What is devobj.exe?
devobj.exe is usually located in the 'C:\ProgramData\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\' folder.
Some of the anti-virus scanners at VirusTotal detected devobj.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Digital signatures [?]
devobj.exe is not signed.
VirusTotal report
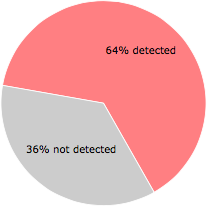
46 of the 72 anti-virus programs at VirusTotal detected the devobj.exe file. That's a 64% detection rate.
| Scanner | Detection Name |
|---|---|
| Acronis | suspicious |
| Ad-Aware | Trojan.GenericKD.32026192 |
| AegisLab | Trojan.Multi.Generic.4!c |
| AhnLab-V3 | Trojan/Win32.Autoit.C3278870 |
| Alibaba | Trojan:Win32/Scar.2d60b95a |
| ALYac | Trojan.GenericKD.32026192 |
| APEX | Malicious |
| Arcabit | Trojan.Generic.D1E8AE50 |
| Avast | Win32:Malware-gen |
| AVG | Win32:Malware-gen |
| Avira | HEUR/AGEN.1000356 |
| BitDefender | Trojan.GenericKD.32026192 |
| Comodo | Malware@#2v81q7op4atdk |
| CrowdStrike | win/malicious_confidence_60% (W) |
| Cybereason | malicious.9ac481 |
| Cylance | Unsafe |
| DrWeb | Trojan.Siggen8.30453 |
| Emsisoft | Trojan.GenericKD.32026192 (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | a variant of Win32/Packed.AutoIt.KY |
| F-Secure | Heuristic.HEUR/AGEN.1000356 |
| FireEye | Generic.mg.ca69a4854834e243 |
| Fortinet | W32/PossibleThreat |
| GData | Win32.Trojan.QuilMiner.B8J0UY |
| Ikarus | Trojan-Spy.HawkEye |
| Invincea | heuristic |
| K7AntiVirus | Trojan ( 700000111 ) |
| K7GW | Trojan ( 700000111 ) |
| Kaspersky | Trojan.Win32.Scar.satl |
| McAfee | Artemis!CA69A4854834 |
| McAfee-GW-Edition | BehavesLike.Win32.Downloader.th |
| Microsoft | PUA:Win32/Puamson.A!ml |
| MicroWorld-eScan | Trojan.GenericKD.32026192 |
| NANO-Antivirus | Trojan.Win32.Mlw.fqtprv |
| Paloalto | generic.ml |
| Panda | Trj/CI.A |
| Qihoo-360 | HEUR/QVM41.2.8DC3.Malware.Gen |
| Rising | Trojan.Win32.Agent_.rm (CLASSIC) |
| SentinelOne | DFI - Suspicious PE |
| Sophos | Mal/Generic-S |
| Symantec | Trojan.Gen.MBT |
| Tencent | Win32.Trojan.Scar.Szlh |
| TrendMicro | TROJ_GEN.R002C0WF119 |
| TrendMicro-HouseCall | TROJ_GEN.R002C0WF119 |
| Webroot | W32.Malware.Gen |
| ZoneAlarm | Trojan.Win32.Scar.satl |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"guid": [
"{00020400-0000-0000-c000-000000000046}",
"{0f87369f-a4e5-4cfc-bd3e-73e6154572dd}"
],
"directory_created": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"dll_loaded": [
"ntmarta.dll",
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"SXS.DLL",
"XmlLite.dll",
"ADVAPI32.dll",
"kernel32.dll",
"UxTheme.dll",
"SspiCli.dll",
"rpcrt4.dll",
"dwmapi.dll",
"comctl32",
"comctl32.dll",
"CLBCatQ.DLL",
"IMM32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Windows\\SysWOW64\\taskschd.dll",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\ProgramData\\",
"C:\\Windows\\SysWOW64\\stdole2.tlb",
"C:\\Windows\\SysWOW64\\en-US\\icacls.exe.mui",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"file_read": [
"C:\\Windows\\SysWOW64\\taskschd.dll",
"C:\\Windows\\SysWOW64\\stdole2.tlb"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\0\\win32",
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\9",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\COM3",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Schedule.Service\\CLSID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0\\0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\TreatAs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0\\0\\win32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\Progid",
"HKEY_CURRENT_USER\\Schedule.Service",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_CURRENT_USER\\Software\\AutoIt v3\\AutoIt",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\LSA\\AccessProviders",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\409",
"HKEY_CURRENT_USER\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocHandler32",
"HKEY_CURRENT_USER\\Control Panel\\Mouse",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\LDAP",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor",
"HKEY_CURRENT_USER\\TypeLib",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855",
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"mutex": [
"1FFRitFm5rP5oY5aeTeDikpQiWRz278L459206376147clipperrorRCRF3C674E"
],
"file_failed": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"command_line": [
"icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" ",
"C:\\Windows\\system32\\cmd.exe \/c icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\"",
"icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\"",
"icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" "
],
"file_moved": [
[
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe"
]
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Schedule.Service\\CLSID\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\PreferredUILanguages",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\AlternateCodePage",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\COM3\\Com+Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language\\InstallLanguageFallback",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0\\0\\win32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\MuiCached\\MachinePreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\EMPTY",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\ProgID\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\0\\win32\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\Mouse\\SwapMouseButtons",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\Type",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32\\ThreadingModel",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\Python27\\icacls",
"C:\\Python27\\Scripts\\icacls.*",
"C:\\Users\\cuck\\AppData",
"C:\\Windows\\System32\\icacls.COM",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\icacls",
"C:\\Windows\\System32\\icacls.*",
"C:\\Windows\\System32\\icacls.exe",
"C:\\Python27\\Scripts\\icacls",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\*.*",
"C:\\Users\\cuck",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\",
"C:\\Users",
"C:\\Python27\\icacls.*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\icacls.*",
"C:\\Users\\cuck\\AppData\\Local"
]
}Generic
[
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"process_name": "3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"pid": 2660,
"summary": {
"directory_created": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"dll_loaded": [
"SXS.DLL",
"XmlLite.dll",
"ADVAPI32.dll",
"kernel32.dll",
"UxTheme.dll",
"SspiCli.dll",
"rpcrt4.dll",
"dwmapi.dll",
"comctl32",
"comctl32.dll",
"CLBCatQ.DLL",
"IMM32.dll"
],
"file_opened": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\Windows\\SysWOW64\\taskschd.dll",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\ProgramData\\",
"C:\\Windows\\SysWOW64\\stdole2.tlb",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"file_read": [
"C:\\Windows\\SysWOW64\\taskschd.dll",
"C:\\Windows\\SysWOW64\\stdole2.tlb"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Schedule.Service",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\0\\win32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\COM3",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Schedule.Service\\CLSID",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0\\0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\TreatAs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0\\0\\win32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\CTF\\Compatibility\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_CURRENT_USER\\Software\\AutoIt v3\\AutoIt",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\9",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\409",
"HKEY_CURRENT_USER\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocHandler",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocHandler32",
"HKEY_CURRENT_USER\\Control Panel\\Mouse",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\Progid",
"HKEY_CURRENT_USER\\TypeLib",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0"
],
"command_line": [
"C:\\Windows\\system32\\cmd.exe \/c icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\""
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe"
],
"mutex": [
"1FFRitFm5rP5oY5aeTeDikpQiWRz278L459206376147clipperrorRCRF3C674E"
],
"guid": [
"{00020400-0000-0000-c000-000000000046}",
"{0f87369f-a4e5-4cfc-bd3e-73e6154572dd}"
],
"file_moved": [
[
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe"
]
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{00020430-0000-0000-C000-000000000046}\\2.0\\0\\win32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\TypeLib\\{E34CB9F1-C7F7-424C-BE29-027DCC09363A}\\1.0\\0\\win32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Schedule.Service\\CLSID\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\Mouse\\SwapMouseButtons",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\COM3\\Com+Enabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\ProgID\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{0F87369F-A4E5-4CFC-BD3E-73E6154572DD}\\InprocServer32\\ThreadingModel"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\",
"C:\\Users\\cuck\\AppData",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\*.*",
"C:\\Users\\cuck",
"C:\\Users",
"C:\\Users\\cuck\\AppData\\Local"
]
},
"first_seen": 1563947584.5938,
"ppid": 1624
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 1676,
"summary": {
"dll_loaded": [
"kernel32.dll"
],
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"command_line": [
"icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" ",
"icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\"",
"icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" "
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar"
],
"directory_enumerated": [
"C:\\Python27\\icacls",
"C:\\Python27\\Scripts\\icacls.*",
"C:\\Users\\cuck\\AppData",
"C:\\Windows\\System32\\icacls.COM",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\icacls",
"C:\\Windows\\System32\\icacls.*",
"C:\\Windows\\System32\\icacls.exe",
"C:\\Python27\\Scripts\\icacls",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Users",
"C:\\Python27\\icacls.*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\icacls.*",
"C:\\Users\\cuck\\AppData\\Local"
]
},
"first_seen": 1563947585.1875,
"ppid": 2660
},
{
"process_path": "C:\\Windows\\SysWOW64\\icacls.exe",
"process_name": "icacls.exe",
"pid": 2700,
"summary": {
"dll_loaded": [
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"ntmarta.dll",
"rpcrt4.dll"
],
"file_opened": [
"C:\\ProgramData\\",
"C:\\Windows\\SysWOW64\\en-US\\icacls.exe.mui",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\LDAP",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\LSA\\AccessProviders",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc"
],
"file_exists": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"file_failed": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language\\InstallLanguageFallback",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\PreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\Type",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\AlternateCodePage",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\MuiCached\\MachinePreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\EMPTY",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName"
]
},
"first_seen": 1563947585.8594,
"ppid": 1676
},
{
"process_path": "C:\\Windows\\SysWOW64\\icacls.exe",
"process_name": "icacls.exe",
"pid": 2508,
"summary": {
"dll_loaded": [
"ntmarta.dll"
],
"file_opened": [
"C:\\ProgramData\\",
"C:\\Windows\\SysWOW64\\en-US\\icacls.exe.mui",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\LDAP",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\LSA\\AccessProviders"
],
"file_exists": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"file_failed": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language\\InstallLanguageFallback",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\PreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\Type",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\AlternateCodePage",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\MuiCached\\MachinePreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\EMPTY",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity"
]
},
"first_seen": 1563947585.625,
"ppid": 1676
},
{
"process_path": "C:\\Windows\\SysWOW64\\icacls.exe",
"process_name": "icacls.exe",
"pid": 344,
"summary": {
"file_opened": [
"C:\\ProgramData\\",
"C:\\Windows\\SysWOW64\\en-US\\icacls.exe.mui",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855",
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe"
],
"file_exists": [
"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Services\\LDAP",
"HKEY_LOCAL_MACHINE\\System\\CurrentControlSet\\Control\\LSA\\AccessProviders"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language\\InstallLanguageFallback",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\PreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\Type",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\MUI\\UILanguages\\en-US\\AlternateCodePage",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\MuiCached\\MachinePreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\EMPTY",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity"
],
"dll_loaded": [
"ntmarta.dll"
]
},
"first_seen": 1563947585.4375,
"ppid": 1676
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1563947584.3125,
"ppid": 376
}
]Signatures
[
{
"markcount": 4,
"families": [],
"description": "Queries for the computername",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1563947584.8598,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 675
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1563947585.0938,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 916
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1563947585.1247,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 940
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1563947585.1247,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 944
}
],
"references": [],
"name": "antivm_queries_computername"
},
{
"markcount": 1,
"families": [],
"description": "Checks if process is being debugged by a debugger",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "IsDebuggerPresent",
"return_value": 0,
"arguments": {},
"time": 1563947584.7188,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 67
}
],
"references": [],
"name": "checks_debugger"
},
{
"markcount": 6,
"families": [],
"description": "Command line console output was observed",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "processed file: C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\r\n",
"console_handle": "0x00000007"
},
"time": 1563947585.5155,
"tid": 1616,
"flags": {}
},
"pid": 344,
"type": "call",
"cid": 119
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Successfully processed 1 files; Failed processing 0 files\r\n",
"console_handle": "0x00000007"
},
"time": 1563947585.5155,
"tid": 1616,
"flags": {}
},
"pid": 344,
"type": "call",
"cid": 121
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "processed file: C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\r\n",
"console_handle": "0x00000007"
},
"time": 1563947585.766,
"tid": 2628,
"flags": {}
},
"pid": 2508,
"type": "call",
"cid": 112
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Successfully processed 1 files; Failed processing 0 files\r\n",
"console_handle": "0x00000007"
},
"time": 1563947585.766,
"tid": 2628,
"flags": {}
},
"pid": 2508,
"type": "call",
"cid": 114
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "processed file: C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\r\n",
"console_handle": "0x00000007"
},
"time": 1563947585.9374,
"tid": 3048,
"flags": {}
},
"pid": 2700,
"type": "call",
"cid": 137
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Successfully processed 1 files; Failed processing 0 files\r\n",
"console_handle": "0x00000007"
},
"time": 1563947585.9374,
"tid": 3048,
"flags": {}
},
"pid": 2700,
"type": "call",
"cid": 139
}
],
"references": [],
"name": "console_output"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1563947584.8598,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 669
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 2,
"families": [],
"description": "The file contains an unknown PE resource name possibly indicative of a packer",
"severity": 1,
"marks": [
{
"category": "resource name",
"ioc": "COMULATIVE",
"type": "ioc",
"description": null
},
{
"category": "resource name",
"ioc": "FASTCON",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_unknown_resource_name"
},
{
"markcount": 1,
"families": [],
"description": "Foreign language identified in PE resource",
"severity": 2,
"marks": [
{
"name": "RT_BITMAP",
"language": "LANG_CHINESE",
"offset": "0x00168274",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_TRADITIONAL",
"type": "generic",
"size": "0x00000bb6"
}
],
"references": [],
"name": "origin_langid"
},
{
"markcount": 1,
"families": [],
"description": "Creates a suspicious process",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "C:\\Windows\\system32\\cmd.exe \/c icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\"",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_process"
},
{
"markcount": 1,
"families": [],
"description": "Moves the original executable to a new location",
"severity": 2,
"marks": [
{
"call": {
"category": "file",
"status": 1,
"stacktrace": [],
"api": "MoveFileWithProgressW",
"return_value": 1,
"arguments": {
"oldfilepath": "C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin",
"newfilepath": "C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe",
"newfilepath_r": "C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\\devobj.exe",
"flags": 2,
"oldfilepath_r": "C:\\Users\\cuck\\AppData\\Local\\Temp\\3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a.bin"
},
"time": 1563947584.8277,
"tid": 2308,
"flags": {}
},
"pid": 2660,
"type": "call",
"cid": 460
}
],
"references": [],
"name": "moves_self"
},
{
"markcount": 2,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 6.8186304525398,
"section": {
"size_of_data": "0x000c5a00",
"virtual_address": "0x000c8000",
"entropy": 6.8186304525398,
"name": ".rsrc",
"virtual_size": "0x000c586f"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 0.49437148217636,
"type": "generic",
"description": "Overall entropy of this PE file is high"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 4,
"families": [],
"description": "Uses suspicious command line tools or Windows utilities",
"severity": 3,
"marks": [
{
"category": "cmdline",
"ioc": "icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" ",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "C:\\Windows\\system32\\cmd.exe \/c icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-5-7:(R,REA,RA,RD)\" & icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\"",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"cuck:(R,REA,RA,RD)\"",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "icacls \"C:\\ProgramData\\amd64_microsoft-windows-s..nsentverifier-winrt_31bf3856ad364e35_10.0.17134.1_none_d10bec548645d855\" \/inheritance:e \/deny \"*S-1-1-0:(R,REA,RA,RD)\" ",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_command_tools"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 662,
"time": 6.1114599704742,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 5694,
"time": 6.0447521209717,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6022,
"time": 4.0519840717316,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6350,
"time": 6.0677711963654,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 6678,
"time": 4.7603170871735,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 7006,
"time": 2.944099187851,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 7334,
"time": 4.6896860599518,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 20274,
"time": 4.1542360782623,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 28658,
"time": 6.1428141593933,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "c7d15c13d4fec23557c6ae14dc5df940e3cee49b4d0851c9ed6e83538247ee68",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "a5d5066a858097d2d7a645b7b9d43becdccd51dc276251b2e60c5aaad5cc1d37",
"irc": [],
"https_ex": []
}Screenshots
devobj.exe removal instructions
The instructions below shows how to remove devobj.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the devobj.exe file for removal, restart your computer and scan it again to verify that devobj.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate devobj.exe in the scan result and tick the checkbox next to the devobj.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate devobj.exe in the scan result.



 C:\ProgramData\amd64_microsoft..35_10.0.17134.1_none_d10bec548645d855\devobj.exe
C:\ProgramData\amd64_microsoft..35_10.0.17134.1_none_d10bec548645d855\devobj.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If devobj.exe still remains in the scan result, proceed with the next step. If devobj.exe is gone from the scan result you're done.
- If devobj.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that devobj.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | ca69a4854834e2432ad203acd7286703 |
| SHA256 | 3715377ba67e21b06bf7c9c9bc4cd00686c8b7043bb4d54ee3bf72eec4a91f0a |
Error Messages
These are some of the error messages that can appear related to devobj.exe:
devobj.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
devobj.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
devobj.exe has stopped working.
End Program - devobj.exe. This program is not responding.
devobj.exe is not a valid Win32 application.
devobj.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with devobj.exe?
To help other users, please let us know what you will do with devobj.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.