What is svchosa.exe?
svchosa.exe is usually located in the 'c:\downloads\' folder.
Some of the anti-virus scanners at VirusTotal detected svchosa.exe.
If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page.
Digital signatures [?]
svchosa.exe is not signed.
VirusTotal report
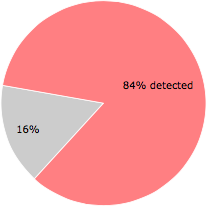
61 of the 73 anti-virus programs at VirusTotal detected the svchosa.exe file. That's a 84% detection rate.
| Scanner | Detection Name |
|---|---|
| Ad-Aware | DeepScan:Generic.Malware.SPVPkTkWk.759D439D |
| AegisLab | Trojan.Win32.Generic.4!c |
| AhnLab-V3 | Trojan/Win32.CoinMiner.R263356 |
| Alibaba | Backdoor:Win32/CoinMiner.1a319b5a |
| ALYac | DeepScan:Generic.Malware.SPVPkTkWk.759D439D |
| Antiy-AVL | Trojan/Win32.Skeeyah |
| APEX | Malicious |
| Arcabit | DeepScan:Generic.Malware.SPVPkTkWk.759D439D |
| Avast | Win32:Trojan-gen |
| AVG | Win32:Trojan-gen |
| Avira | TR/Downloader.Gen4 |
| BitDefender | DeepScan:Generic.Malware.SPVPkTkWk.759D439D |
| CAT-QuickHeal | Backdoor.Generic |
| ClamAV | Win.Trojan.Generic-6305873-0 |
| Comodo | TrojWare.Win32.Dialer.AFXP@4pjm0a |
| CrowdStrike | win/malicious_confidence_90% (W) |
| Cybereason | malicious.201ebb |
| Cylance | Unsafe |
| Cyren | W32/KillAV.AU.gen!Eldorado |
| DrWeb | Trojan.DnsChange.15856 |
| eGambit | Trojan.Generic |
| Emsisoft | DeepScan:Generic.Malware.SPVPkTkWk.759D439D (B) |
| Endgame | malicious (high confidence) |
| ESET-NOD32 | a variant of Win32/CoinMiner.BWP |
| F-Prot | W32/KillAV.AU.gen!Eldorado |
| F-Secure | Trojan.TR/Downloader.Gen4 |
| FireEye | Generic.mg.6451e14201ebb8bd |
| Fortinet | W32/CoinMiner.BWP!tr |
| GData | DeepScan:Generic.Malware.SPVPkTkWk.759D439D |
| Ikarus | Trojan.Win32.CoinMiner |
| Invincea | heuristic |
| Jiangmin | Backdoor.Generic.aupc |
| K7AntiVirus | Trojan ( 00549a851 ) |
| K7GW | Trojan ( 00549a851 ) |
| Kaspersky | HEUR:Backdoor.Win32.Generic |
| Malwarebytes | Trojan.BitCoinMiner |
| MAX | malware (ai score=100) |
| MaxSecure | Trojan.Malware.1728101.susgen |
| McAfee | GenericRXHF-GW!6451E14201EB |
| McAfee-GW-Edition | BehavesLike.Win32.PUPXAJ.cc |
| Microsoft | Trojan:Win32/Skeeyah.A!rfn |
| MicroWorld-eScan | DeepScan:Generic.Malware.SPVPkTkWk.759D439D |
| NANO-Antivirus | Trojan.Win32.CoinMiner.fofjdt |
| Paloalto | generic.ml |
| Panda | Trj/CI.A |
| Qihoo-360 | HEUR/QVM07.1.7D37.Malware.Gen |
| Rising | Backdoor.Farfli!1.64B3 (CLASSIC) |
| SentinelOne | DFI - Suspicious PE |
| Sophos | Mal/Generic-S |
| Symantec | Trojan.Gen.MBT |
| Tencent | Win32.Trojan.Killav.Wncj |
| TheHacker | Trojan/CoinMiner.bwp |
| TrendMicro | Coinminer.Win32.MALXMR.SMDD |
| TrendMicro-HouseCall | Coinminer.Win32.MALXMR.SMDD |
| VBA32 | BScope.Trojan.IRCbot |
| VIPRE | BehavesLike.Win32.Malware.eah (mx-v) |
| ViRobot | Trojan.Win32.Z.Coinminer.917504.H |
| Webroot | W32.Trojan.Gen |
| Yandex | Trojan.CoinMiner!szvNFyYyOVE |
| Zillya | Trojan.CoinMiner.Win32.21757 |
| ZoneAlarm | HEUR:Backdoor.Win32.Generic |
Sandbox Report
The following information was gathered by executing the file inside Cuckoo Sandbox.
Summary
Successfully executed process in sandbox.
Summary
{
"connects_ip": [
"47.104.110.131",
"192.168.56.1"
],
"file_created": [
"C:\\$dtrln\\umkbh.exe"
],
"file_recreated": [
"\\??\\Nsi"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}\\DhcpNameServer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Run\\XPWIN7",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}\\NameServer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\xy3602",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}\\DhcpNameServer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}\\NameServer"
],
"dll_loaded": [
"C:\\Windows\\system32\\pnrpnsp.dll",
"C:\\Windows\\syswow64\\dbghelp.dll",
"kernel32",
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"api-ms-win-core-sysinfo-l1-2-1",
"api-ms-win-core-localization-l1-2-1",
"DNSAPI.dll",
"kernel32.dll",
"C:\\Windows\\system32\\IMM32.DLL",
"KERNEL32.dll",
"C:\\Windows\\system32\\napinsp.dll",
"api-ms-win-core-synch-l1-2-0",
"ntmarta.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"WININET.dll",
"KERNEL32.DLL",
"RASMAN.DLL",
"ole32.dll",
"USER32.dll",
"gdi32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"rtutils.dll",
"IPHLPAPI.DLL",
"wininet.dll",
"C:\\Windows\\system32\\Winsta.dll",
"OLEAUT32.dll",
"C:\\Windows\\System32\\mswsock.dll",
"DHCPCSVC.DLL",
"RPCRT4.dll",
"dnsapi.dll",
"C:\\Windows\\System32\\winrnr.dll",
"C:\\Windows\\system32\\NLAapi.dll",
"api-ms-win-core-fibers-l1-1-1",
"C:\\Windows\\SysWOW64\\oleaut32.dll",
"ADVAPI32.dll",
"rpcrt4.dll",
"WS2_32.dll"
],
"file_opened": [
"C:\\ProgramData\\Application Data",
"C:\\Windows\\System32\\wshqos.dll",
"C:\\$dtrln\\umkbh.exe",
"\\Device\\NamedPipe",
"C:\\ProgramData",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\$dtrln",
"C:\\ProgramData\\Desktop",
"C:\\Windows\\System32\\wbem\\en-US\\wmiutils.dll.mui",
"C:\\ProgramData\\Microsoft",
"C:\\ProgramData\\Templates",
"C:\\ProgramData\\Start Menu",
"C:\\ProgramData\\",
"C:\\$dtrln\\",
"C:\\ProgramData\\Documents",
"\\Device\\NamedPipe\\",
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui",
"C:\\ProgramData\\Favorites",
"C:\\Windows\\System32\\wship6.dll"
],
"file_read": [
"C:\\$dtrln\\umkbh.exe"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc",
"HKEY_CURRENT_USER\\Software\\RealVNC\\vncviewer\\",
"HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Connections",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Associations",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Interfaces\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Wpad",
"HKEY_CURRENT_USER\\SOFTWARE\\RealVNC\\vncviewer\\",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}",
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows Defender",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}"
],
"resolves_host": [
"47.104.110.131",
"wpad",
"cuckpc"
],
"file_written": [
"C:\\$dtrln\\umkbh.exe"
],
"file_deleted": [
"C:\\$dtrln\\umkbh.exe",
"C:\\Windows\\SysWOW64\\rserver30\\Radm_log.htm"
],
"file_exists": [
"C:\\$dtrln\\umkbh.exe",
"C:\\ProgramData",
"C:\\$dtrln",
"C:\\$dtrln\\vjkyg.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\ProgramData\\svchostlong.exe"
],
"mutex": [
"IESQMMUTEX_0_208",
"C:\\$dtrln\\umkbh.exe",
"44f3Gk4zcTvR4e8PTaYEEpJfhj8FpvnxbHADmAiiQFLeMTAzvN1Xavn3VHHNP8n4ob3WJ77KbzcQaCgGYSofCwpSQQkCW9G",
"stratum+tcp:\/\/mine.c3pool.com:80",
"Gkhjkl Nonkrstu Wxy$udzyw"
],
"fetches_url": [
"http:\/\/m9f.oss-cn-beijing.aliyuncs.com\/SMB445.exe"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"cmd.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{eb87e1bd-3233-11d2-aec9-00c04fb68820}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{dcb00000-570f-4a9b-8d69-199fdba5723b}",
"{eb87e1bc-3233-11d2-aec9-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dcb00c01-570f-4a9b-8d69-199fdba5723b}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"command_line": [
"cmd \/c taskkill \/f \/im cmd.exe",
"cmd \/c ipconfig \/flushdns",
"ipconfig \/flushdns",
"C:\\$dtrln\\umkbh.exe -o stratum+tcp:\/\/mine.c3pool.com:80 -u 44f3Gk4zcTvR4e8PTaYEEpJfhj8FpvnxbHADmAiiQFLeMTAzvN1Xavn3VHHNP8n4ob3WJ77KbzcQaCgGYSofCwpSQQkCW9G -p x --max-cpu-usage=45 -K",
"taskkill \/f \/im cmd.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{9556DC99-828C-11CF-A37E-00AA003240C7}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\PreferredUILanguages",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\InprocServer32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\ProgramData",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Terminal Server\\TSAppCompat",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoProxyDetectType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\LoadAppInit_DLLs",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\MuiCached\\MachinePreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{027947E1-D731-11CE-A357-000000000001}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{D4781CD6-E5D3-44DF-AD94-930EFE48A887}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Terminal Server\\TSUserEnabled",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging"
],
"directory_enumerated": [
"C:\\Python27\\taskkill.*",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Windows\\System32\\ras\\*.pbk",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\taskkill",
"C:\\Users\\cuck\\AppData",
"C:\\Python27\\Scripts\\ipconfig",
"C:\\Users",
"C:\\Python27\\ipconfig.*",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Python27\\ipconfig",
"C:\\Windows\\System32\\taskkill.*",
"C:\\Python27\\Scripts\\taskkill",
"C:\\Users\\cuck",
"C:\\Python27\\Scripts\\taskkill.*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\ipconfig",
"C:\\Windows\\System32\\ipconfig.exe",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\ipconfig.*",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Python27\\Scripts\\ipconfig.*",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\taskkill.*",
"C:\\Windows\\System32\\ipconfig.COM",
"C:\\Windows\\System32\\taskkill.COM",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Python27\\taskkill",
"C:\\Windows\\System32\\ipconfig.*",
"C:\\Windows\\System32\\taskkill.exe"
],
"directory_created": [
"C:\\$dtrln"
]
}Dropped
[
{
"yara": [],
"sha1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"name": "cdfc1fb96be69a07_umkbh.exe",
"type": "empty",
"sha256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"urls": [],
"crc32": "00000000",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/868\/files\/cdfc1fb96be69a07_umkbh.exe",
"ssdeep": null,
"size": 0,
"sha512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5715dc83f4a921d36ce9ce47d0d13c5d85f2b0ff8318d2877eec2f63b931bd47417a81a538327af927da3e",
"md5": "d41d8cd98f00b204e9800998ecf8427e"
},
{
"yara": [],
"sha1": "542ceb6d4488c241f0a04e49c8cfd72a27ffbaab",
"name": "883660368307a018_umkbh.exe",
"filepath": "C:\\$dtrln\\umkbh.exe",
"type": "data",
"sha256": "883660368307a018b46db2ecb237e555da18749bf6695e515e50bc8658bbd417",
"urls": [],
"crc32": "9494A95D",
"path": "\/home\/hpuser\/.cuckoo\/storage\/analyses\/868\/files\/883660368307a018_umkbh.exe",
"ssdeep": null,
"size": 396800,
"sha512": "8c0c90fd577d1fcd9de7307b9e3ef1756903750369c4c7e6cee0133ab845daa73395cb074c62b80677159596c08018a0c5eaacaa8fb1e8ce2428fea66b3c00fc",
"pids": [
2308
],
"md5": "afc85fbe5c6efd3230f43bd955837071"
}
]Generic
[
{
"process_path": "C:\\$dtrln\\umkbh.exe",
"process_name": "umkbh.exe",
"pid": 2272,
"summary": {
"file_opened": [
"C:\\Windows\\System32\\wshqos.dll",
"C:\\Windows\\System32\\wship6.dll"
],
"mutex": [
"C:\\$dtrln\\umkbh.exe",
"44f3Gk4zcTvR4e8PTaYEEpJfhj8FpvnxbHADmAiiQFLeMTAzvN1Xavn3VHHNP8n4ob3WJ77KbzcQaCgGYSofCwpSQQkCW9G",
"stratum+tcp:\/\/mine.c3pool.com:80"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\MuiCached\\MachinePreferredUILanguages",
"HKEY_CURRENT_USER\\Control Panel\\Desktop\\PreferredUILanguages",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain"
],
"dll_loaded": [
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"C:\\Windows\\system32\\NLAapi.dll",
"kernel32",
"IPHLPAPI.DLL",
"C:\\Windows\\System32\\winrnr.dll",
"C:\\Windows\\System32\\mswsock.dll",
"api-ms-win-core-fibers-l1-1-1",
"api-ms-win-core-localization-l1-2-1",
"api-ms-win-core-sysinfo-l1-2-1",
"DNSAPI.dll",
"KERNEL32.DLL",
"USER32.dll",
"C:\\Windows\\system32\\pnrpnsp.dll",
"ADVAPI32.dll",
"C:\\Windows\\system32\\napinsp.dll",
"WS2_32.dll",
"api-ms-win-core-synch-l1-2-0"
]
},
"first_seen": 1562529263.8586,
"ppid": 2308
},
{
"process_path": "C:\\Users\\cuck\\AppData\\Local\\Temp\\7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16.bin",
"process_name": "7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16.bin",
"pid": 2308,
"summary": {
"connects_ip": [
"47.104.110.131",
"192.168.56.1"
],
"file_created": [
"C:\\$dtrln\\umkbh.exe"
],
"file_recreated": [
"\\??\\Nsi"
],
"regkey_written": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}\\DhcpNameServer",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Run\\XPWIN7",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}\\NameServer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\xy3602",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}\\DhcpNameServer",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}\\NameServer"
],
"dll_loaded": [
"C:\\Windows\\system32\\pnrpnsp.dll",
"C:\\Windows\\syswow64\\dbghelp.dll",
"API-MS-Win-Security-LSALookup-L1-1-0.dll",
"gdi32.dll",
"DNSAPI.dll",
"kernel32.dll",
"C:\\Windows\\system32\\IMM32.DLL",
"C:\\Windows\\system32\\napinsp.dll",
"ntmarta.dll",
"API-MS-WIN-Service-Management-L1-1-0.dll",
"WININET.dll",
"API-MS-WIN-Service-winsvc-L1-1-0.dll",
"ole32.dll",
"USER32.dll",
"API-MS-Win-Security-SDDL-L1-1-0.dll",
"RASMAN.DLL",
"rtutils.dll",
"IPHLPAPI.DLL",
"wininet.dll",
"OLEAUT32.dll",
"C:\\Windows\\System32\\mswsock.dll",
"DHCPCSVC.DLL",
"dnsapi.dll",
"C:\\Windows\\System32\\winrnr.dll",
"C:\\Windows\\system32\\NLAapi.dll",
"KERNEL32.dll",
"C:\\Windows\\SysWOW64\\oleaut32.dll",
"ADVAPI32.dll",
"WS2_32.dll"
],
"file_opened": [
"C:\\ProgramData\\Application Data",
"C:\\$dtrln\\umkbh.exe",
"\\Device\\NamedPipe",
"C:\\ProgramData",
"C:\\",
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls",
"C:\\$dtrln",
"C:\\ProgramData\\Desktop",
"C:\\ProgramData\\Microsoft",
"C:\\ProgramData\\Templates",
"C:\\ProgramData\\Start Menu",
"C:\\ProgramData\\",
"C:\\$dtrln\\",
"C:\\ProgramData\\Documents",
"\\Device\\NamedPipe\\",
"C:\\ProgramData\\Favorites"
],
"file_read": [
"C:\\$dtrln\\umkbh.exe"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Wpad",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}",
"HKEY_CURRENT_USER\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{AEFD33F3-CC73-4821-AD44-6915063E7FB1}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows Defender",
"HKEY_CURRENT_USER\\SOFTWARE\\RealVNC\\vncviewer\\",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}",
"HKEY_CURRENT_USER\\Software\\RealVNC\\vncviewer\\",
"HKEY_CURRENT_USER\\Software\\Microsoft\\windows\\CurrentVersion\\Internet Settings\\Connections",
"HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\Tcpip\\Parameters\\Interfaces\\",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Associations",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Interfaces\\{EF381EA0-4D07-418D-A490-68AF67CE948B}"
],
"resolves_host": [
"47.104.110.131",
"wpad",
"cuckpc"
],
"file_written": [
"C:\\$dtrln\\umkbh.exe"
],
"file_deleted": [
"C:\\$dtrln\\umkbh.exe",
"C:\\Windows\\SysWOW64\\rserver30\\Radm_log.htm"
],
"file_exists": [
"C:\\$dtrln",
"C:\\$dtrln\\vjkyg.exe",
"C:\\ProgramData",
"C:\\$dtrln\\umkbh.exe",
"C:\\ProgramData\\svchostlong.exe"
],
"mutex": [
"IESQMMUTEX_0_208",
"Gkhjkl Nonkrstu Wxy$udzyw"
],
"fetches_url": [
"http:\/\/m9f.oss-cn-beijing.aliyuncs.com\/SMB445.exe"
],
"guid": [
"{dcb00c01-570f-4a9b-8d69-199fdba5723b}",
"{a47979d2-c419-11d9-a5b4-001185ad2b89}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{d0074ffd-570f-4a9b-8d69-199fdba5723b}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dcb00000-570f-4a9b-8d69-199fdba5723b}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"command_line": [
"cmd \/c taskkill \/f \/im cmd.exe",
"cmd \/c ipconfig \/flushdns",
"C:\\$dtrln\\umkbh.exe -o stratum+tcp:\/\/mine.c3pool.com:80 -u 44f3Gk4zcTvR4e8PTaYEEpJfhj8FpvnxbHADmAiiQFLeMTAzvN1Xavn3VHHNP8n4ob3WJ77KbzcQaCgGYSofCwpSQQkCW9G -p x --max-cpu-usage=45 -K"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{9556DC99-828C-11CF-A37E-00AA003240C7}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{26656EAA-54EB-4E6F-8F85-4F0EF901A406}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseHostnameAsAlias",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\EnableConsoleTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\User Shell Folders\\AppData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\crypt32\\DebugHeapFlags",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\ProgramData",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{BCD1DE7E-2DB1-418B-B047-4A74E101F8C1}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Terminal Server\\TSAppCompat",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{8A40A45D-055C-4B62-ABD7-6D613E2CEAEC}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\FileTracingMask",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\AutoProxyDetectType",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{2A1C9EB2-DF62-4154-B800-63278FCB8037}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{1B1CAD8C-2DAB-11D2-B604-00104B703EFD}\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\UseOldHostResolutionOrder",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\InprocServer32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\InprocServer32\\ThreadingModel",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\DisableImprovedZoneCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileTracingMask",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Lsa\\AccessProviders\\MartaExtension",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\FileDirectory",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\LDAP\\LdapClientIntegrity",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{027947E1-D731-11CE-A357-000000000001}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{D4781CD6-E5D3-44DF-AD94-930EFE48A887}\\ProxyStubClsid32\\(Default)",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Connections\\DefaultConnectionSettings",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\EnableFileTracing",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{D68AF00A-29CB-43FA-8504-CE99A996D9EA}\\InprocServer32\\InprocServer32",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{55272A00-42CB-11CE-8135-00AA004BB851}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProfileList\\S-1-5-21-699399860-4089948139-3198924279-1001\\ProfileImagePath",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows NT\\CurrentVersion\\Windows\\LoadAppInit_DLLs",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASMANCS\\MaxFileSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Terminal Server\\TSUserEnabled",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Policies\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Security_HKLM_only",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Tracing\\RASAPI32\\ConsoleTracingMask",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\CLSID\\{B196B286-BAB4-101A-B69C-00AA00341D07}\\(Default)"
],
"directory_enumerated": [
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\rasphone.pbk",
"C:\\Windows\\System32\\ras\\*.pbk",
"C:\\ProgramData\\Microsoft\\Network\\Connections\\Pbk\\*.pbk",
"C:\\Users\\cuck\\AppData\\Roaming\\Microsoft\\Network\\Connections\\Pbk\\*.pbk"
],
"directory_created": [
"C:\\$dtrln"
]
},
"first_seen": 1562529186.7969,
"ppid": 3040
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 3016,
"summary": {
"dll_loaded": [
"kernel32.dll"
],
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"command_line": [
"ipconfig \/flushdns"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar"
],
"directory_enumerated": [
"C:\\Windows\\System32\\ipconfig.*",
"C:\\Users\\cuck\\AppData",
"C:\\Windows\\System32\\ipconfig.exe",
"C:\\Python27\\ipconfig",
"C:\\Windows\\System32\\ipconfig.COM",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Users\\cuck",
"C:\\Python27\\Scripts\\ipconfig",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\ipconfig",
"C:\\Users",
"C:\\Python27\\ipconfig.*",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\ipconfig.*",
"C:\\Users\\cuck\\AppData\\Local",
"C:\\Python27\\Scripts\\ipconfig.*"
]
},
"first_seen": 1562529187.3125,
"ppid": 2308
},
{
"process_path": "C:\\Windows\\SysWOW64\\taskkill.exe",
"process_name": "taskkill.exe",
"pid": 2268,
"summary": {
"dll_loaded": [
"C:\\Windows\\system32\\Winsta.dll",
"OLEAUT32.dll"
],
"file_opened": [
"C:\\Windows\\System32\\wbem\\en-US\\wmiutils.dll.mui",
"C:\\Windows\\SysWOW64\\en-US\\KERNELBASE.dll.mui"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32",
"HKEY_CURRENT_USER\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}",
"HKEY_CURRENT_USER\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\WBEM\\CIMOM",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32"
],
"wmi_query": [
"SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"cmd.exe\")"
],
"guid": [
"{4590f812-1d3a-11d0-891f-00aa004b2e24}",
"{00000003-0000-0000-c000-000000000046}",
"{eb87e1bd-3233-11d2-aec9-00c04fb68820}",
"{4590f811-1d3a-11d0-891f-00aa004b2e24}",
"{44aca674-e8fc-11d0-a07c-00c04fb68820}",
"{eb87e1bc-3233-11d2-aec9-00c04fb68820}",
"{674b6698-ee92-11d0-ad71-00c04fd8fdff}",
"{8bc3f05e-d86b-11d0-a075-00c04fb68820}",
"{7c857801-7381-11cf-884d-00aa004b2e24}",
"{d5f569d0-593b-101a-b569-08002b2dbf7a}",
"{f309ad18-d86a-11d0-a075-00c04fb68820}",
"{dc12a687-737f-11cf-884d-00aa004b2e24}"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\EnableObjectValidation",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Domain",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{423EC01E-2E35-11D2-B604-00104B703EFD}\\ProxyStubClsid32\\(Default)",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\services\\Tcpip\\Parameters\\Hostname",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\WBEM\\CIMOM\\Logging",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Classes\\Wow6432Node\\Interface\\{1C1C45EE-4395-11D2-B60B-00104B703EFD}\\ProxyStubClsid32\\(Default)"
]
},
"first_seen": 1562529187.5781,
"ppid": 300
},
{
"process_path": "C:\\Windows\\SysWOW64\\ipconfig.exe",
"process_name": "ipconfig.exe",
"pid": 2252,
"summary": {
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Rpc",
"HKEY_LOCAL_MACHINE\\Software\\Policies\\Microsoft\\Windows NT\\Rpc"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Rpc\\MaxRpcSize",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\SystemSetupInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\GRE_Initialize\\DisableMetaFiles",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\SQMClient\\Windows\\CEIPEnable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\Windows Error Reporting\\WMR\\Disable",
"HKEY_LOCAL_MACHINE\\SYSTEM\\Setup\\OOBEInProgress",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\ComputerName\\ActiveComputerName\\ComputerName"
],
"dll_loaded": [
"RPCRT4.dll",
"kernel32.dll",
"rpcrt4.dll"
]
},
"first_seen": 1562529187.4844,
"ppid": 3016
},
{
"process_path": "C:\\Windows\\SysWOW64\\cmd.exe",
"process_name": "cmd.exe",
"pid": 300,
"summary": {
"dll_loaded": [
"kernel32.dll"
],
"file_opened": [
"C:\\Windows\\Globalization\\Sorting\\sortdefault.nls"
],
"regkey_opened": [
"HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor",
"HKEY_LOCAL_MACHINE\\Software\\Microsoft\\Command Processor"
],
"file_exists": [
"C:\\Users\\cuck\\AppData\\Local\\Temp"
],
"command_line": [
"taskkill \/f \/im cmd.exe"
],
"regkey_read": [
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\AutoRun",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\CompletionChar",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\EnableExtensions",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\CustomLocale\\en-US",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Locale\\00000409",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\Language Groups\\1",
"HKEY_LOCAL_MACHINE\\SYSTEM\\ControlSet001\\Control\\Nls\\ExtendedLocale\\en-US",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\PathCompletionChar",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\DisableUNCCheck",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DelayedExpansion",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\AutoRun",
"HKEY_CURRENT_USER\\Software\\Microsoft\\Command Processor\\DefaultColor",
"HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Command Processor\\CompletionChar"
],
"directory_enumerated": [
"C:\\Python27\\Scripts\\taskkill.*",
"C:\\Users\\cuck\\AppData",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\taskkill.*",
"C:\\Python27\\taskkill.*",
"C:\\Python27\\Scripts\\taskkill",
"C:\\Users\\cuck\\AppData\\Local\\Temp",
"C:\\Windows\\System32\\taskkill.COM",
"C:\\Users\\cuck",
"C:\\Windows\\System32\\taskkill.exe",
"C:\\Windows\\System32\\taskkill.*",
"C:\\Users",
"C:\\Python27\\taskkill",
"C:\\Users\\cuck\\AppData\\Local\\Temp\\taskkill",
"C:\\Users\\cuck\\AppData\\Local"
]
},
"first_seen": 1562529187.3281,
"ppid": 2308
},
{
"process_path": "C:\\Windows\\System32\\lsass.exe",
"process_name": "lsass.exe",
"pid": 476,
"summary": {},
"first_seen": 1562529186.5781,
"ppid": 376
}
]Signatures
[
{
"markcount": 3,
"families": [],
"description": "Queries for the computername",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1562529192.0469,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1706
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1562529192.0939,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 2089
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "GetComputerNameW",
"return_value": 1,
"arguments": {
"computer_name": "CUCKPC"
},
"time": 1562529187.6871,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 69
}
],
"references": [],
"name": "antivm_queries_computername"
},
{
"markcount": 4,
"families": [],
"description": "Command line console output was observed",
"severity": 1,
"marks": [
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "\r\nWindows IP Configuration\r\n\r\n",
"console_handle": "0x00000007"
},
"time": 1562529187.5474,
"tid": 2184,
"flags": {}
},
"pid": 2252,
"type": "call",
"cid": 32
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "Successfully flushed the DNS Resolver Cache.\r\n",
"console_handle": "0x00000007"
},
"time": 1562529187.5474,
"tid": 2184,
"flags": {}
},
"pid": 2252,
"type": "call",
"cid": 64
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "SUCCESS: The process \"cmd.exe\" with PID 1692 has been terminated.\n",
"console_handle": "0x00000007"
},
"time": 1562529187.7971,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 243
},
{
"call": {
"category": "misc",
"status": 1,
"stacktrace": [],
"api": "WriteConsoleW",
"return_value": 1,
"arguments": {
"buffer": "SUCCESS: The process \"cmd.exe\" with PID 300 has been terminated.\n",
"console_handle": "0x00000007"
},
"time": 1562529187.7971,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 259
}
],
"references": [],
"name": "console_output"
},
{
"markcount": 1,
"families": [],
"description": "Checks amount of memory in system, this can be used to detect virtual machines that have a low amount of memory available",
"severity": 1,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "GlobalMemoryStatusEx",
"return_value": 1,
"arguments": {},
"time": 1562529187.5474,
"tid": 2184,
"flags": {}
},
"pid": 2252,
"type": "call",
"cid": 51
}
],
"references": [],
"name": "antivm_memory_available"
},
{
"markcount": 1,
"families": [],
"description": "The executable uses a known packer",
"severity": 1,
"marks": [
{
"category": "packer",
"ioc": "Armadillo v1.71",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "peid_packer"
},
{
"markcount": 2,
"families": [],
"description": "The file contains an unknown PE resource name possibly indicative of a packer",
"severity": 1,
"marks": [
{
"category": "resource name",
"ioc": "X32",
"type": "ioc",
"description": null
},
{
"category": "resource name",
"ioc": "X64",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "pe_unknown_resource_name"
},
{
"markcount": 1,
"families": [],
"description": "Allocates read-write-execute memory (usually to unpack itself)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtAllocateVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2272,
"region_size": 65536,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 0,
"protection": 64,
"process_handle": "0xffffffffffffffff",
"allocation_type": 12288,
"base_address": "0x0000000002750000"
},
"time": 1562529264.3276,
"tid": 2804,
"flags": {
"protection": "PAGE_EXECUTE_READWRITE",
"allocation_type": "MEM_COMMIT|MEM_RESERVE"
}
},
"pid": 2272,
"type": "call",
"cid": 990
}
],
"references": [],
"name": "allocates_rwx"
},
{
"markcount": 1,
"families": [],
"description": "A process attempted to delay the analysis task.",
"severity": 2,
"marks": [
{
"type": "generic",
"description": "7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16.bin tried to sleep 512 seconds, actually delayed analysis time by 512 seconds"
}
],
"references": [],
"name": "antisandbox_sleep"
},
{
"markcount": 9,
"families": [],
"description": "Foreign language identified in PE resource",
"severity": 2,
"marks": [
{
"name": "X32",
"language": "LANG_CHINESE",
"offset": "0x0002b250",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00053c00"
},
{
"name": "X64",
"language": "LANG_CHINESE",
"offset": "0x0007ee50",
"filetype": "data",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00060e00"
},
{
"name": "RT_ICON",
"language": "LANG_CHINESE",
"offset": "0x000e0bb0",
"filetype": "GLS_BINARY_LSB_FIRST",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000468"
},
{
"name": "RT_ICON",
"language": "LANG_CHINESE",
"offset": "0x000e0bb0",
"filetype": "GLS_BINARY_LSB_FIRST",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000468"
},
{
"name": "RT_ICON",
"language": "LANG_CHINESE",
"offset": "0x000e0bb0",
"filetype": "GLS_BINARY_LSB_FIRST",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000468"
},
{
"name": "RT_ICON",
"language": "LANG_CHINESE",
"offset": "0x000e0bb0",
"filetype": "GLS_BINARY_LSB_FIRST",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000468"
},
{
"name": "RT_GROUP_ICON",
"language": "LANG_CHINESE",
"offset": "0x000e1018",
"filetype": "MS Windows icon resource - 2 icons, 16x16",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000022"
},
{
"name": "RT_GROUP_ICON",
"language": "LANG_CHINESE",
"offset": "0x000e1018",
"filetype": "MS Windows icon resource - 2 icons, 16x16",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000022"
},
{
"name": "RT_MANIFEST",
"language": "LANG_CHINESE",
"offset": "0x000e1040",
"filetype": "XML 1.0 document, ASCII text, with CRLF line terminators",
"sublanguage": "SUBLANG_CHINESE_SIMPLIFIED",
"type": "generic",
"size": "0x00000202"
}
],
"references": [],
"name": "origin_langid"
},
{
"markcount": 1,
"families": [],
"description": "Creates hidden or system file",
"severity": 2,
"marks": [
{
"call": {
"category": "file",
"status": 1,
"stacktrace": [],
"api": "NtCreateFile",
"return_value": 0,
"arguments": {
"create_disposition": 5,
"file_handle": "0x000003c8",
"filepath": "C:\\$dtrln\\umkbh.exe",
"desired_access": "0x40100080",
"file_attributes": 2,
"filepath_r": "\\??\\C:\\$dtrln\\umkbh.exe",
"create_options": 96,
"status_info": 2,
"share_access": 0
},
"time": 1562529202.2499,
"tid": 2828,
"flags": {
"create_disposition": "FILE_OVERWRITE_IF",
"desired_access": "FILE_READ_ATTRIBUTES|SYNCHRONIZE|GENERIC_WRITE",
"create_options": "FILE_NON_DIRECTORY_FILE|FILE_SYNCHRONOUS_IO_NONALERT",
"file_attributes": "FILE_ATTRIBUTE_HIDDEN",
"status_info": "FILE_CREATED",
"share_access": ""
}
},
"pid": 2308,
"type": "call",
"cid": 2548
}
],
"references": [],
"name": "creates_hidden_file"
},
{
"markcount": 2,
"families": [],
"description": "Creates a suspicious process",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "cmd \/c taskkill \/f \/im cmd.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im cmd.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "suspicious_process"
},
{
"markcount": 1,
"families": [],
"description": "Executes one or more WMI queries",
"severity": 2,
"marks": [
{
"category": "wmi",
"ioc": "SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime, ParentProcessId FROM Win32_Process WHERE ( Caption = \"cmd.exe\")",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "has_wmi"
},
{
"markcount": 10,
"families": [],
"description": "Searches running processes potentially to identify processes for sandbox evasion, code injection or memory dumping",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "mobsync.exe",
"snapshot_handle": "0x000003c8",
"process_identifier": 1636
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1624
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "python.exe",
"snapshot_handle": "0x000003c8",
"process_identifier": 1596
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1627
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "taskhost.exe",
"snapshot_handle": "0x000003c8",
"process_identifier": 3008
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1630
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16.bin",
"snapshot_handle": "0x000003c8",
"process_identifier": 2308
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1636
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "SearchFilterHost.exe",
"snapshot_handle": "0x000003c8",
"process_identifier": 2460
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1639
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "WmiPrvSE.exe",
"snapshot_handle": "0x000003c8",
"process_identifier": 2164
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1642
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -1073741772,
"api": "Process32NextW",
"return_value": 0,
"arguments": {
"process_name": "",
"snapshot_handle": "0x000003c8",
"process_identifier": 5242985
},
"time": 1562529192.0309,
"tid": 856,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1645
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "umkbh.exe",
"snapshot_handle": "0x000002f0",
"process_identifier": 2272
},
"time": 1562529266.2339,
"tid": 2828,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 814084
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "Process32NextW",
"return_value": 1,
"arguments": {
"process_name": "conhost.exe",
"snapshot_handle": "0x000002f0",
"process_identifier": 2484
},
"time": 1562529266.3279,
"tid": 2828,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 814089
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 18,
"nt_status": -1073741816,
"api": "Process32NextW",
"return_value": 0,
"arguments": {
"process_name": "",
"snapshot_handle": "0x000002f0",
"process_identifier": 6815854
},
"time": 1562529266.4219,
"tid": 2828,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 814094
}
],
"references": [],
"name": "injection_process_search"
},
{
"markcount": 1,
"families": [],
"description": "Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time)",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtProtectVirtualMemory",
"return_value": 0,
"arguments": {
"process_identifier": 2272,
"stack_dep_bypass": 0,
"stack_pivoted": 0,
"heap_dep_bypass": 1,
"length": 65536,
"protection": 32,
"process_handle": "0xffffffffffffffff",
"base_address": "0x0000000002750000"
},
"time": 1562529264.3436,
"tid": 2804,
"flags": {
"protection": "PAGE_EXECUTE_READ"
}
},
"pid": 2272,
"type": "call",
"cid": 991
}
],
"references": [],
"name": "protection_rx"
},
{
"markcount": 1,
"families": [],
"description": "Checks adapter addresses which can be used to detect virtual network interfaces",
"severity": 2,
"marks": [
{
"call": {
"category": "network",
"status": 0,
"stacktrace": [],
"last_error": 0,
"nt_status": -1073741772,
"api": "GetAdaptersAddresses",
"return_value": 111,
"arguments": {
"flags": 0,
"family": 0
},
"time": 1562529187.2339,
"tid": 2584,
"flags": {}
},
"pid": 2308,
"type": "call",
"cid": 1193
}
],
"references": [],
"name": "antivm_network_adapters"
},
{
"markcount": 2,
"families": [],
"description": "The binary likely contains encrypted or compressed data indicative of a packer",
"severity": 2,
"marks": [
{
"entropy": 7.9176820100193,
"section": {
"size_of_data": "0x000b7000",
"virtual_address": "0x0002b000",
"entropy": 7.9176820100193,
"name": ".rsrc",
"virtual_size": "0x000b6248"
},
"type": "generic",
"description": "A section with a high entropy has been found"
},
{
"entropy": 0.82062780269058,
"type": "generic",
"description": "Overall entropy of this PE file is high"
}
],
"references": [
"http:\/\/www.forensickb.com\/2013\/03\/file-entropy-explained.html",
"http:\/\/virii.es\/U\/Using%20Entropy%20Analysis%20to%20Find%20Encrypted%20and%20Packed%20Malware.pdf"
],
"name": "packer_entropy"
},
{
"markcount": 1,
"families": [],
"description": "Checks for the Locally Unique Identifier on the system for a suspicious privilege",
"severity": 2,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "LookupPrivilegeValueW",
"return_value": 1,
"arguments": {
"system_name": "",
"privilege_name": "SeDebugPrivilege"
},
"time": 1562529187.6871,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 50
}
],
"references": [],
"name": "privilege_luid_check"
},
{
"markcount": 1,
"families": [],
"description": "Expresses interest in specific running processes",
"severity": 2,
"marks": [
{
"category": "process",
"ioc": "umkbh.exe",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "process_interest"
},
{
"markcount": 4,
"families": [],
"description": "Terminates another process",
"severity": 2,
"marks": [
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 1168,
"nt_status": -1073741772,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000001",
"process_identifier": 1692,
"process_handle": "0x0000017c"
},
"time": 1562529187.7811,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 238
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000001",
"process_identifier": 1692,
"process_handle": "0x0000017c"
},
"time": 1562529187.7971,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 239
},
{
"call": {
"category": "process",
"status": 0,
"stacktrace": [],
"last_error": 1168,
"nt_status": -1072365560,
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000001",
"process_identifier": 300,
"process_handle": "0x0000017c"
},
"time": 1562529187.7971,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 254
},
{
"call": {
"category": "process",
"status": 1,
"stacktrace": [],
"api": "NtTerminateProcess",
"return_value": 0,
"arguments": {
"status_code": "0x00000001",
"process_identifier": 300,
"process_handle": "0x0000017c"
},
"time": 1562529187.7971,
"tid": 1996,
"flags": {}
},
"pid": 2268,
"type": "call",
"cid": 255
}
],
"references": [],
"name": "terminates_remote_process"
},
{
"markcount": 4,
"families": [],
"description": "Uses Windows utilities for basic Windows functionality",
"severity": 2,
"marks": [
{
"category": "cmdline",
"ioc": "cmd \/c taskkill \/f \/im cmd.exe",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "cmd \/c ipconfig \/flushdns",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "ipconfig \/flushdns",
"type": "ioc",
"description": null
},
{
"category": "cmdline",
"ioc": "taskkill \/f \/im cmd.exe",
"type": "ioc",
"description": null
}
],
"references": [
"http:\/\/blog.jpcert.or.jp\/2016\/01\/windows-commands-abused-by-attackers.html"
],
"name": "uses_windows_utilities"
},
{
"markcount": 1,
"families": [],
"description": "Looks for the Windows Idle Time to determine the uptime",
"severity": 3,
"marks": [
{
"call": {
"category": "system",
"status": 1,
"stacktrace": [],
"api": "NtQuerySystemInformation",
"return_value": 0,
"arguments": {
"information_class": 8
},
"time": 1562529187.0939,
"tid": 2588,
"flags": {
"information_class": "SystemProcessorPerformanceInformation"
}
},
"pid": 2308,
"type": "call",
"cid": 412
}
],
"references": [],
"name": "antisandbox_idletime"
},
{
"markcount": 2,
"families": [],
"description": "Installs itself for autorun at Windows startup",
"severity": 3,
"marks": [
{
"type": "generic",
"reg_key": "HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Microsoft\\Windows\\CurrentVersion\\Run\\XPWIN7",
"reg_value": "C:\\Users\\cuck\\AppData\\Local\\Temp\\7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16.bin"
},
{
"type": "generic",
"reg_key": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\xy3602",
"reg_value": "C:\\Users\\cuck\\AppData\\Local\\Temp\\7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16.bin"
}
],
"references": [],
"name": "persistence_autorun"
},
{
"markcount": 1,
"families": [],
"description": "A stratum cryptocurrency mining command was executed",
"severity": 3,
"marks": [
{
"category": "cmdline",
"ioc": "C:\\$dtrln\\umkbh.exe -o stratum+tcp:\/\/mine.c3pool.com:80 -u 44f3Gk4zcTvR4e8PTaYEEpJfhj8FpvnxbHADmAiiQFLeMTAzvN1Xavn3VHHNP8n4ob3WJ77KbzcQaCgGYSofCwpSQQkCW9G -p x --max-cpu-usage=45 -K",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "cryptomining_stratum_command"
},
{
"markcount": 5,
"families": [],
"description": "Sets or modifies WPAD proxy autoconfiguration file for traffic interception",
"severity": 3,
"marks": [
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x0000034c",
"value": 1,
"regkey_r": "WpadDecisionReason",
"reg_type": 4,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionReason"
},
"time": 1562529187.5619,
"tid": 2584,
"flags": {
"reg_type": "REG_DWORD"
}
},
"pid": 2308,
"type": "call",
"cid": 1437
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x0000034c",
"value": "\u00a0\u00ecG\u0091\u000b5\u00d5\u0001",
"regkey_r": "WpadDecisionTime",
"reg_type": 3,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecisionTime"
},
"time": 1562529187.5619,
"tid": 2584,
"flags": {
"reg_type": "REG_BINARY"
}
},
"pid": 2308,
"type": "call",
"cid": 1438
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExA",
"return_value": 0,
"arguments": {
"key_handle": "0x0000034c",
"value": 3,
"regkey_r": "WpadDecision",
"reg_type": 4,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadDecision"
},
"time": 1562529187.5619,
"tid": 2584,
"flags": {
"reg_type": "REG_DWORD"
}
},
"pid": 2308,
"type": "call",
"cid": 1439
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExW",
"return_value": 0,
"arguments": {
"key_handle": "0x0000034c",
"value": "Unidentified network",
"regkey_r": "WpadNetworkName",
"reg_type": 1,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}\\WpadNetworkName"
},
"time": 1562529187.5619,
"tid": 2584,
"flags": {
"reg_type": "REG_SZ"
}
},
"pid": 2308,
"type": "call",
"cid": 1440
},
{
"call": {
"category": "registry",
"status": 1,
"stacktrace": [],
"api": "RegSetValueExW",
"return_value": 0,
"arguments": {
"key_handle": "0x00000348",
"value": "{E34DF837-3A38-4E8C-83F4-ABF8AB3FB4A6}",
"regkey_r": "WpadLastNetwork",
"reg_type": 1,
"regkey": "HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Internet Settings\\Wpad\\WpadLastNetwork"
},
"time": 1562529187.5619,
"tid": 2584,
"flags": {
"reg_type": "REG_SZ"
}
},
"pid": 2308,
"type": "call",
"cid": 1508
}
],
"references": [],
"name": "modifies_proxy_wpad"
},
{
"markcount": 1,
"families": [],
"description": "Collects information on the system (ipconfig, netstat, systeminfo)",
"severity": 3,
"marks": [
{
"category": "cmdline",
"ioc": "cmd \/c ipconfig \/flushdns",
"type": "ioc",
"description": null
}
],
"references": [],
"name": "recon_systeminfo"
}
]Yara
The Yara rules did not detect anything in the file.
Network
{
"tls": [],
"udp": [
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 10572,
"time": 6.2244050502777,
"dport": 137,
"sport": 137
},
{
"src": "192.168.56.101",
"dst": "192.168.56.255",
"offset": 15252,
"time": 12.22492313385,
"dport": 138,
"sport": 138
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 17096,
"time": 5.5507199764252,
"dport": 5355,
"sport": 51001
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 17416,
"time": 4.15456199646,
"dport": 5355,
"sport": 53595
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 17744,
"time": 6.1583499908447,
"dport": 5355,
"sport": 53848
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 18072,
"time": 4.7802131175995,
"dport": 5355,
"sport": 54255
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 18400,
"time": 3.0487132072449,
"dport": 5355,
"sport": 55314
},
{
"src": "192.168.56.101",
"dst": "224.0.0.252",
"offset": 18728,
"time": 6.1656291484833,
"dport": 5355,
"sport": 55880
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 19056,
"time": 4.739687204361,
"dport": 1900,
"sport": 1900
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 38466,
"time": 4.1954321861267,
"dport": 3702,
"sport": 49152
},
{
"src": "192.168.56.101",
"dst": "239.255.255.250",
"offset": 46850,
"time": 6.2559361457825,
"dport": 1900,
"sport": 53598
}
],
"dns_servers": [],
"http": [],
"icmp": [],
"smtp": [],
"tcp": [],
"smtp_ex": [],
"mitm": [],
"hosts": [],
"pcap_sha256": "df7d0441f50503235d566395f1784e8c857ac29a6a37e5e049dab0840b13d0c6",
"dns": [],
"http_ex": [],
"domains": [],
"dead_hosts": [],
"sorted_pcap_sha256": "bed0a9b64aa6640af25e96a6596a9a6248d3da2596ccbe9152cf4f13e60939bd",
"irc": [],
"https_ex": []
}Screenshots
svchosa.exe removal instructions
The instructions below shows how to remove svchosa.exe with help from the FreeFixer removal tool. Basically, you install FreeFixer, scan your computer, check the svchosa.exe file for removal, restart your computer and scan it again to verify that svchosa.exe has been successfully removed. Here are the removal instructions in more detail:
- Download and install FreeFixer: http://www.freefixer.com/download.html
- When the scan is finished, locate svchosa.exe in the scan result and tick the checkbox next to the svchosa.exe file. Do not check any other file for removal unless you are 100% sure you want to delete it. Tip: Press CTRL-F to open up FreeFixer's search dialog to quickly locate svchosa.exe in the scan result.



 c:\downloads\svchosa.exe
c:\downloads\svchosa.exe 
- Restart your computer.
- Start FreeFixer and scan your computer again. If svchosa.exe still remains in the scan result, proceed with the next step. If svchosa.exe is gone from the scan result you're done.
- If svchosa.exe still remains in the scan result, check its checkbox again in the scan result and click Fix.
- Restart your computer.
- Start FreeFixer and scan your computer again. Verify that svchosa.exe no longer appear in the scan result.
Hashes [?]
| Property | Value |
|---|---|
| MD5 | 6451e14201ebb8bde9b7e9140a35701d |
| SHA256 | 7dc2f0fb5179bedf2676c3ef649e018b7af419ebb83a08d84ca22cdf7dbc3b16 |
Error Messages
These are some of the error messages that can appear related to svchosa.exe:
svchosa.exe has encountered a problem and needs to close. We are sorry for the inconvenience.
svchosa.exe - Application Error. The instruction at "0xXXXXXXXX" referenced memory at "0xXXXXXXXX". The memory could not be "read/written". Click on OK to terminate the program.
svchosa.exe has stopped working.
End Program - svchosa.exe. This program is not responding.
svchosa.exe is not a valid Win32 application.
svchosa.exe - Application Error. The application failed to initialize properly (0xXXXXXXXX). Click OK to terminate the application.
What will you do with svchosa.exe?
To help other users, please let us know what you will do with svchosa.exe:
Comments
Please share with the other users what you think about this file. What does this file do? Is it legitimate or something that your computer is better without? Do you know how it was installed on your system? Did you install it yourself or did it come bundled with some other software? Is it running smoothly or do you get some error message? Any information that will help to document this file is welcome. Thank you for your contributions.
I'm reading all new comments so don't hesitate to post a question about the file. If I don't have the answer perhaps another user can help you.
No comments posted yet.