [
{
"category": "registry",
"ioc": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Cryptography\\MachineGuid",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "recon_fingerprint"
},
{
"markcount": 1,
"families": [],
"description": "This executable has a PDB path",
"severity": 1,
"marks": [
{
"category": "pdb_path",
"ioc": "C:\\Users\\AymenTLILI\\source\\repos\\WindowsFormsApp2\\WindowsFormsApp2\\obj\\Release\\AloulouJikou.pdb",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "has_pdb"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1605808389.156125,
"tid": 2436,
"flags": {}
},
"pid": 2740,
"type": "call",
"cid": 475
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 38,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feef821000"
},
"time": 1605808388.844125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 254
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9e000"
},
"time": 1605808388.906125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 329
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9e000"
},
"time": 1605808388.906125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 331
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 385
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 387
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 389
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 391
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 393
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 395
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 397
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9f000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 399
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 401
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 403
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 405
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1605808388.953125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 407
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa0000"
},
"time": 1605808388.969125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 409
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1605808388.969125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 411
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1605808388.969125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 413
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1605808388.969125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 415
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefaa1000"
},
"time": 1605808388.969125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 417
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"length": 4096,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"base_address": "0x000007feefa9e000"
},
"time": 1605808388.969125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE"
}
},
"pid": 2740,
"type": "call",
"cid": 419
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00022000"
},
"time": 1605808389.188125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 539
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 589824,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 1056768,
"base_address": "0x000007fffff20000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_RESERVE|MEM_TOP_DOWN"
}
},
"pid": 2740,
"type": "call",
"cid": 580
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007fffff20000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 581
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007fffff20000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 582
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 65536,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 1056768,
"base_address": "0x000007fffff10000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_RESERVE|MEM_TOP_DOWN"
}
},
"pid": 2740,
"type": "call",
"cid": 583
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007fffff10000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 584
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff000da000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 585
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00012000"
},
"time": 1605808389.235125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 586
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00023000"
},
"time": 1605808389.297125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 604
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff000ea000"
},
"time": 1605808389.297125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 613
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00112000"
},
"time": 1605808389.297125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 614
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff000ed000"
},
"time": 1605808389.297125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 615
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0002c000"
},
"time": 1605808389.328125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 656
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff00160000"
},
"time": 1605808389.375125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 703
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff000db000"
},
"time": 1605808389.375125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 708
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff000d2000"
},
"time": 1605808389.516125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 779
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2740,
"region_size": 4096,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 4096,
"base_address": "0x000007ff0003f000"
},
"time": 1605808389.578125,
"tid": 2436,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT"
}
},
"pid": 2740,
"type": "call",
"cid": 810
}
],
"references": [],
"name": "allocates_rwx"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 546,
"time": 3.110944986343384,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 5226,
"time": 9.14074993133545,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7070,
"time": 3.0209429264068604,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7398,
"time": 1.0197160243988037,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7726,
"time": 3.0678510665893555,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8054,
"time": 1.5197241306304932,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 8382,
"time": -0.10159087181091309,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 8710,
"time": 1.546739101409912,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28120,
"time": 1.05281400680542,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 36504,
"time": 3.1120049953460693,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "132c2617babbcd059a48f464d084462b9d7f727523a2df5f91e7416f29bf0051",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "ef26938b03e8612ba4e7eac11e266298d3f8186b84bcc7e5ce05a0b8f1207fe2",
"irc": [],
"https_ex": []
}Screenshots
cpmmm.exe removal instructions
The instructions below shows how to remove cpmmm.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the cpmmm.exe file for removal, restart your computer and scan it again to verify that cpmmm.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate cpmmm.exe in the scan result and tick the checkbox next to the cpmmm.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate cpmmm.exe in the scan result.



 c:\downloads\cpmmm.exe
c:\downloads\cpmmm.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If cpmmm.exe still remains in the scan result, proceed with the next step. If cpmmm.exe is gone from the scan result you're done.
- If cpmmm.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that cpmmm.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | 7bc8102a72ce90be757699084f1499c2 |
| SHA256 | 54e36b4cab0a5b5cd61ec50a954630e9439365dc4339575474200157c098916e |
Error Messages
These are some of the error messages that can appear related to cpmmm.exe:
cpmmm.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
cpmmm.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
YDAISV3 has stopped working.
End Program - cpmmm.exe. This program is not responding.
cpmmm.exe is not a valid Win32 application.
cpmmm.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with cpmmm.exe?
To help other users, please let us know what you will do with cpmmm.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.