Word Shark - 32% Detection Rate *
Did you just run into a download or a file on your computer that has been digitally signed by Word Shark? Some of the security products refers to the detected files as Adware.Vitruvian.Q and Adware.Plugin.1137. The detection rate for the Word Shark files collected here is 32%. Please read on for more details.
You will probably notice Word Shark when clicking to run the file. The publisher name shows up as the "Verified publisher" in the UAC dialog as the screenshot shows:
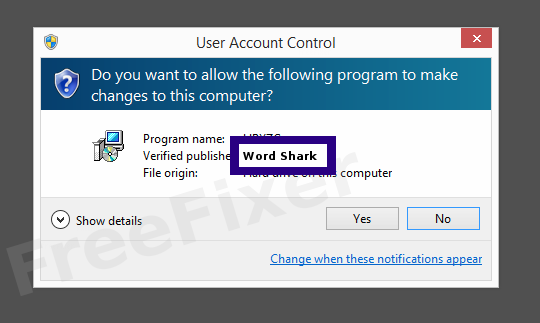
You can also view the Word Shark certificate with the following procedure:
- Open up Windows Explorer and locate the Word Shark file
- Right-click the file and select Properties
- Click the Digital Signatures tab
- Click on the View Certificate button
Here's a screenshot of a file that has been digitally signed by Word Shark:
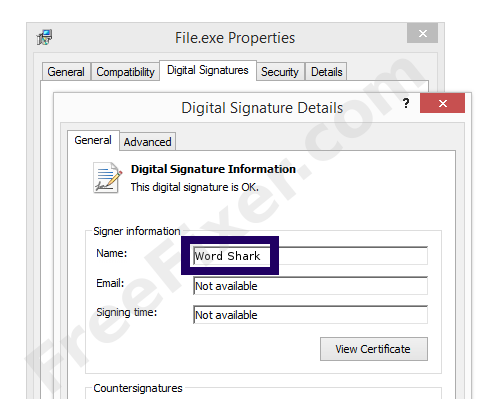
As you can see in the screenshot above, the Windows OS reports that "This digital signature is OK". This means that the file has been published by Word Shark and that the file has not been tampered with.
If you click the View Certificate button shown in the screengrab above, you can see all the details of the certificate, such as when it was issued, who issued the certificate, how long it is valid, etc. You can also see the address for Word Shark, such as the street name, city and country.
GlobalSign CodeSigning CA - G2 has issued the Word Shark certificates. You can also view the details of the issuer by clicking the View Certificate button shown in the screenshot above.
Word Shark Files
These are the Word Shark files I've collected, thanks to the FreeFixer users.
| Detection Ratio | File Name |
|---|---|
| 9/55 | wsfd_vw_1_10_0_20.sys |
| 10/57 | wssvc.exe |
| 18/56 | wssvc.exe |
| 12/55 | WordSharkAutoUpdateClient.exe |
| 12/56 | wsfd_vt_1_10_0_20.sys |
| 39/56 | wssvc.exe |
| 42/54 | wordshark-setup-1.10.0.20.exe |
Scanner and Detection Names
Here is the detection names for the Word Shark files. I've grouped the detection names by each scanner engine. Thanks to VirusTotal for the scan results.
| Scanner | Detection Names |
|---|---|
| AVG | Generic.1E9, Generic6.CEZF |
| AVware | Trojan.Win32.Generic!BT, InfoAtoms (fs), Vitruvian |
| Ad-Aware | Application.Generic.1451198, Adware.Vitruvian.Q |
| Agnitum | PUA.Vitruvian!, Riskware.NetTool! |
| AhnLab-V3 | PUP/Win32.Vitruvian |
| Antiy-AVL | GrayWare[AdWare]/MSIL.Vitruvian.a |
| Arcabit | PUP.Adware.WordShark, Trojan.Adware.Vitruvian.1 |
| Avast | Win32:Malware-gen, Win32:Vitruvian-B [PUP], Win32:PUP-gen [PUP] |
| Avira | ADWARE/Adware.Gen7, ADWARE/Plugin.58456, ADWARE/Plugin.317696 |
| Baidu-International | Hacktool.Win64.NetFilter.A, Adware.Win32.Vitruvian.F, Hacktool.Win32.NetFilter.A |
| BitDefender | Application.Generic.1451198, Adware.Vitruvian.Q |
| Bkav | W32.HfsAdware.A2E5 |
| CAT-QuickHeal | AdWare.Vitruvian.r5 (Not a Virus), AdWare.Vitruvian.g5 (Not a Virus) |
| Comodo | ApplicUnwnt |
| Cyren | W32/Vitruvian.QCVI-6923, W32/Adware.HPNC-4210 |
| DrWeb | Adware.Plugin.1137, Adware.Plugin.1011 |
| ESET-NOD32 | a variant of Win64/NetFilter.A potentially unsafe, a variant of Win32/Adware.Vitruvian.F, a variant of Win32/NetFilter.A potentially unsafe, a variant of MSIL/Adware.Vitruvian.A |
| Emsisoft | Adware.Vitruvian.Q (B) |
| F-Prot | W32/Vitruvian.A |
| F-Secure | Application.Generic.1451198, Adware.Vitruvian.Q |
| Fortinet | Adware/NetFilter, Riskware/Vitruvian, Adware/Vitruvian, Riskware/NetFilter |
| GData | Application.Generic.1451198, Adware.Vitruvian.Q |
| Ikarus | PUA.Vitruvian |
| Jiangmin | AdWare/Vitruvian.y, AdWare/Vitruvian.ad, AdWare/MSIL.juo |
| K7AntiVirus | Adware ( 004b8e1a1 ), Adware ( 004bbf601 ), Riskware ( 0040eff71 ) |
| K7GW | Adware ( 004b8e1a1 ), Adware ( 004bbf601 ), Riskware ( 0040eff71 ) |
| Kaspersky | not-a-virus:AdWare.Win32.Vitruvian.n, not-a-virus:AdWare.MSIL.Vitruvian.a, not-a-virus:AdWare.Win32.Vitruvian.o |
| Malwarebytes | PUP.Optional.WordShark.A, PUP.Optional.WordShark |
| McAfee | Artemis!452C1A01EE09, Artemis!9A7123A57B8D, Artemis!2A06DE988BC7, Artemis!DC2873B56986 |
| McAfee-GW-Edition | Artemis, Artemis!PUP, BehavesLike.Win32.Tool.tc |
| MicroWorld-eScan | Application.Generic.1451198, Adware.Vitruvian.Q |
| NANO-Antivirus | Riskware.Win32.Vitruvian.duugee, Riskware.Win32.Plugin.dxcgle |
| Panda | Generic Suspicious, Trj/CI.A, PUP/WordShark |
| Qihoo-360 | HEUR/QVM03.0.Malware.Gen, HEUR/QVM10.1.Malware.Gen, HEUR/QVM42.1.Malware.Gen |
| SUPERAntiSpyware | Adware.Plugin/Variant, PUP.WordShark/Variant, Adware.Virtuvian/Variant |
| Sophos | Troj/Agent-AODZ |
| Symantec | WS.Reputation.1, Trojan.Gen.2 |
| Tencent | Win32.Adware.Vitruvian.Palw, Msil.Adware.Vitruvian.Ecah, Win32.Adware.Vitruvian.Hpry, Msil.Adware.Vitruvian.Wrqe |
| TrendMicro | TROJ_GEN.R08NC0OGE15, TROJ_GEN.R0EBC0OGE15 |
| TrendMicro-HouseCall | Suspicious_GEN.F47V0611 |
| VBA32 | AdWare.Vitruvian, AdWare.MSIL.Vitruvian |
| VIPRE | Trojan.Win32.Generic!BT, InfoAtoms (fs), Vitruvian |
| ViRobot | Trojan.Win32.S.Agent.299096[h] |
| Zillya | Adware.Vitruvian.Win32.72, Adware.Vitruvian.Win32.87 |
| nProtect | Adware.Vitruvian.Q |
* How the Detection Percentage is Calculated
The detection percentage is based on the fact that I've gathered 446 scan reports for the Word Shark files. 142 of these scan reports came up with some sort of detection. If you like, you can view the full details of the scan results by examining the files listed above.
Analysis Details
The analysis is done on certificates with the following serial numbers:
- 112198eb233b90e5f1dcefa56d0bcf72b66c